
Google has announced that it is creating a security feature called Device Bound Session Credentials (DBSC) in open beta to help users be protected against session cookie theft attacks.
First introduced as a prototype in April 2024, DBSC is designed to combine authentication sessions into devices to prevent threat actors from using stolen cookies to sign in to the victim’s account and gain unauthorized access from another device under their control.
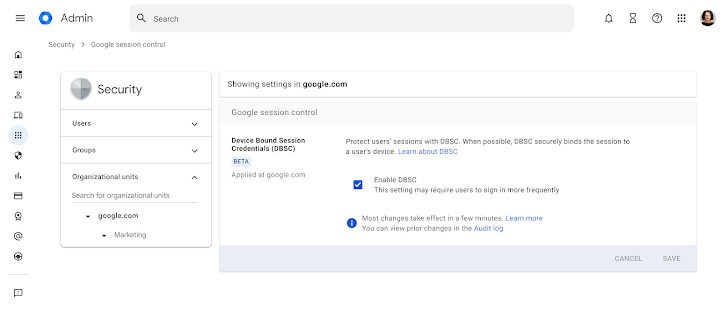
“DBSC, available in the Chrome browser on Windows, helps to enhance security after logging in and bind session cookies (small files used by websites that remember user information) to your device,” said Senior Director of Product Administrator at Google Workspace.
DBSC is not just about protecting user accounts after authentication. It will be much more difficult for bad actors to reuse session cookies and improve session integrity.

The company also notes that PassKey support is now available to more than 11 million Google Workspace customers in general, as well as expanding its admin controls to audit registrations and limit PassKey to physical security keys.
Finally, Google will use the OpenID standard to deploy a Shared Signal Framework (SSF) receiver in a closed beta for selected customers to allow for near-real-time exchange of critical security signals.
“This framework acts as a robust system for the ‘transmitters’ to quickly notify ‘receivers’ of critical events, facilitating a coordinated response to security threats,” Wen said.
“Beyond threat detection and response, signal sharing also allows for general sharing of various properties, such as devices and user information, further strengthening the overall security attitude and joint defense mechanism.”
Google Project Zero releases transparency report
The development comes as Google Project Zero, a security team within the company tasked with hunting for zero-day vulnerabilities, announced a new testing policy reporting transparency to address what is described as upstream patch gaps.
Typically, a patch gap refers to the period when a fix is released due to a vulnerability and the time it takes for users to install the appropriate update, while an upstream patch gap indicates the time pan for upstream vendors to take advantage of the fix, while downstream customers have not yet integrated the patch and shipped to end users.
To close this upstream patch app, Google said it is adding a new step that is intended to publicly share vulnerability discoveries within a week of reporting to relevant vendors.
This information is expected to include a vendor or open source project when the report, the affected products, the date the report was submitted, and the 90-day disclosure deadline expires. The current list includes two Microsoft Windows bugs, a flaw in Dolby Unified Decoder, and three issues: Google Bigwave.

“The main goal of this exam is to reduce the upstream patch gap by increasing transparency,” said Tim Willis of Project Zero. “We can better inform downstream dependents by providing an early signal that vulnerabilities are being reported upstream. For our small set of issues, there is an additional source of information to monitor issues that may affect users.”
Google further said it plans to apply this principle to Big Sleep. It is an artificial intelligence (AI) agent launched last year as part of a collaboration between DeepMind and Google Project Zero, which enhances vulnerability detection.
Search Behemoth also emphasized that technical details, proof of concept code, or other information that could “substantially support” will be released until the deadline.
With a modern approach, Google Project Zero said it hopes to drive needles by releasing patches to devices, systems and services that end users rely on timely, enhancing the overall security ecosystem.
Source link

