Threat actors actively harness the critical security flaws of “only – Charity’s multipurpose non-profit WordPress theme” to take over sensitive sites.
The CVSS score for vulnerabilities tracked as CVE-2025-5394 is 9.8. Security researcher Thái An is believed to have discovered and reported the bug.
According to WordFence, this drawback is related to any file upload that affects all versions of plugins prior to 7.8.3. Addressed in version 7.8.5, released on June 16, 2025.
CVE-2025-5394 “rooted in a plugin installation function named alion_import_pack_install_plugin() and derived from missing feature checks, so you can deploy any plugin from a remote source via Ajax and achieve code execution.
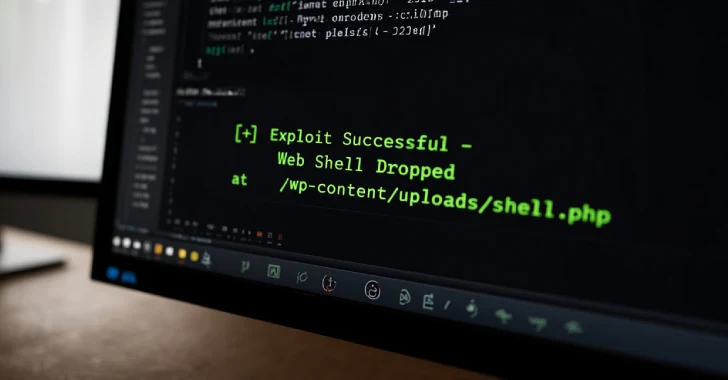
“This vulnerability allows an unauthorized attacker to upload arbitrary files to a vulnerable site and enable remote code execution. This is usually exploited for complete site takeover.”
Evidence shows that CVE-2025-5394 began being exploited on July 12, two days before the vulnerability was published. This indicates that the threat actors behind the campaign may be actively monitoring code changes for newly addressed vulnerabilities.

The company said it has already blocked 120,900 exploit attempts targeting defects. The activity originated from the following IP address –
193.84.71.24487.120.92.24146.19.213.8185.159.158.108188.215.235.94146 .70.10.2574.118.126.11162.133.47.18198.145.157.1022A0B: 4141:820:752 :: 2

The observed attacks have been averaged to upload a zip archive (“wp-classic-editor.zip” or “background-image-cropper.zip”) containing PHP-based backdoors. It also delivers a fully functional file manager and backdoor that allows you to create rogue administrator accounts.
To mitigate potential threats, WordPress site owners using themes are recommended to apply the latest updates, check for suspicious admin users, and scan the logs of requests.
Source link