Cybersecurity researchers have revealed details of a new phishing campaign that hides malicious payloads by bypassing defenses by abuse of link wrapping services from Proofpoint and Intermedia.
“Link Lapping is designed by vendors such as Proofpoint to protect users by routing all clicked URLs through the scanning service, allowing them to block known malicious destinations when clicked,” the CloudFlare Email Security team said.
“This is effective against known threats, but if the link wrapped when clicked is not flagged by the scanner, the attack can still be successful.”
The activities observed over the past two months have once again shown how threat actors can find different ways to leverage legitimate functions and reliable tools to carry out malicious actions.
It is worth noting that link wrapping exploitation involves gaining unauthorized access to email accounts that already use the feature within your organization.[.]com/v2/url? u =).

Another important aspect is about what CloudFlare calls “multitiaridirect abuse,” where threat actors first use URL shortening services like Bitly to obscure malicious links, and then Proofpoint sends the abbreviated link to an email message via the measured account, obscuring the second time.
This behavior effectively creates a redirect chain. This causes the URL to go through two levels of obfuscation (Bitly and ProofPoint URL defense) before being victimized to a phishing page.
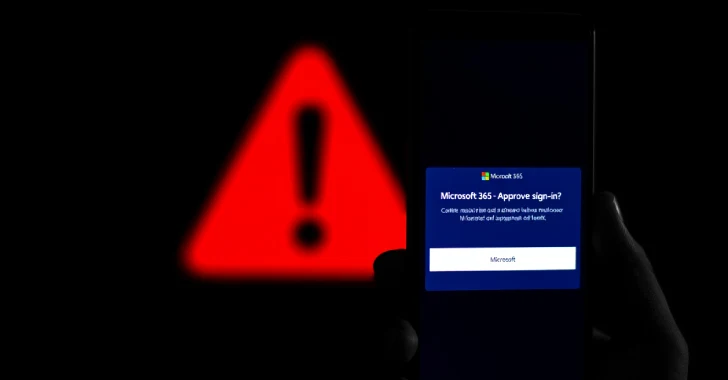
In the attacks observed by Web Infrastructure Company, phishing messages exaggerate voicemail notifications, urging recipients to click on the links to listen to them, and ultimately pointing them to a fake Microsoft 365 phishing page designed to capture qualifications.
Alternative Infection Chains employ the same technique in emails that notify users of expected documents received by Microsoft teams and trick them by clicking on hyperlinks trapped in Booby.
A third variation of these attacks claims that you can impersonate a team in email, have unread messages, and click the “Team Reply” button embedded in the message to redirect to the qualification harvest page.
“By covering malicious destinations with legal urldefense[.]Proof Point[.]com and url[.]Abuse of email protection URLs, trustworthy link wrapping services for these phishing campaigns significantly increases the chances of successful attacks,” said CloudFlare.
The development comes amid a surge in phishing attacks that weaponize scalable vector graphics (SVG) files to avoid traditional spam prevention and phishing protections and launch multi-stage malware infections.

“Unlike JPEG and PNG files, SVG files are written in XML and support JavaScript and HTML code,” said New Jersey Cybersecurity and Communications Integration Cell (NJCCIC) last month. “These can contain scripts, hyperlinks, and interactive elements. They can be exploited by embedding malicious code into harmless SVG files.”
Phishing campaigns have also been observed to embed fake Zoom video conferencing links in emails. When clicked, it triggers the redirect chain to a fake page that mimics a realistic-looking interface, then provides a “Chapter Connection Timing” message, which is brought to the phishing page and encourages you to qualify.
“Unfortunately, instead of ‘rejoining’, victim qualifications and IP addresses, countries and regions are extracted via Telegram, a messaging app well known for its ‘security and encrypted communications’ and inevitably sent to threat actors,” Cofense said in a recent report.
Source link