Cybersecurity researchers have disclosed multiple security flaws in video surveillance products from Axis Communications, which, if successfully exploited, can now take over the attack.
“This attack will have pre-certified remote code execution in Axis Device Manager, servers used to configure and manage camera fleets, and Axis camera stations for client software used to view camera feeds.”
“In addition, using Internet scanning of exposed axes, attackers can enumerate vulnerable servers and clients and carry out granular, highly targeted attacks.”

The list of identified defects is as follows:
CVE-2025-30023 (CVSS score: 9.0) – Fault in the communication protocol used between client and server. This could lead to authenticated users performing remote station execution attacks (camera manager 5.58, and device manager 5.32, and device manager 5.32) and could be used with the client score used for CVE-2025-30024 (CVSS score: 6.8). Performs intermediate (AITM) attack (fixed with device manager 5.32) CVE-2025-30025 (CVSS score: 4.8) – Defective Axis Camera Station Server Fault (fixed with Camera Station Pro 6.9 and Camera Station 5.58)

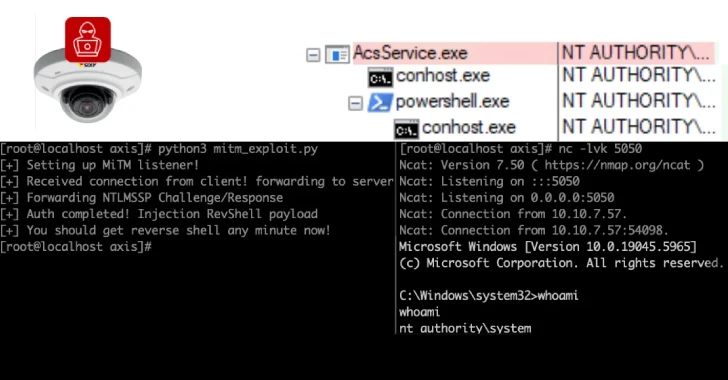
The successful exploitation of the aforementioned vulnerability allows an attacker to assume the AITM location between the camera station and its clients, effectively modifying requests/responses and performing any action on either the server or client system. There is no evidence that the problem was exploited in the wild.

Claroty said it found over 6,500 servers that expose their own axis.
“A successful exploit gives the attacker system-level access on the internal network and the ability to control each camera in a particular deployment,” Moshe said. “The feed can be hijacked, monitored, and/or shut down. Attackers can take advantage of these security issues to bypass authentication to the camera and obtain remote code execution before authentication on the device.”
Source link