Cybersecurity researchers are warning of a new campaign distributing the Astaroth banking Trojan that employs GitHub as the backbone of its operations to remain resilient in the face of infrastructure outages.
“Rather than relying solely on traditional command-and-control (C2) servers that can be taken down, these attackers are leveraging GitHub repositories to host their malware configurations,” McAfee Labs researchers Harshil Patel and Prabudh Chakravorty said in the report.
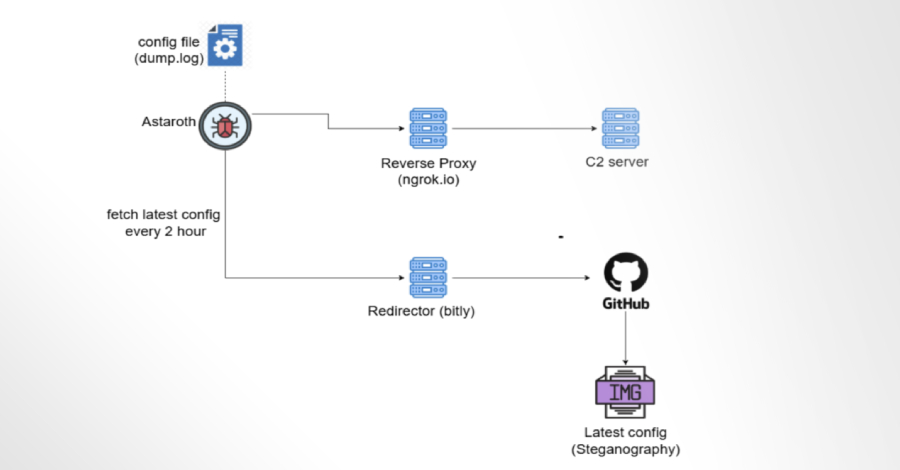
“Even if law enforcement or security researchers shut down the C2 infrastructure, Astaroth will continue to run simply by retrieving new configurations from GitHub.”
According to the cybersecurity firm, this activity is primarily focused on Brazil, but the banking malware is known to target various countries in Latin America, including Mexico, Uruguay, Argentina, Paraguay, Chile, Bolivia, Peru, Ecuador, Colombia, Venezuela, and Panama.

This is not the first time that Astaroth’s campaign has set its sights on Brazil. In July and October 2024, both Google and Trend Micro warned about threat clusters called PINEAPPLE and Water Makara that used phishing emails to distribute malware.
The latest attack chain is no different, starting with a DocuSign-themed phishing email containing a link to download a compressed Windows shortcut (.lnk) file. Opening this file will install Astaroth on the compromised host.
LNK files contain obfuscated JavaScript that is responsible for retrieving additional JavaScript from external servers. The newly fetched JavaScript code downloads a number of files from one of the randomly selected hard-coded servers.
It contains an AutoIt script that is executed by the JavaScript payload, which then loads and executes the shellcode. Additionally, a Delphi-based DLL is loaded to decrypt the Astaroth malware and inject it into the newly created RegSvc.exe process.
Astaroth is Delphi malware designed to monitor victims’ visits to banking and cryptocurrency websites and use keylogging to steal credentials. The captured information is sent to the attacker using Ngrok reverse proxy.

This is accomplished by checking the active browser program window every second to see if any banking-related sites are open. When these conditions are met, the malware hooks keyboard events and records keystrokes. Some of the targeted websites are listed below.
Kaisha Gob[.]brsafra.com[.]br itau.com[.]br bancooriginal.com[.]br santandernet.com[.]br btgpactual[.]com ether scan[.]iobinance[.]com bitcointrade.com[.]br metamask[.]io foxbit.com[.]br local bitcoin[.]com

Astaroth is also equipped with analysis resistance, automatically shutting down emulators, debuggers, and analysis tools such as the QEMU guest agent, HookExplorer, IDA Pro, ImmunityDebugger, PE Tools, WinDbg, and Wireshark when it is detected.
Persistence on the host is configured by dropping an LNK file into the Windows startup folder that runs an AutoIT script that automatically launches the malware upon system restart. Additionally, not only is the first URL accessed by the JavaScript in the LNK file geofenced, but the malware also ensures that the machine’s system locale is not set to English or US.
“Astaroth uses GitHub to update its configuration if the C2 server becomes inaccessible. By hosting images on GitHub, we use steganography to hide this information from view,” McAfee said.
In doing so, the malware leverages a legitimate platform to host configuration files, turning it into a resilient backup infrastructure when the primary C2 server becomes inaccessible. The company said it worked with a Microsoft-owned subsidiary to remove the GitHub repository and temporarily cripple its operations.
Source link