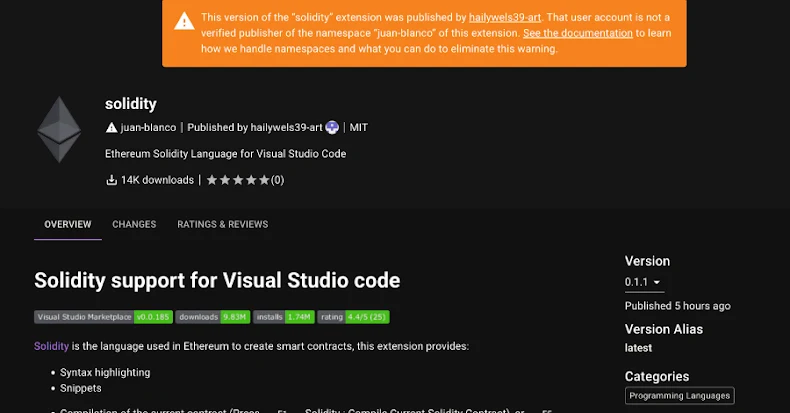
Cybersecurity researchers have flagged a new malicious extension in the Open VSX registry that harbors a remote access Trojan called SleepyDuck.
According to John Tuckner of Secure Annex, the extension in question, juan-bianco.solidity-vlang (version 0.0.7), was first published as a completely benign library on October 31, 2025, then reached 14,000 downloads before being updated to version 0.0.8 with new malicious functionality on November 1.
“The malware includes sandbox evasion techniques and leverages Ethereum contracts to update command and control addresses in case the original address is deleted,” Tuckner added.
We have repeatedly detected campaigns targeting Solidity developers distributing malicious extensions on both the Visual Studio Extension Marketplace and Open VSX. In July 2025, Kaspersky revealed that a Russian developer lost $500,000 in cryptocurrency assets after installing such an extension through Cursor.

In the latest case detected by an enterprise extension security company, the malware is triggered when a new code editor window is opened or a .sol file is selected.
Specifically, it is configured to find the fastest Ethereum remote procedure call (RPC) provider to connect to in order to gain access to the blockchain and initiate a connection with “sleepyduck”‘s remote server.[.]xyz” (as it is named) via the contract address “0xDAfb81732db454DA238e9cFC9A9Fe5fb8e34c465” and starts a polling loop that checks every 30 seconds for new commands to be executed on the host.
It can also collect system information such as hostname, username, MAC address, time zone, etc. and leak the details to servers. If the domain is occupied or deleted, the malware has built-in fallback controls and accesses a predefined list of Ethereum RPC addresses to extract contract information that can hold server details.
In addition, this extension has the ability to reach new configurations from contract addresses to set up new servers, as well as run emergency commands against all endpoints in case of unexpected events. The contract was created on October 31, 2025, and the attacker updated the server details from “localhost:8080” to “sleepyduck.”[.]xyz” will be executed over four transactions.
It is unclear whether the attackers artificially inflated the download numbers to increase the extension’s relevance in search results. This is a tactic often employed to increase popularity by tricking unsuspecting developers into installing malicious libraries.
This development comes at the same time that the company also revealed details of another set of five extensions, this time published on the VS Code Extension Marketplace by a user named “developmentinc.” It includes a Pokemon-themed library (‘mock1’) that downloads a batch script miner from an external server.[.]su:443″) is installed or enabled, run the miner using “cmd.exe”.
The script file uses PowerShell to restart itself with administrator privileges, add all drive letters from C: to Z: and configure Microsoft Defender Antivirus exclusions, as well as download the Monero mining executable from ‘mock1’.[.]Run “su”.

Extensions uploaded by threat actors are no longer available for download, but are listed below.
Development Co., Ltd. cfx-lua-vs Development Co., Ltd. Pokemon Development Co., Ltd. Trizon-vs Development Co., Ltd. Minecraft Snippet Development Co., Ltd. kombai-vs
Users are advised to be careful when downloading extensions and ensure that they are from reputable publishers. Microsoft announced in June that it would begin regular market-wide scans to protect users from malware. All extensions that have been removed from the official marketplace can be found on the RemovedPackages page on GitHub.
Source link