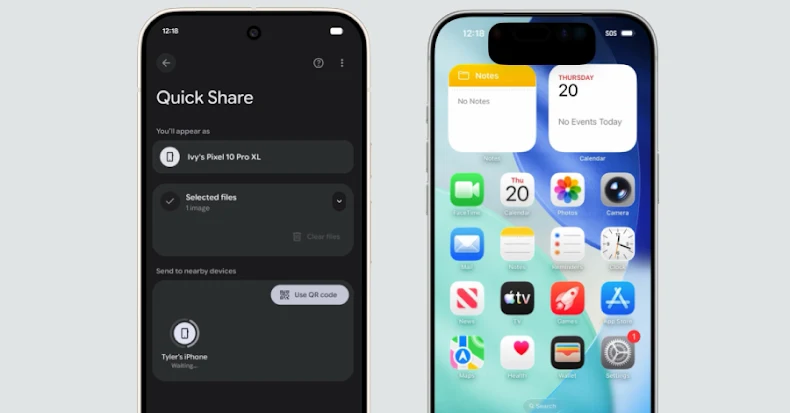
Surprisingly, Google announced Thursday that it has updated its peer-to-peer file transfer service, Quick Share, to work with Apple’s AirDrop device, allowing users to more easily share files and photos between Android and iPhone devices.
The cross-platform sharing feature is currently limited to the Pixel 10 lineup and works with iPhone, iPad, and macOS devices, but will be expanded to other Android devices in the future.
The only caveat to transferring files from a Pixel 10 smartphone via AirDrop is that Apple device owners must make their iPhone (or iPad or Mac) discoverable by everyone. This can be enabled for 10 minutes.
Similarly, according to a support document published by Google, to receive content from an Apple device, Android device users must either adjust their Quick Share visibility to everyone for 10 minutes or go into receive mode on the Quick Share page.

“We built Quick Share interoperability support for AirDrop using the same rigorous security standards we apply to all Google products,” said Dave Kleidermacher, vice president of platform security and privacy at Google.
Central to the future is a layered security approach that leverages the memory-safe Rust programming language to create secure shared channels. According to Google, this eliminates an entire class of memory safety vulnerabilities and makes implementations more resilient to attacks that attempt to exploit memory errors.
The tech giant also noted that the feature does not rely on any workarounds and no data is routed through its servers, adding that it is open to working with Apple to enable “Contacts Only” mode in the future.
NetSPI, which conducted an independent assessment in August 2025, stated that “Google’s implementation of the Quick Share version does not introduce vulnerabilities to the broader protocol ecosystem.”
“Although it shares certain characteristics with implementations created by other manufacturers, this implementation is fairly secure. In fact, the process of file exchange is particularly strong because no information is leaked, a common weakness in other manufacturers’ implementations.”
However, that analysis revealed a low-severity information disclosure vulnerability (CVSS score: 2.1). This vulnerability could allow an attacker with physical access to the device to access information such as image thumbnails and SHA256 hashes of phone numbers and email addresses. Google has since addressed this issue.

The development comes after Google said it had blocked more than 115 million attempts in India to install sideloaded apps that requested access to sensitive privileges for financial fraud. The company also said it is piloting new features in Japan in collaboration with financial services such as Google Pay, Navi, and Paytm to combat scams that trick users into opening an app when sharing their screen.
“On devices running Android 11 or later, users will now see a prominent warning when they open one of these apps while sharing their screen in a call with an unknown contact,” said Evan Kotsovinos, Google’s vice president of privacy, safety and security. “This feature provides the option to end calls and stop screen sharing with a single tap, protecting users from potential fraudulent activity.
Finally, Google said it is also developing Enhanced Phone Number Verification (ePNV), a new Android-based security protocol that replaces the SMS OTP flow with SIM-based verification to improve sign-in security.
Source link