According to Kaspersky, the attackers involved in the forum troll operation are believed to be involved in a new phishing campaign targeting individuals in Russia.
A Russian cybersecurity vendor announced that it detected new activity in October 2025. The origin of the threat actor is currently unknown.
“While the spring cyberattacks focused on organizations, the fall cyberattacks focused on specific individuals: academics in the fields of political science, international relations, and global economics working at major Russian universities and research institutes,” said security researcher Georgy Kucherin.
Operation ForumTroll refers to a series of sophisticated phishing attacks that exploit a then-zero-day vulnerability in Google Chrome (CVE-2025-2783) to deliver the LeetAgent backdoor and a spyware implant known as Dante.
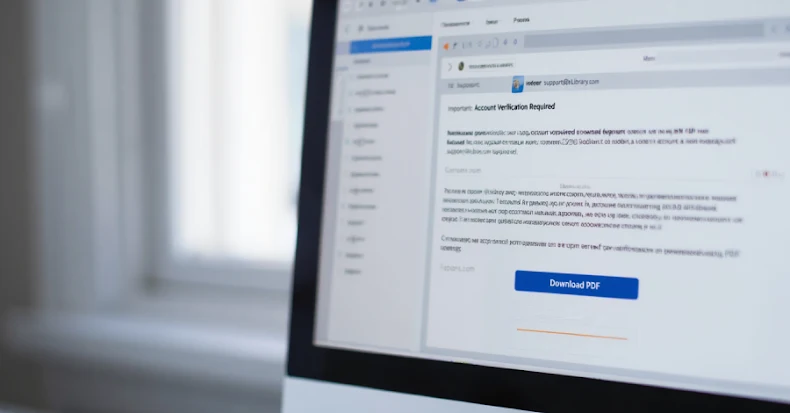
The latest wave of attacks also started with emails claiming to be from eLibrary, a Russian scientific electronic library, with messages sent from the address “support@e-library”.[.]This domain was registered in March 2025, six months before the campaign began, suggesting that preparations for the attack had been underway for quite some time.

Kaspersky said the strategic domain aging was done to avoid the red flags that typically accompany sending email from newly registered domains. In addition, the attackers also hosted a copy of the legitimate eLibrary home page (“elibrary”).[.]ru”) on a fake domain to maintain the ruse.
This email instructs potential targets to download a plagiarism report by clicking on an embedded link pointing to a malicious site. When a victim performs this step, a ZIP archive with the naming pattern “__.zip” is downloaded to the victim’s machine.
Additionally, these links are designed for one-time use, so any subsequent attempts to navigate to the URL will result in a message in Russian that says “Download failed. Please try again later.” If users attempt to download from a platform other than Windows, they will see a message that says, “Please try again later on a Windows computer.”
“The attackers also carefully customized their phishing emails to target experts in specific fields,” the company said. “The downloaded archives were labeled with the victim’s last name, first name and patronymic.”
The archive contains a Windows shortcut (LNK) with the same name that, when executed, runs a PowerShell script that downloads and launches a PowerShell-based payload from a remote server. The payload then accesses the URL to retrieve the final DLL and uses COM hijacking to persist it. It also downloads a decoy PDF and displays it to the victim.
The final payload is a command and control (C2) and red team framework known as Tuoni, which allows the attacker to gain remote access to the victim’s Windows device.
“Forum trolls have been targeting organizations and individuals in Russia and Belarus since at least 2022,” Kaspersky said. “Given this long timeline, it is likely that this APT group will continue to target groups and individuals of interest in both countries.”
The disclosure comes as Positive Technologies details the activities of two threat clusters: QuietCrabs (apparently a Chinese hacker group also tracked as UTA0178 and UNC5221) and Thor, which appears to be involved in ransomware attacks since May 2025.

These intrusion sets are known to exploit security flaws in Microsoft SharePoint (CVE-2025-53770), Ivanti Endpoint Manager Mobile (CVE-2025-4427 and CVE-2025-4428), Ivanti Connect Secure (CVE-2024-21887), and Ivanti Sentry (CVE-2023-38035).
The attack carried out by QuietCrabs leverages initial access to deploy an ASPX web shell and uses it to deliver a JSP loader that can download and run KrustyLoader, dropping the Sliver implant.
“Thor is a threat group first observed in attacks against Russian companies in 2025,” said researchers Alexander Badaev, Klimenty Galkin, and Vladislav Lunin. “As the final payload, the attackers use LockBit and Babuk ransomware, as well as Tactical RMM and MeshAgent to maintain persistence.”
Source link