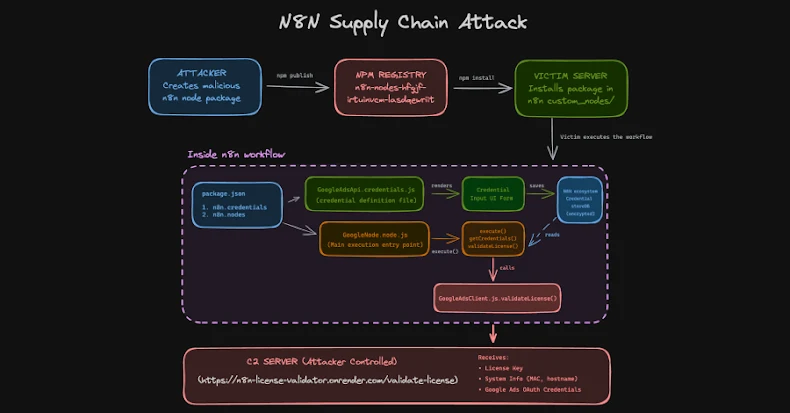
Threat actors have been observed uploading a set of eight packages to the npm registry masquerading as integrations targeting the n8n workflow automation platform to steal developers’ OAuth credentials.
One such package, named ‘n8n-nodes-hfgjf-irtuinvcm-lasdqewriit’, mimics the Google Ads integration, prompting users to link their ad accounts in a seemingly legitimate form and siphon it to a server under the attacker’s control.
“This attack represents another expansion of supply chain threats,” Endor Labs said in a report released last week. “Unlike traditional npm malware, which often targets developer credentials, this campaign exploited a workflow automation platform that acts as a centralized credential repository that holds OAuth tokens, API keys, and sensitive credentials for dozens of integrated services, including Google Ads, Stripe, and Salesforce, in one place.”

The complete list of identified packages that have since been removed is:
n8n-nodes-hfgjf-irtuinvcm-lasdqewriit (4,241 downloads, author: kakashi-hatake) n8n-nodes-ggdv-hdfvcnnje-uyrokvbkl (1,657 downloads, author: kakashi-hatake) n8n-nodes-vbmkajdsa-uehfitvv-ueqjhhksdlkkmz (1,493 downloads, author: kakashi-hatake) n8n-nodes-performance-metrics (752 downloads, author: hezi109) n8n-nodes-gasdhgfuy-rejerw-ytjsadx (8,385 downloads, author: zabuza-momochi) n8n-nodes-danev (5,525 downloads, author: dan_even_segler) n8n-nodes-rooyai-model (1,731 downloads, author: haggags) n8n-nodes-zalo-vietts (4,241 downloads, author: vietts_code and diendh)
Users ‘zabuza-momochi’, ‘dan_even_segler’, and ‘diendh’ are also linked to other libraries that are still available for download as of this writing.
It is unknown if these contain similar malicious functionality. However, evaluation of the first three packages with ReversingLabs Spectra Assure found no security issues. In the case of ‘n8n-nodes-zl-vietts’, analysis flagged the library as containing a component with a history of malware.

Interestingly, an updated version of the package ‘n8n-nodes-gg-udhasudsh-hgjkhg-official’ was published on npm just three hours ago, suggesting that a campaign may be underway.
Once installed as a community node, the malicious package behaves like any other n8n integration, displaying a configuration screen and storing the Google Ads account’s OAuth token in encrypted form in the n8n credential store. When the workflow runs, it runs code that decrypts the stored token using n8n’s master key and extracts it to a remote server.
This development marks the first time that a supply chain threat has explicitly targeted the n8n ecosystem, with malicious actors weaponizing community integration trust to achieve their goals.

This finding highlights security issues associated with integrating untrusted workflows and potentially expands the attack surface. Developers are encouraged to audit packages before installing them, examine package metadata for anomalies, and use official n8n integrations.
N8n also warns of the security risks posed by the use of npm’s community nodes, stating that it is possible to perform malicious actions on the machine where the service is running. For self-hosted n8n instances, we recommend disabling community nodes by setting N8N_COMMUNITY_PACKAGES_ENABLED to false.
“Community nodes run with the same level of access as n8n itself. Community nodes can read environment variables, access the file system, make outgoing network requests, and most importantly, receive decrypted API keys and OAuth tokens while running workflows,” said researchers Kiran Raj and Henrik Preet. “There is no sandboxing or separation between the node code and the n8n runtime.”
“Thus, a single malicious npm package is enough to gain deep visibility into workflows, steal credentials, and communicate externally without immediately arousing suspicion. For attackers, the npm supply chain provides a silent and highly effective entry point into an n8n environment.”
Source link