Cybersecurity researchers have revealed details of a previously undocumented, feature-rich malware framework codenamed VoidLink that is specifically designed for long-term, stealthy access to Linux-based cloud environments.
According to a new report from Check Point Research, cloud-native Linux malware frameworks consist of a set of custom loaders, implants, rootkits, and modular plugins that allow operators to extend or change their functionality over time or pivot if their purpose changes. It was first discovered in December 2025.
“The framework includes multiple cloud-focused features and modules and is designed to work reliably in cloud and container environments for long periods of time,” the cybersecurity firm said in an analysis published today. “VoidLink’s architecture is very flexible and highly modular, centered around a custom plugin API that appears to be inspired by Cobalt Strike’s Beacon Object Files (BOF) approach. This API is used by over 30 plugin modules available by default.”
This finding reflects a shift in attacker focus from Windows to Linux systems, which are emerging as the foundation for cloud services and critical operations. Actively maintained and evolving, VoidLink has been assessed to be the work of Chinese-affiliated threat actors.

A cloud-first implant written in the Zig programming language, this toolkit can discover major cloud environments. When Amazon Web Services (AWS), Google Cloud, Microsoft Azure, Alibaba, and Tencent recognize that you’re running inside a Docker container or Kubernetes pod, they adapt their behavior. You can also collect credentials associated with cloud environments and popular source code version control systems such as Git.
 High-level overview of VoidLink
High-level overview of VoidLink
The targeting of these services indicates that VoidLink is likely designed to target software developers in order to steal sensitive data or use access to conduct supply chain attacks.
Some of the other features are listed below.
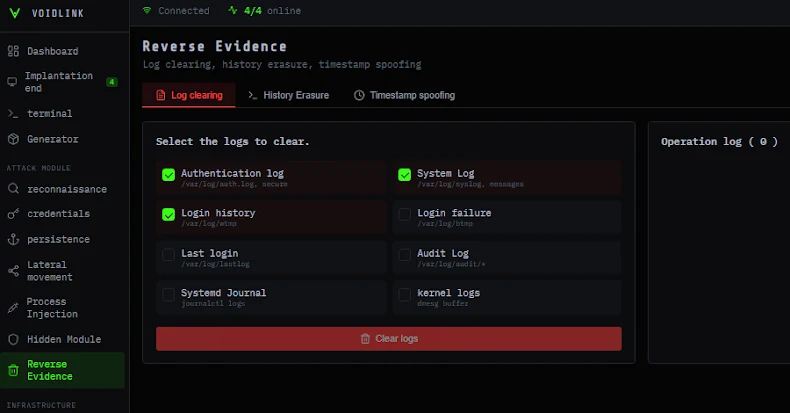
Hide processes based on LD_PRELOAD, loadable kernel modules (LKMs), and Linux kernel versions Rootkit-like functionality using eBPF In-memory plugin system to extend functionality Support for various command and control (C2) channels such as HTTP/HTTPS, WebSockets, ICMP, and DNS tunneling Form peer-to-peer (P2P) or mesh-style networks between compromised hosts
China’s web-based dashboard allows attackers to remotely control the implant, create bespoke versions on the fly, manage files, tasks, and plugins, and execute various stages of the attack cycle, from reconnaissance and persistence to lateral movement and defense evasion that erases any trace of malicious activity.
 Builder panel for creating customized versions of VoidLink
Builder panel for creating customized versions of VoidLink
VoidLink supports 37 plugins spanning anti-forensics, reconnaissance, containers, privilege escalation, lateral movement, and more, turning it into a full-fledged post-exploitation framework.
Anti-Forensics: Wipe or edit logs and shell history based on keywords and time-stomp files that preclude analysis. Cloud: Easily discover and elevate privileges in Kubernetes and Docker, escape containers, and investigate misconfigurations. Collect credentials: Collect credentials and secrets such as SSH keys, Git credentials, local password materials, browser credentials and cookies, tokens, and API keys. Lateral Movement (Spreading) Persistence uses SSH-based worms laterally to help establish persistence through dynamic linker exploitation, cron jobs, and system services. Recon collects detailed system and environmental information.
Check Point described VoidLink as “impressive” and “much more sophisticated than typical Linux malware,” saying it features a core orchestrator component that handles C2 communications and task execution.

It also includes a set of anti-analysis features to avoid detection. It may flag various debuggers and monitoring tools as well as remove itself if signs of tampering are detected. It also has a self-modifying code option that allows you to bypass the runtime memory scanner and decrypt protected code regions at runtime, encrypting them when not in use.
Additionally, the malware framework enumerates the security products and hardening measures installed on the infected host, calculates a risk score, and derives an overall evasion strategy. For example, this may include slowing down port scans and providing more control in high-risk environments.
“Developers demonstrate high levels of technical expertise with high proficiency across multiple programming languages, including modern frameworks such as Go, Zig, C, and React,” Check Point said. “Additionally, attackers have deep knowledge of the internal workings of sophisticated operating systems, allowing them to develop sophisticated and complex solutions.”
“VoidLink aims to automate evasion as much as possible by profiling the environment and choosing the best strategies to operate in that environment. Powered by kernel-mode tradecraft and a vast plugin ecosystem, VoidLink enables operators to move through cloud environments and container ecosystems with adaptive stealth.”
Source link