Lumen Technologies’ Black Lotus Labs team announced that it had been null-routing traffic to more than 550 command and control (C2) nodes associated with the AISURU/Kimwolf botnet since early October 2025.
AISURU and its Android counterpart Kimwolf have recently emerged as one of the largest botnets, capable of forcing enslaved devices to participate in distributed denial of service (DDoS) attacks and relaying malicious traffic for residential proxy services.
Details about Kimwolf were revealed last month when QiAnXin XLab published a thorough analysis of the malware. The malware turns compromised devices (mostly unauthorized Android TV streaming devices) into residential proxies by distributing a software development kit (SDK) called ByteConnect, either directly or through a sketchy pre-installed app.
The end result was that the botnet expanded to infect over 2 million Android devices using the exposed Android Debug Bridge (ADB) service by tunneling through residential proxy networks, thereby allowing attackers to compromise a wide range of TV boxes.
A subsequent Synthient report revealed that the Kimwolf attackers were attempting to offload proxy bandwidth in exchange for an upfront payment.
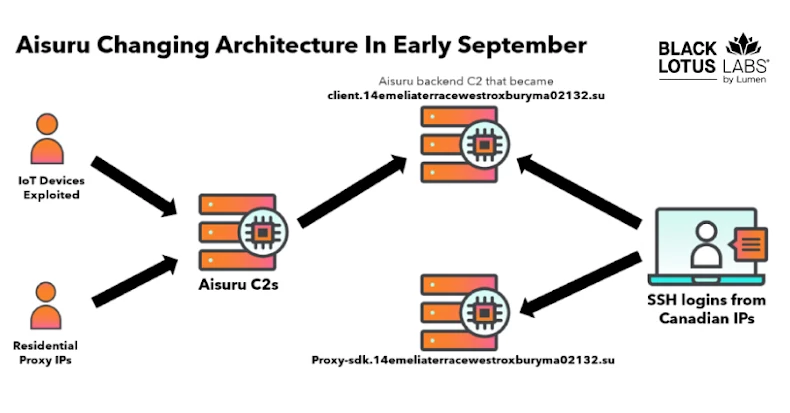
Black Lotus Labs announced that it has identified a group of residential SSH connections originating from multiple Canadian IP addresses in September 2025 based on analysis of Aisuru’s backend C2 65.108.5.[.]46, IP address to access 194.46.59 using SSH[.]169, proxy-sdk.14emeliaterracewestroxburyma02132[.]vinegar.

Notably, second-level domains surpassed Google on Cloudflare’s list of top 100 domains in November 2025, prompting the web infrastructure company to remove them from the list.
Then, in early October 2025, the cybersecurity company announced that it had identified another C2 domain – greatfirewallisacensingtool.14emeliaterracewestroxburyma02132[.]su – resolved to 104.171.170[.]21, an IP address belonging to Utah-based hosting provider Resi Rack LLC. The company advertises itself as a “premium game server hosting provider.”
This connection is significant because a recent report by independent security journalist Brian Krebs revealed how the people behind various botnet-based proxy services were selling their warez on a Discord server called resi.[.]To. This includes the co-founders of Resi Rack, who are said to have been actively working on selling proxy services through Discord for about two years.
The server, which has since disappeared, was owned by someone named “d” (presumed to be a shortened version of the handle “Dort”), and Snow is believed to be the botmaster.
“In early October, we observed a 300% spike in the number of new bots added to Kimwolf in seven days. This was the beginning of the increase, and by mid-month the total number of bots reached 800,000,” Black Lotus Labs said. “We found that nearly all of the bots in this surge were being sold through a single residential proxy service.”
It was subsequently discovered that the Kimwolf C2 architecture was scanning for vulnerable devices in PYPROXY and other services from October 20, 2025 to November 6, 2025. This behavior is explained by the botnet’s exploitation of security flaws in many proxy services that allow residential proxy endpoints to interact with devices on the internal network and drop malware.
This turns your device into a residential proxy node and makes its public IP address (assigned by your internet service provider) listed for rental on your residential proxy provider site. Threat actors, such as the attackers behind these botnets, lease access to infected nodes and weaponize them to scan local networks for devices with ADB mode enabled to further spread.

“After one successful null route, [in October 2025]the greatfirewallisacensingtool domain was observed moving to 104.171.170.[.]201, another Resi Rack LLC IP,” Black Lotus Labs said. “Once this server started, we saw a significant spike in traffic from 176.65.149.”[.]At 19:25565, the server was being used to host malware. This was on a common ASN that was simultaneously used by the Aisuru botnet. ”
The disclosure came against the backdrop of a Chawkr report detailing a sophisticated proxy network containing 832 compromised KeeneticOS routers operating between Russian ISPs including Net By Net Holding LLC, VladLink, and GorodSamara.
“The consistent SSH fingerprint and identical configuration across all 832 devices indicates automated mass exploitation, whether leveraging stolen credentials, embedded backdoors, or known security flaws in router firmware,” the report said. “Each compromised router maintains both HTTP (port 80) and SSH (port 22) access.”
These compromised SOHO routers act as residential proxy nodes, giving threat actors the ability to perform malicious activities under the guise of normal internet traffic. This shows that attackers are increasingly using consumer devices as vectors for multi-stage attacks.
“Unlike data center IPs or known hosting provider addresses, these residential endpoints operate under the radar of most security vendor reputation lists and threat intelligence feeds,” Chawkr said.
“Their legitimate residence classification and clean IP reputation allow malicious traffic to disguise normal consumer activity and evade detection mechanisms that immediately flag requests from suspicious hosting infrastructure or known proxy services.”
Source link