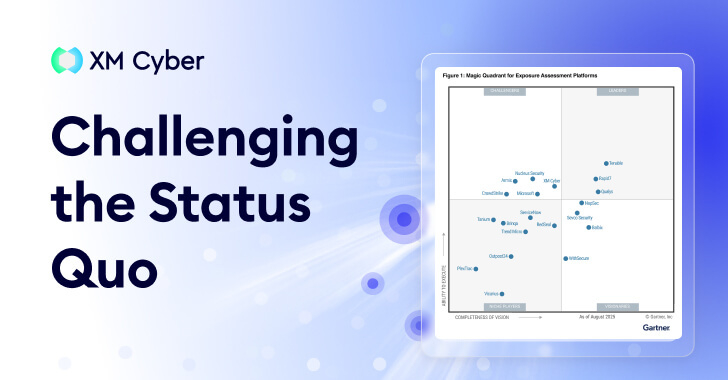
Gartner® doesn’t create new categories lightly. Typically, new acronyms emerge only when it becomes mathematically impossible to complete an industry-wide “to-do list.” The introduction of the Exposure Assessment Platform (EAP) category therefore appears to be a formal acknowledgment that traditional vulnerability management (VM) is no longer a viable way to protect modern enterprises.
The transition from traditional vulnerability assessment market guides to the new Magic Quadrant for EAP represents a move away from an endless stream of “vulnerability hoses” or CVEs and toward a Continuous Threat Exposure Management (CTEM) model. For us, this is more than just a change in terminology. This is an attempt to resolve the “dead end” paradox that has plagued security teams for a decade.
In the first Magic Quadrant report in this category, Gartner evaluated 20 vendors on their ability to support continuous discovery, risk-informed prioritization, and unified visibility across cloud, on-premises, and identity layers. This article details the report’s key findings, the drivers behind the new category, the features that define it, and takeaways for security teams.
Why exposure assessment is becoming popular
Security tools have always promised to reduce risk, but most have delivered noise. Some products reveal misconfigurations. In other cases, log privilege drift. Third, flag vulnerable external assets. The result is a production crisis and chronic vigilance fatigue in the SOC. Each tool provided a piece of the puzzle, but none could put all the pieces together to explain how exposure forms or what should be fixed in the first place to avoid exposure.
Skepticism about traditional VM tools is understandable. Data from more than 15,000 environments shows that 74% of identified exposures are “dead ends,” residing on assets with no viable path to critical systems. In the old model, security teams spent 90% of their remediation efforts remediating these impasses, and the risk reduction to business processes could be virtually zero.
EAP is designed to address this. We bring all these elements into a unified view, track how systems, identities, and vulnerabilities interact in real-world environments, and show how attackers actually use it to move from low-risk development environments to critical assets.
This model has attracted attention because it reflects how attackers behave. Threat actors are not limited to a single flaw. They have weak controls, uncoordinated permissions, and detection blind spots. The EAP model tracks how exposures accumulate across the environment and direct attackers to reachable assets. Platforms in this category are built to show where risk occurs, how it spreads, and what conditions support attacker movement.
Gartner predicts that organizations that use this approach will reduce unplanned downtime by 30% by 2027. These dramatic gains are based on similarly dramatic changes in how exposures are defined, modeled, and operationalized across environments. This change impacts every layer of the security workflow, from how signals are connected to how teams decide what to fix first.
Drill down: from static lists to moving exposures
Workflow changes start with how EAPs detect and connect conditions that lead to risk. Exposure assessment platforms take a different approach than traditional vulnerability tools. They are built around a unique set of features, including:
These unify discovery across your environment. EAP continuously scans internal networks, cloud workloads, and user-facing systems to identify both known and untracked assets, as well as unmanaged identities, misconfigured roles, and legacy systems not listed in standard inventory. Prioritize based on context, not just severity. Exposures are ranked using multiple parameters such as asset importance, access paths, exploitability, and scope of control. This allows the team to see which problems are reachable, which are isolated, and which allow for lateral movement. They integrate exposure data into operational workflows. EAP output is designed to support actions. The platform connects with IT and security tools so findings can be assigned, tracked, and resolved through existing systems without waiting for quarterly audits or manual reviews. Supports lifecycle tracking. Once exposures are identified, EAP monitors them throughout remediation steps, configuration changes, and policy updates. That visibility helps teams understand what has been fixed, what remains, and how each adjustment impacts risk posture.
What the quadrant reveals about market maturity
New Magic Quadrant highlights market fragmentation. Meanwhile, traditional incumbents are looking to “bolt on” publishing capabilities to their existing scanning engines. The other is a native Exposure Management player that has been modeling attacker behavior for years.
The maturity of this category is evidenced by the changing definition of done. Success is now measured not by the number of vulnerabilities patched, but by how many important attack paths are eliminated. Platforms like XM Cyber, built on attack graph-based modeling, are currently spearheading this approach.
What security teams should focus on
Exposure assessment is now established as its own category, with defined functions, evaluation criteria, and an increasing role in corporate workflows. The Magic Quadrant platform identifies relevant exposures, maps which assets can be accessed, and guides remediation based on attacker movements.
For practitioners, the immediate value is efficiency. These platforms are making decisions about what to fix first, how to allocate ownership, and where risk mitigation will have the greatest impact. Exposure assessment is now positioned as a core layer of how we protect, maintain and understand the environment. If you can mathematically prove that 74% of alerts are safe to ignore, you’re not just “improving security,” you’re giving back time and resources to teams that are likely already at breaking point. The EAP category is finally aligning security metrics with business realities. The question is no longer “How many vulnerabilities do we have?” But “Are we safe from important attack vectors?”
To learn more about why XM Cyber was named a Challenger in Exposure Rating Platform’s 2025 Magic Quadrant, get your copy of the report here.
Note: This article was professionally written and contributed by Maya Malevich, Director of Product Marketing at XM Cyber.
Gartner Disclaimer: Gartner, Magic Quadrant for Exposure Assessment Platforms, Mitchell Schneider, Dhivya Poole, Jonathan Nunez, November 10, 2025. GARTNER is a registered trademark and service mark of Gartner and Magic Quadrant is a registered trademark of Gartner, Inc. and/or its affiliates in the United States and other countries and is used herein with permission. Unauthorized reproduction is prohibited. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Source link