A new security flaw in SmarterTools SmarterMail email software is now being exploited in the wild two days after a patch was released.
This vulnerability currently does not have a CVE identifier and is tracked by watchTowr Labs as WT-2026-0001. Patched by SmarterTools with build 9511 on January 15, 2026 after responsible disclosure by exposure management platform on January 8, 2026.
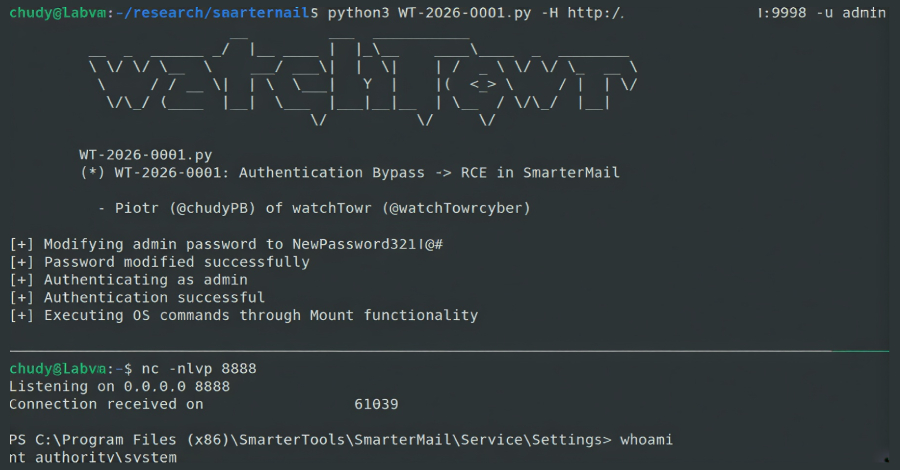
This is described as an authentication bypass flaw that could allow arbitrary users to reset the password of a SmarterMail system administrator using a specially crafted HTTP request to the “/api/v1/auth/force-reset-password” endpoint.
“The problem, of course, is that users can run the OS directly with RCE functionality as a feature.” [operating system] command,” said watchTowr Labs researchers Piotr Bazydlo and Sina Kheirkhah.
The root of the issue lies in the “SmarterMail.Web.Api.AuthenticationController.ForceResetPassword” function, which not only allows the endpoint to be reached without authentication, but also handles incoming requests depending on whether the user is a system administrator or not, by taking advantage of the fact that the reset request is accompanied by a boolean flag called “IsSysAdmin.”

If the flag is set to ‘true’ (i.e. indicating that the user is an administrator), the underlying logic performs the following set of actions:
Gets the settings corresponding to the username passed as input in the HTTP request. Create a new system administrator item with a new password. Update your administrator account with a new password.
In other words, Privileged Pass is configured to allow you to easily update an administrator user’s password by sending an HTTP request using the administrator account’s username and password of your choice. This complete lack of security control could be exploited by an attacker to gain elevated access if they knew the existing administrator’s username.
This is not the end. This is because authentication bypass provides a direct path to remote code execution through built-in functionality that allows system administrators to execute operating system commands on the underlying operating system and obtain a SYSTEM-level shell.
To do this, go to the “Settings” page, create a new volume, and enter any command in the “Volume mount command” field. This command is then executed by the host operating system.
The cybersecurity company said it decided to make its findings public following a post on the SmarterTools community portal. In the post, users claimed that logs showed that the same “force-reset-password” endpoint was used to change passwords on January 17, 2026, two days after the patch was released, leaving them unable to access their administrator accounts.
This may indicate that the attacker reverse-engineered the patch and reconstructed the flaw. To make matters worse, it doesn’t help that SmarterMail’s release notes are vague and don’t explicitly mention what issues have been resolved. One item in the bulleted list for build 9511 simply says “Important: Important security fixes.”

In response, SmarterTools CEO Tim Uzzanti hinted that this was to avoid giving attackers further avenues of attack, but said that they plan to send an email whenever a new CVE is discovered, and again when a build is released that resolves the issue.
“In our 23-plus years, we have only had a few CVEs, and they were primarily communicated through release notes and critical fix references,” Uzzanti said in response to transparency concerns raised by customers. “We appreciate the feedback that will lead to future policy changes.”
It is currently unknown whether such an email was sent to SmarterMail administrators this time. Hacker News has reached out to SmarterTools for comment and will update the article if we hear back.
This development comes less than a month after the Cyber Security Authority of Singapore (CSA) detailed a maximum severity security flaw in SmarterMail (CVE-2025-52691, CVSS score: 10.0) that could be exploited to remotely execute code.
Source link