Indian government agencies have been targeted in two campaigns conducted by threat actors operating in Pakistan using previously undocumented trade channels.
These campaigns were codenamed Gopher Strike and Sheet Attack by Zscaler ThreatLabz, identified in September 2025.
“While these campaigns share some similarities with APT36, a Pakistan-linked advanced persistent threat (APT) group, we assess with medium confidence that the activity identified in this analysis may originate from a new subgroup or another Pakistan-linked group operating in parallel,” researchers Sudeep Singh and Yin Hong Chan said.
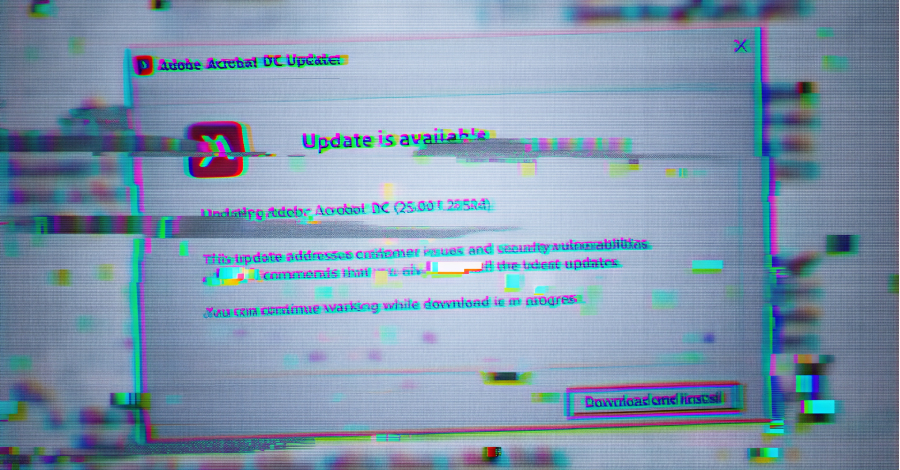
The name Sheet Attack comes from the use of legitimate services such as Google Sheets, Firebase, and email for command and control (C2). Meanwhile, Gopher Strike is credited with using phishing emails as a starting point to deliver PDF documents containing blurry images overlaid with seemingly innocuous pop-ups instructing recipients to download an update for Adobe Acrobat Reader DC.

The main purpose of this image is to give the user the impression that they need to install an update to access the document’s content. with fake update dialog[ダウンロードしてインストール]Clicking the button will trigger the download of the ISO image file only if the request originates from an IP address located in India and the user agent string corresponds to Windows.
“These server-side checks prevent automated URL analysis tools from retrieving ISO files and ensure that malicious files are delivered only to their intended targets,” Zscaler said.
The malicious payload embedded within the ISO image is a Golang-based downloader called GOGITTER that creates Visual Basic Script (VBScript) files if they do not exist in the following locations: “C:\Users\Public\Downloads”, “C:\Users\Public\Pictures”, and “%APPDATA%”. This script is designed to fetch VBScript commands every 30 seconds from two preconfigured C2 servers.
GOGITTER also sets persistence using a scheduled task configured to run the VBScript file mentioned above every 50 minutes. Additionally, verify that there is another file named “adobe_update.zip” within the same three folders. If the ZIP file does not exist, pull the archive from a private GitHub repository (“github”).[.]com/jaishankai/sockv6″). GitHub account created on June 7, 2025.

Upon successful download, the attack chain sends an HTTP GET request to the domain “adobe-acrobat”.[.]in” could inform threat actors that the endpoint is infected. GOGITTER then extracts and executes “edgehost.exe” from the ZIP file. GITSHELLPAD, a lightweight Golang-based backdoor, leverages private GitHub repositories for threat actor-controlled C2s.
Specifically, it polls the C2 server every 15 seconds with a GET request to access the contents of a file named “command.txt”. Supports 6 different commands –
cd .., change working directory to parent directory. cd, change directory to the specified path. run, executes a command in the background without capturing output. Upload, uploads the local file specified by path to a GitHub repository. Download, downloads the file to the specified path. By default, cmd /c is used to run the command and capture the output.

The results of the command execution are saved in a file called “result.txt” and uploaded to your GitHub account via an HTTP PUT request. If the command runs successfully, “command.txt” will be removed from your GitHub repository.
Zscaler said it also observed that the attacker used cURL commands to download RAR archives after gaining access to the victim’s machine. The archive contains a utility that collects system information and drops GOSHELL, a custom Golang-based loader used to deliver Cobalt Strike Beacons after multiple rounds of decoding. Wipe tools off the machine after use.
“GOSHELL’s size was artificially inflated to approximately 1 gigabyte by adding junk bytes to a Portable Executable (PE) overlay, likely to evade detection by antivirus software,” the cybersecurity firm said. “GOSHELL only runs on specific hostnames by comparing the victim’s hostname to a hard-coded list.”
Source link