In the 2025 cyber espionage attack, Chinese-linked threat actors were observed using the latest version of a backdoor called COOLCLIENT to facilitate comprehensive data theft from infected endpoints.
The activity was attributed to Mustang Panda (also known as Earth Preta, Fireant, HoneyMyte, Polaris, and Twill Typhoon), and the intrusions were primarily targeted at government agencies across the campaign across Myanmar, Mongolia, Malaysia, and Russia.
Revealing details of the updated malware, Kaspersky said it is being deployed as a secondary backdoor along with PlugX and LuminousMoth infections.
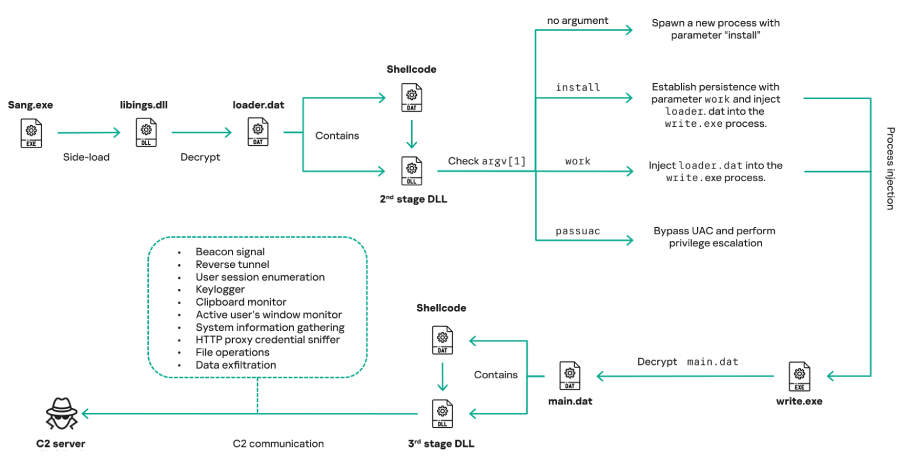
“COOLCLIENT was typically delivered with an encrypted loader file containing encrypted configuration data, shellcode, and next-stage DLL modules in memory,” the Russian cybersecurity firm said. “These modules relied on DLL sideloading as their primary execution method, and required a legitimate signed executable to load the malicious DLL.”

Between 2021 and 2025, Mustang Panda allegedly utilized signed binaries of various software products for this purpose, including Bitdefender (“qutppy.exe”), VLC Media Player (renamed from “vlc.exe” to “googleupdate.exe”), Ulead PhotoImpact (“olreg.exe”), and Sangfor (“sang.exe”).
Campaigns observed in 2024 and 2025 were found to exploit legitimate software developed by Sangfor, including campaigns targeting Pakistan and Myanmar, to deliver a COOLCLIENT variant that dropped and executed a never-before-seen rootkit.
COOLCLIENT was first documented by Sophos in November 2022 in a report detailing widespread use of DLL sideloading by a China-based APT group. Subsequent Trend Micro analysis officially identified the backdoor as Mustang Panda, highlighting its file read/delete, clipboard and active window monitoring capabilities.
The malware was also used in attacks targeting multiple carriers in a single Asian country in a long-running espionage campaign that could begin in 2021, Broadcom’s Symantec and Carbon Black Threat Hunters team revealed in June 2024.

COOLCLIENT is designed to collect system and user information, such as keystrokes, clipboard contents, files, and HTTP proxy credentials, from a host’s HTTP traffic packets based on instructions sent from a command and control (C2) server over TCP. You can also set up a reverse tunnel or proxy to receive and execute additional plugins in memory.
Some of the supported plugins are listed below.
ServiceMgrS.dll, a service management plugin that monitors all services on the victim host FileMgrS.dll, a file management plugin that enumerates, creates, moves, reads, compresses, searches, or deletes files and folders RemoteShellS.dll – a remote shell plugin that spawns a “cmd.exe” process that allows operators to issue commands and capture the resulting output
Mustang Panda has also been observed deploying three different stealer programs to extract saved login credentials from Google Chrome, Microsoft Edge, and other Chromium-based browsers. In at least one case, the attacker executed a cURL command to leak a Mozilla Firefox browser cookie file (“cookies.sqlite”) to Google Drive.
These thieves were detected in attacks on government departments in Myanmar, Malaysia, and Thailand, and are suspected of being used as part of a broader post-exploitation effort.

Additionally, this attack features the use of a known malware called TONESHELL (also known as TOnePipeShell). The malware is used with varying levels of functionality to establish persistence and drop additional payloads, including QReverse, a remote access Trojan with remote shell, file management, screenshot capture, and information gathering capabilities, and a USB worm codenamed TONEDISK.
Kaspersky Lab’s analysis of the browser credential stealer also revealed code-level similarities to the cookie stealer used by LuminousMoth, suggesting some degree of tooling sharing between the two clusters. Additionally, Mustang Panda has been observed using batch and PowerShell scripts to gather system information, conduct document theft operations, and steal browser login data.
“With features such as keylogging, clipboard monitoring, proxy credential theft, document leakage, browser credential harvesting, and large-scale file theft, HoneyMyte’s campaign appears to go far beyond traditional espionage goals such as document theft and persistence,” the company said.
“These tools mark a shift toward active monitoring of user activity, including capturing keystrokes, collecting clipboard data, and harvesting proxy credentials.”
Source link