Cybersecurity researchers have uncovered the secrets of a gateway monitoring and attacker-in-the-man (AitM) framework called DKnife, which has been operated by Chinese-linked attackers since at least 2019.
The framework consists of seven Linux-based implants designed to perform deep packet inspection, manipulate traffic, and deliver malware through routers and edge devices. Its primary target appears to be Chinese-speaking users and has been assessed based on the presence of phishing pages to obtain credentials for Chinese email services, leaked modules for popular Chinese mobile applications such as WeChat, and code references to Chinese media domains.
“DKnife attacks target a wide range of devices, including PCs, mobile devices, and Internet of Things (IoT) devices,” Cisco Talos researcher Ashley Shen noted in a report Thursday. “It delivers and communicates with ShadowPad and DarkNimbus backdoors by hijacking binary downloads and Android application updates.”
The cybersecurity firm said it discovered DKnife as part of its ongoing monitoring of another Chinese threat activity cluster codenamed Earth Minotaur, which is linked to tools such as the MOONSHINE exploit kit and the DarkNimbus (also known as DarkNights) backdoor. Interestingly, this backdoor is also used by a third Chinese-aligned Advanced Persistent Threat (APT) group called TheWizards.
Analysis of DKnife’s infrastructure revealed an IP address hosting WizardNet, a Windows implant deployed by TheWizards via the AitM framework called Spellbinder. The details of the toolkit were documented by ESET in April 2025.
Cisco says targeting Chinese-speaking users depends on discovering configuration files pulled from a single command-and-control (C2) server, increasing the likelihood that there are other servers hosting similar configurations to target different regions.
This is important given the infrastructure connections between DKnife and WizardNet, as TheWizards is known to target individuals and the gambling sector in Cambodia, Hong Kong, mainland China, the Philippines, and the United Arab Emirates.
 Features of the 7 DKnife components
Features of the 7 DKnife components
Unlike WizardNet, DKnife is designed to run on Linux-based devices. Its modular architecture allows carriers to offer a wide range of capabilities from packet analysis to traffic manipulation. It is delivered by ELF Downloader and contains 7 different components.
dknife.bin – the central nervous system of the framework responsible for deep packet inspection, user activity reporting, binary download hijacking, and DNS hijacking postapi.bin – a data reporter module that acts as a relay by receiving traffic from DKnife and reporting it to a remote C2 sslmm.bin – a reverse proxy modified from HAProxy that performs TLS termination, email decryption, and URL rerouting Module mmdown.bin – An updater module that connects to a hard-coded C2 server to download the APK used in the attack yitiji.bin – A packet forwarding module that creates a bridge TAP interface on the router to host and route attacker-injected LAN traffic Remote.bin – A peer-to-peer (P2P) VPN client module that creates a communication channel to a remote C2 dkupdate.bin – Updater and watchdog module to keep various components up and running
“DKnife collects credentials from major email providers in China and is able to host phishing pages for other services,” Talos said. “To collect email credentials, the sslmm.bin component presents its own TLS certificate to the client, terminates and decrypts the POP3/IMAP connection, and inspects the cleartext stream to extract the username and password.”
“The extracted credentials are tagged with “PASSWORD” and forwarded to the postapi.bin component, which ultimately relays them to the remote C2 server. ”
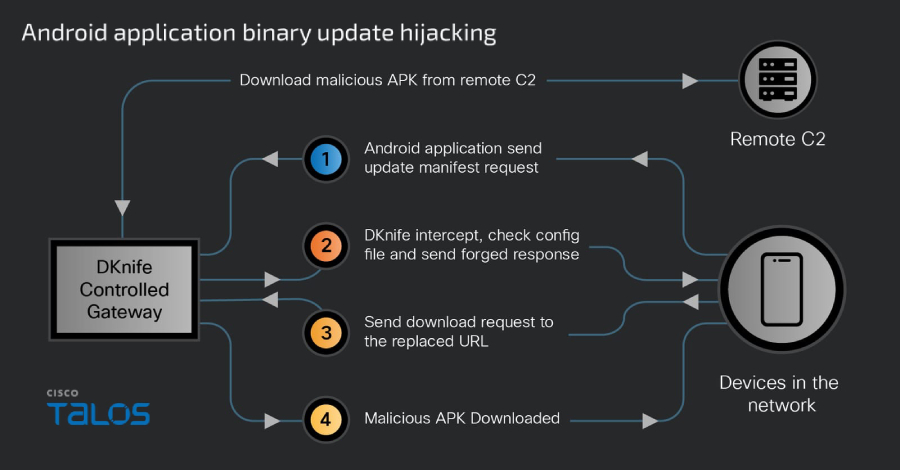
The core component of the framework is dknife.bin, which is responsible for deep packet inspection and allows carriers to conduct traffic monitoring campaigns ranging from “covert monitoring of user activity to active inline attacks that replace legitimate downloads with malicious payloads.” This includes –
Provides an updated C2 of DarkNimbus malware to Android and Windows Performs Domain Name System (DNS)-based hijacking over IPv4 and IPv6 to facilitate malicious redirects to JD.com-related domains Hijacks and replaces Android application updates related to Chinese news media, video streaming, image editing apps, e-commerce platforms, taxi service platforms, gaming, and porn video streaming apps by intercepting update manifest requests Windows and other binary downloads that load the ShadowPad backdoor and subsequently DarkNimbus based on certain preconfigured rules delivered via DLL sideloading. Interferes with communications from antivirus and PC management products, including 360 Total Security and Tencent services. Monitor user activity in real time and report it to your C2 server.
“Routers and edge devices remain prime targets for advanced targeted attack campaigns,” Talos said. “As attackers increase their efforts to compromise this infrastructure, it is important to understand the tools and TTPs they are using. The discovery of the DKnife framework highlights the advanced capabilities of modern AitM threats, which blend deep packet inspection, traffic manipulation, and customized malware delivery across a wide range of device types.”
Source link