It has been reported that 768 vulnerabilities with specified CVE identifiers increased from the 639 CVE in 2024 in 2024 and increased by 20 % year -on -year.
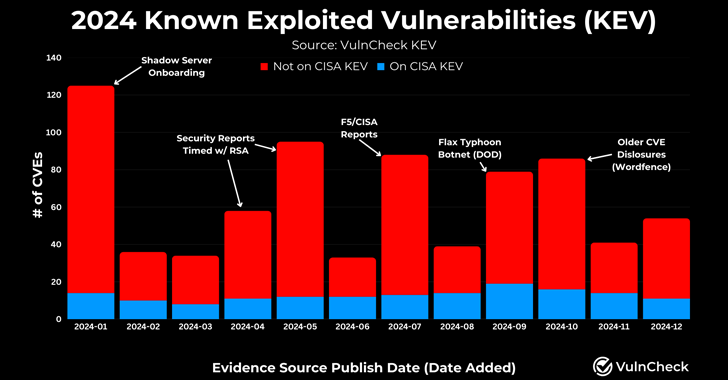
VULNCHECK, which describes 2024 as “another banner year for a threat actor targeting vulnerabilities,” was 23.6 % of the known vulnerabilities (Kev) were released or the CVE was released. Before that, he stated that it was known to be weapons.
This shows that it is slightly decreasing from 26.8 % in 2023 and is always trying to exploit the vulnerability life cycle.
“In 2024, it was publicly reported that 1 % of the published CVE was abused in the wild,” Vulncheck’s Patrick Garrity said in a report shared with hacker news. “It is expected that this number will grow because the exploitation is often discovered after the CVE is released.”

The report clarifies that 15 Chinese hacking groups out of a total of 60 threats are related to at least one abuse of vulnerabilities that were often exploited in 2023. It occurs two months later.
“It’s not surprising, but Log4J CVE (CVE-2021-44228) is associated with the overall threat actor, and 31 threat actors are related to exploitation,” Garrity said at the end of last year. The company has identified 65,245 hosts a potentially vulnerable and vulnerable person. defect.
As a whole, it is likely to be affected by the exploitation of 15 security defects due to the exploitation of 15 security defects in Apache, Atlassian, Citrix, Cisco, Paperinet, and Zoho. 00,000 Internet access available There is a system.
“The organization evaluates the exposure to these technologies, enhances potential risks, utilizes robust threat intelligence, maintains powerful patch management practices, and the Internet of these devices as much as possible. It is necessary to reduce control, such as minimizing exposure on the surface, “said Vulncheck.
Source link