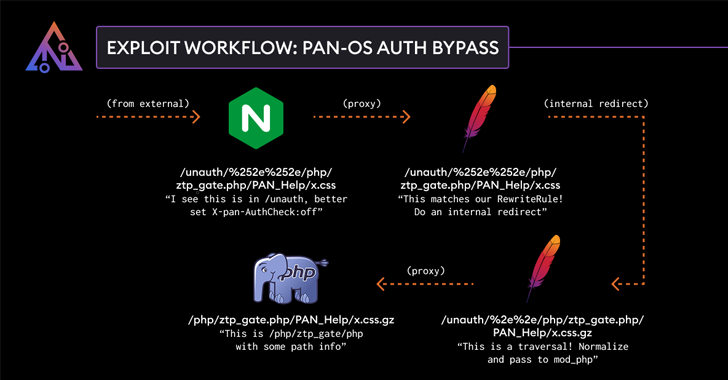
Palo Alto Networks addresses the advanced security flaws in Pan-OS software that can result in authentication bypassing.
The vulnerability tracked as CVE-2025-0108 has a CVSS score of 7.8 out of 10.0. However, if access to the management interface is restricted to a jumpbox, the score will drop to 5.1.
“Palo Alto Networks Pan-OS software authentication bypassing enables unauthorized attackers with network access to the management web interface, bypassing the required authentication for the PAN-OS management web interface, and allowing specific PHP scripts to be used. I’ll call you” in the advisory.
“While calling these PHP scripts does not enable remote code execution, it can have a negative impact on the integrity and confidentiality of PAN-OS.”
The vulnerability affects the following versions –
PAN-OS 11.2 <11.2.4-H4(> = Fixed to 11.2.4-H4) PAN-OS 11.1 <11.1.6-H1(> = Fixed at 11.1.6-H1) PAN-OS 11.0 (Fixed fixed version supported as end-of-life status was reached on 17 November 2024) PAN-OS 10.2 <10.2.13-H3(> = 10.2.13-H3 Pan-H3-H3-H3 <10.1.14-H9( > = Fixed in 10.1.14-H9)
Searchlight Cyber/Assetnote Security Researcher Adam Kues has been admitted to discovering and reporting the defect, and the security flaws are related to inconsistencies in the way the interface’s Nginx and Apache components handle incoming requests He said.

Palo Alto Networks has also sent out an update to resolve two other defects –
CVE-2025-0109 (CVSS score: 5.5) – Palo Alto Alto Networks Pan-OS Management Web interface uncertified file deletion vulnerability. Contains limited logs and configuration files that allow attackers who have access to the network to the management web interface to delete certain files as “who” users (PAN-OS versions 11.2.4-H4, 11.1.6 -H1, 10.2.13-H3, and 10.1.14-H9) CVE-2025-0110 (CVSS score: 7.3) – Palo Alto Networks Command Injection Vulnerability PAN-OS OpenConFig plugin is a PAN-OS management web interface Make GNMI requests to enable authenticated administrators with the ability to bypass system restrictions and execute arbitrary commands (fixed plugin version 2.1.2 with PAN-OS OpenConfig)
To mitigate the risk poses by vulnerabilities, we strongly recommend disabling access to the management interface from the Internet or untrusted network. Customers who do not use OpenConFig can choose to disable or uninstall the plugin from the instance.
Source link