Cybersecurity researchers are warning against a new campaign that leverages Web Injects to deliver new Apple MacOS malware known as FrigidStealer.
This activity stems from information stealing on other platforms such as Windows (Lumma Stealer or Deerstealer) and Android (Marcher) that were previously undocumented threat actors known as TA2727.
Ta2727 is “a threat actor who uses fake update theme lures to distribute various malware payloads,” says a report shared with Hacker News.

This is one of the newly identified threat activity clusters along with TA2726, and is rated as a malicious traffic delivery system (TDS) operator that facilitates traffic delivery for other threat actors to deliver malware. It’s there. The financially motivated threat actor is believed to have been active since at least September 2022.
According to the enterprise security company, TA2726 acts as the TDS for another threat actor called TA2727 and TA569. TA569 is responsible for the distribution of JavaScript-based loader malware, known as Socgholish (aka FakeUpdates), which often employs browser updates. A legitimate but compromised site.
“TA2726 is financially motivated and works with other financially motivated actors, such as TA569 and TA2727,” the company said. “This means that this actor is most likely responsible for the compromises of the web server or website that leads to injections operated by other threat actors.”
Both TA569 and TA2727 are distributed via websites compromised with malicious JavaScript website injections that mimic browser updates on web browsers such as Google Chrome and Microsoft Edge. They share similarities. What makes the TA2727 different is the use of attack chains that provide different payloads based on the recipient’s geography or device.
If a user visits an infected website in France or the UK on a Windows computer, they are prompted to download the MSI installer file that launches Hijack Loader (also known as Doiloader).
Meanwhile, the same fake update redirection when visiting from an Android device leads to the deployment of bank Trojans that have been detected in the wild for over a decade.

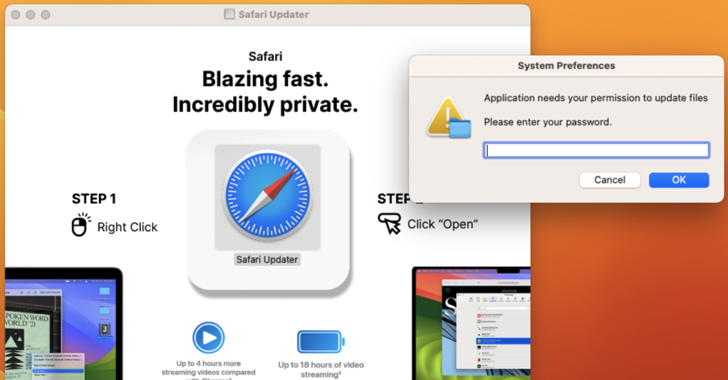
That’s not all. As of January 2025, the campaign was updated to target MACOS users outside of North America by redirecting to a fake update page where a new information steeler downloaded the codename FrigidStealer.
FrigidStealer installers, like other MacOS malware, require users to explicitly launch unsigned apps to bypass gatekeeper protection. The built-in MACH-O executable is then run to install the malware.
“The executable was written in GO and was signed ad hoc,” ProofPoint said. “The executable was built with the Wailsio project, which provides content to the user’s browser. This adds to the victim’s social engineering and means that the Chrome or Safari installer is legal.”
FrigidStealer is no different from the various steeler families targeting MACOS systems. Use Applescript to encourage users to enter their system passwords, thereby increasing the privilege to collect files and any kind of sensitive information from web browsers, Apple Notes, and Cryptocurrency-related apps.

“Actors use web compromises to provide malware that targets both corporate and consumer users,” the company said. “It makes sense for such web injection to deliver customized malware to recipients, including MAC users, which are not yet common in enterprise environments than Windows.”
This development is another completely undetectable, named Tiny FUD, where DENWP Research’s Tonmoy Jitu leverages name manipulation, dynamic link daemon (dyld) injection, and command-and-control (C2)-based command execution. This is because we revealed details about the MacOS backdoor.
It also follows the emergence of new information steeler malware such as Astral Stealer and Flesh Stealer. Both are designed to collect sensitive information, avoid detection, and maintain the persistence of compromised systems.
“Meat steelers are particularly effective at detecting virtual machine (VM) environments,” FlashPoint said in a recent report. “This will run on a VM to prevent potential forensic analysis and show you an understanding of security research practices.”
Source link