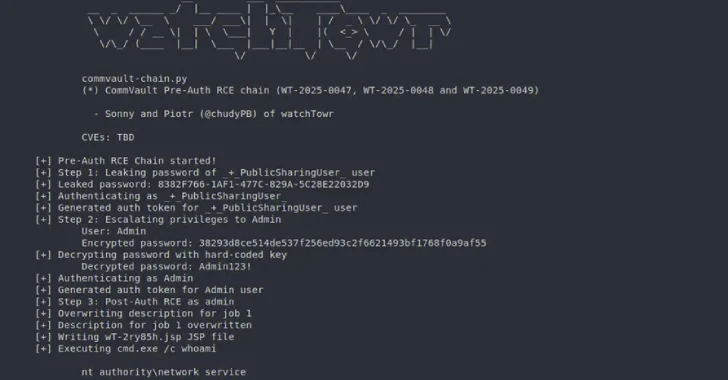
Commvault has released an update to address four security gaps that can be exploited to achieve remote code execution on sensitive instances.
The list of vulnerabilities identified in the Commvault version before 11.36.60 is as follows:
CVE-2025-57788 (CVSS score: 6.9) – A known login mechanism vulnerability allows unauthenticated attackers to make API calls without the need for user credentials. CVE-2025-57790 (CVSS score: 8.7) – Allows remote attackers to intrude to perform remote attacks via the Path Traversal Vulnerability CVE-2025-57791 (CVSS score: 6.9) that allows remote attackers to perform unauthorized file system access via past traversal issues. Insufficient input validation and becomes a valid user session for a low sovereign role

Watchtowr Labs researchers Sonny MacDonald and Piotr Bazydlo are acknowledged to have discovered and reported four security flaws in April 2025. All flagged vulnerabilities were resolved in versions 11.32.102 and 11.36.60. Commvault SaaS solutions are not affected.
In an analysis published Wednesday, the cybersecurity company said threat actors could create these vulnerabilities into two previous significant exploit chains to achieve code execution combining CVE-2025-57791 and CVE-2025-57790. CVE-2025-57790.
It is worth noting that the second Pre-Auth remote code execution chain will only succeed if the built-in administrator password has not been changed since the installation.
This disclosure comes almost four months after WatchTowr Labs reported a critical Commvault Command Center flaw (CVE-2025-34028, CVSS score: 10.0) that allows arbitrary code execution in affected installations.
A month later, the US Cybersecurity and Infrastructure Security Agency (CISA) added the vulnerability to its known Exploited Vulnerabilities (KEV) catalog, citing evidence of aggressive exploitation in the wild.
Source link