
Cybersecurity researchers show the evolution of widely used remote access called Asyncrat, which was first released on GitHub in January 2019 and has since served as the basis for several other variations.
“Asyncrat has solidified its position as a cornerstone of modern malware and as a broad threat that has evolved into a vast network of forks and variants,” ESET researcher Nikola Knežević said in a report shared with Hacker News.
“Its capabilities aren’t that impressive on its own, but it is the open source nature of Ashratt that truly amplified its impact. Its plugin-based architecture and ease of modification have caused the spread of many forks, further pushing the boundaries.”
The evolution of Asyncrat emphasizes its technological adaptability, but its real-world impact stems from the way it unfolded in opportunistic phishing campaigns and bundled with loaders such as Guloader and Smokeloader. These delivery methods allow for rapid delivery via cracked software, malicious ads, or fake updates, targeting users in both corporate and consumer environments. Without early detection, Asyncrat often functions as a staging tool for subsequent payloads such as ransomware and qualified steelers.
The C#-based malware that Nyan Cat first published on Github is equipped to allow attackers to steal screenshots, log keystrokes, credentials, and secretly command infected systems, remove data, and execute malicious instructions.

The simplicity and open source nature of modular tools, coupled with enhanced modular architecture and stealth capabilities, has not only been highly adaptable and difficult to detect, but has also been an attractive option for threat actors, as proven by countless campaigns distributing threats over the years.
The Slovak cybersecurity company said the “base” of Asyncrat was previously laid by another open source rat known as the Quasar rat (Cinarat or Yggdrasil), available on Github since 2015.
The two parts of the malware are combined by using the same custom cipher class used to decrypt the malware configuration settings. Since the release of Asyncrat, malware has produced a variety of variants, including DCRAT (aka DarkCrystal Rat) and Venom Rat.
DCRAT greatly improves Asyncrat, packs evasive technology to fly under the radar, and enhances the ability to collect webcam data, microphone recordings and discordant tokens alongside the module that encrypts files.
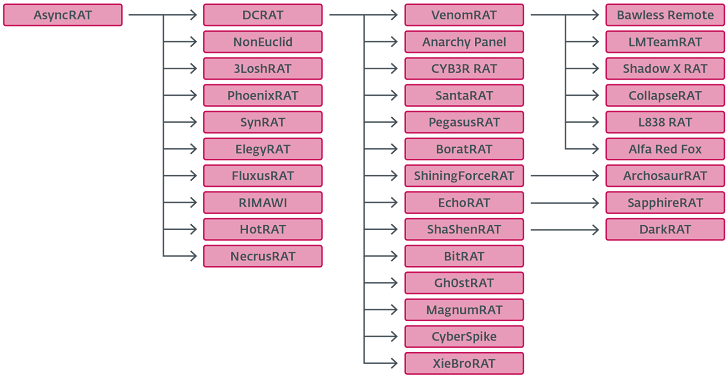
“DCRAT also implements evasive technologies such as AMSI and ETW patching, which work by disabling security features that detect and log malicious behavior,” ESET said. “Addi5onally features an anti-processing system that handles names that match the names of denilists.”
Meanwhile, Venom Rat is said to have been inspired by DCRAT, and at the same time packs its own unique features.
“They actually belong to the Quasar Rat family, but they are still different mice,” Anna Shirokova, a researcher at Rapid 7, said in her November 2024 analysis of Asincrats and Poisonous Rats.
ESET said it has identified a little-known variant of Asyncrat that collects plugins, geolocations, that incorporate plugins into brute-force SSH and FTP credentials, and acts as clippers by replacing clipboard data with attacker’s cryptocurrency wallet addresses.

Jasonrat introduces its own custom-made changes, including its ability to target systems based on country. Similarly, Xiebrorat features a browser’s credential steeler and a plugin that interacts with the Cobalt Strike server via a reverse connection. It also adapts to the Chinese market.
“The rise of Asyncrat and subsequent forks highlight the inherent risks of open source malware frameworks,” ESET said. “All of these forks not only extend Asyncrat’s technical capabilities, but also show how actors can quickly and creatively threaten open source code.”
“The broad availability of such a framework has significantly reduced the barriers to entry for aspiring cybercriminals, allowing even beginners to deploy sophisticated malware with this democratization of malware development to a minimum, and the landscape.”
This shift also helped to promote the rise of MAAS as malware. There, pre-configured Anne Crat Builders and Plug and Play Modules are openly sold on Telegram and Dark Web Forums. Attribution and defense are complicated by increasing duplication between open source malware, penetration testing tools, and commercial remote access frameworks.
For security teams, this means understanding how behavior detection, command and control (C2) analysis and futile persistence, clipboard hijacking, and qualification theft converges in modern malware campaigns.
Source link

