Cybersecurity researchers have discovered two Android Spyware campaigns called Prospy and Tospy, which are impersonating apps like Signal and Totok to target users in the United Arab Emirates (UAE).
Slovak Cybersecurity Company ESET said malicious apps will be distributed via fake websites and social engineering, ensuring unsuspecting users download them. Once installed, both spyware malware strains establish permanent access to the compromised Android device and remove data.
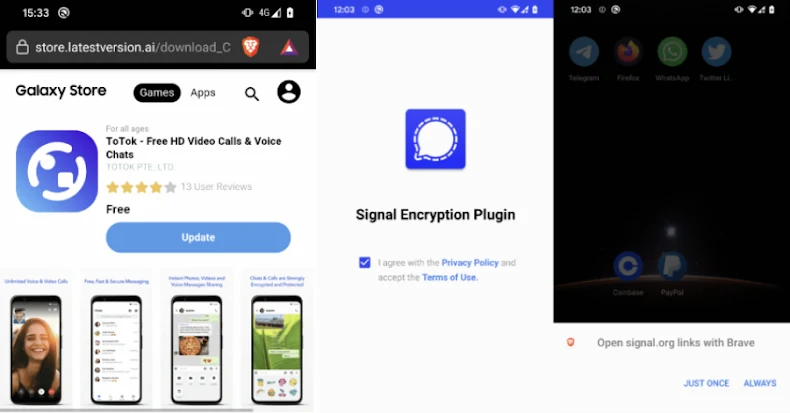
“Neither app, including spyware, was available in the official app store. Both require manual installation from third-party websites pose as legitimate services,” said Lukášštefanko, a researcher at ESET. In particular, one of the websites distributing the Tospy Malware family mimicked the Samsung Galaxy store and led users to manually download and install the malicious version of the Totok app. ”
The Prospy campaign, discovered in June 2025, is believed to have been ongoing since 2024, and claims to use deceptive websites pose as signals and upgrade to their respective apps: the Signal Encryption Plugin and Tokok Pro.
It’s no coincidence that Totok is used as a lure as it was removed from Google Play and Apple App Store in December 2019, as the app was removed from Google Play and Apple App Store, due to concerns that it acted as a spy tool for the UAE government and harvested user conversations, locations and other data.

The developers of Totok have since continued to insist that the deletion was “an attack on our company by people who hold dominant positions in this market,” and that the app does not spy on users.
The Rogue Prospy app is designed to request permissions to access contacts, SMS messages and files stored on your device. You can also remove device information.
ESET said it flagged another Android spyware family that was actively distributed in the wild and targeted users in the same region, just as Prospy was detected. The ongoing Tospy campaign, launched on June 30, 2022, is leveraging fake sites by impersonating the Totok app to deliver malware.
The region-focused campaign is focused on stealing sensitive data files, media, contacts and chat backups, and the TotoK Pro app is propagated to the Prospy cluster, redirecting users to the official web browser download page when tapped, and instructing them to download the actual app.

“This redirect is designed to reinforce the illusion of legitimacy,” ESET said. “The future launch of the malicious TOTOK Pro app will instead open the Real TotoK app and effectively mask the presence of Spyware. However, users will see that two apps are installed on their devices (TOTOK and TOTOK Pro).
Signal encryption plugins in a similar way include a “enable” button, where users access the signal and download and download legitimate encrypted messaging apps.[.]Organization site. However, unlike with Totok Pro, the Rogue Signal App icon will be changed by impersonating a Google Play service when the victim grants all the necessary permissions.
Regardless of the installed app, spyware embedded inside it secretly removes data before a user clicks or enables it. This includes device information, SMS messages, contact lists, files, and a list of installed applications.

“Like Prospy, Tospy has a procedure designed to deceive victims even more, designed to believe that the malware they just installed is a legitimate app,” Sitefunko said. “After a user launches a malicious TOTOK app, there are two scenarios: the official TOTOK app is installed on the device or not.”
“If the official TOTOK app is not installed on your device, Tospy will attempt to redirect users to the Huawei Appgallery via an already installed Huawei app or the default browser.

If the app is already installed on your device, it will display a fake screen that gives the impression that you are checking for app updates before launching the official TOTOK app seamlessly. However, in the background, it collects files that match user contacts, specific extensions, and device information and tots Data Backups (*.ttkmbackup).
To achieve persistence, both spyware families run a foreground service that displays persistent notifications, and use Android’s AlarmManager to repeatedly restart the foreground service if it quits, and automatically launch the background service required by restarting the device.
ESET said campaigns are being tracked differently due to differences in delivery methods and infrastructure, despite some commonalities in the malware being deployed. It is currently unknown who is behind the activity.
“Users should remain vigilant when downloading apps from unofficial sources, enable installations from unknown origins, and install apps and add-ons outside the official app store, especially when installing anything that they claim to enhance trustworthy services,” the company added.
Source link