Cybersecurity researchers are shedding light on a new, versatile malware loader called Castle Loaders, used in campaigns that distribute a variety of information steelers and remote access trojans (rats).
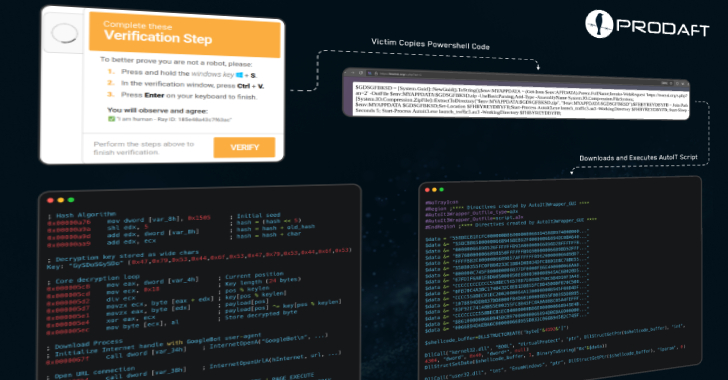
The activity employs a CloudFlare-themed Clickfix phishing attack and a fake Github repository opened in the name of a legitimate application, Swiss Cybersecurity Company Prodaft said in a report shared with Hacker News.
The first observed malware loaders in Wild earlier this year have been used to distribute other loaders such as Deerstealer, Redline, StealC, NetSupport Rat, Sectoprat, and even Hijack Loader.

“We employ dead code injection and packaging technology to prevent analysis,” the company said. “After unpacking at runtime, it connects to a C2 (Command and Control) server, downloads and runs the target module.”
The Castle Loader payload is distributed as a portable executable containing embedded shellcode, and then calls the main module of the loader that connects to the C2 server to fetch and run the next stage malware.
Malware distribution attacks rely on popular Clickfix techniques for domains that disguise software development libraries, video conferencing platforms, browser update notifications, or document verification systems, which ultimately trick users to copy and execute PowerShell commands that activate the infection chain.
Victims are directed to fake domains via Google search. At this point, we will provide a page containing fake error messages and Captcha validation boxes developed by the threat actor and ask you to execute a set of instructions to address the issue.

Alternatively, CastleLoader leverages fake Github repositories to mimic legal tools as distribution vectors, ensuring that users who unconsciously download them compromise their machines with malware instead.
“This approach leverages developers’ trust in GitHub and the trend of running install commands from repositories that appear to be well-reputed,” Prodaft said.
Prodaft said he observed that Hijack Loader was being delivered via Deerstealer and Castleloader, the latter propagating the Deerstealer variations as well. This suggests the overlap between these campaigns, despite the fact that they are organized by a variety of threat actors.

Since May 2025, the Castleloader campaign has utilized seven different C2 servers, with over 1,634 infection attempts recorded over the period. An analysis of the C2 infrastructure and web-based panels used to monitor and manage infections shows that as many as 469 devices have been compromised, resulting in a 28.7% infection rate.
“The Castleloader is a new, aggressive threat that is being adopted quickly in a variety of malicious campaigns and is being adopted rapidly to deploy a variety of other loaders and steelers,” Prodaft said. “Its sophisticated anti-analytical techniques and multi-stage infection processes highlight its effectiveness as a major distribution mechanism in the current threat landscape.”
“The C2 panel typically shows operational capabilities associated with the provision of malware As-a-Service (MAAS), suggesting that operators have experience in cybercrime infrastructure development.”
Source link