
The newly emerging ransomware (RAAS) gang, known as chaos, could be made up of former members of the black suit crew, as the latter’s dark web infrastructure is subject to law enforcement seizures.
Born in February 2025, Chaos is the latest participant in the ransomware landscape, carrying out big game hunting and double horror attacks.
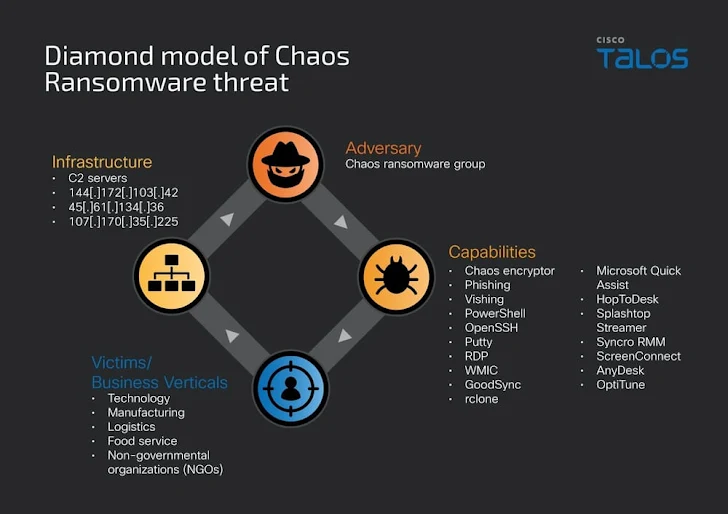
“The Chaos Raas actor launched a low-efford spam flood, escalated to voice-based social engineering for access, followed by RMM tool abuse and legal file sharing software for persistent connections for data removal.”
“Ransomware targets both multi-threaded, rapid selective encryption, anti-analytics techniques, and local and network resources to maximize impact while hampering detection and recovery.”
It is important to note that ransomware groups are unrelated to chaotic ransomware builder variants such as Yashma and Lucky_Gh0$T. This indicates that the threat actor is using the same name to soothe the confusion. The majority of the victims are in the US based on data from Ransomware.live.
Compatible with Windows, ESXi, Linux and NAS systems, Chaos has been observed to seek a $300,000 ransom from the victim in exchange for a “detailed intrusion summary with main kill chain and security recommendations.”
The attack includes a combination of phishing and voice phishing techniques, and gains initial access by tricking the victim into installing remote desktop software, particularly Microsoft Quick Assist.

Threat actors then carry out post-company discoveries and reconnaissance, then install other RMM tools such as AnyDesk, ScreenConnect, Optitune, Syncro RMM, Splashtop to establish persistent remote access to the network.
There is also a step to harvest the credentials, delete the PowerShell event log, and remove any security tools installed on the machine to reduce detection. Attacks culminate in ransomware deployments, but not before lateral movement and data removal using GoodSync.
Ransomware binaries support multi-threading, promote rapid encryption of both local and network resources, all block recovery efforts, and implement multi-layer anti-analysis techniques to avoid debugging tools, virtual machine environments, automated sandboxes, and other security platforms.
The link to the Black Suit comes from the commercial similarities adopted, including encryption commands, the theme and structure of ransom memos, and the RMM tools used. It is noteworthy that the Black Suit is a brand of the Royal Ransomware Group brand, and is a derivative of Conti in itself, highlighting the shape-changing nature of the threat.
The development is the same as the dark black suit website seized as part of a joint enforcement effort called Operation Checkmate. Visitors will be greeted by a splash screen that says, “The site was seized by a US Homeland Security Survey as part of a coordinated international law enforcement investigation.” There were no official statements from the authorities regarding the takedown.
In a related move, the US Federal Bureau of Investigation (FBI) and the Department of Justice (DOJ) have publicly announced the seizing of 20.2891382 BTC (now over $2.4 million) from the address of a cryptocurrency wallet associated with a member of the Chaos ransomware group known as Hors.
Chaos is the latest participant in the ransomware landscape and has also witnessed the arrival of other new stocks such as Backup, Bert, Blackfl, BQTLock, Dark 101, Gunra, Jackalock, Moscovium, Redfox, and Sinobi. Rated as being based on the infamous Conti Ransomware, Gunra has claimed 13 casualties since late April 2025.
“Gunra ransomware employs advanced evasive and anti-analytic techniques used to infect window operating systems, while minimizing the risk of detection,” Cyfirma said. “Its evasive capabilities include obfuscation of malicious activities, avoiding rule-based detection systems, strong encryption methods, ransom requests, and warnings to publish data in underground forums.”

Other recent ransomware attacks involve using DLL sideloads to drop lures like Nailaolocker and Clickfix to trick users into downloading and downloading malicious HTML application (HTA) files under the pretext of completing Captcha validation checks and spreading Epsilon Red Ransomware.
“The Epsilon Red ransomware, first identified in 2021, leaves ransom notes on infected computers that resemble Revil ransomware notes despite minor grammar improvements,” says Cloudsek.
According to the NCC Group, ransomware attacks in the second quarter of 2025 fell 43%, down from 2,074 in the first quarter of 2025. Qilin has become the most active ransomware group during the period, with 151 attacks and Akira has followed at 131, with 115, Safepay at 46, safepay at 46, and Lynx being estimated to be active in 2025.
“The amount of victims exposed at ransomware leak sites may be declining, but this does not mean that the threat will decrease,” he said, as the global head of threat intelligence for the NCC Group.
“While law enforcement crackdowns and leaked ransomware source code may be contributing factors in regards to lower activity, Ransomware Group is taking advantage of this opportunity to evolve through rebranding and using advanced social engineering tactics.”
Source link

