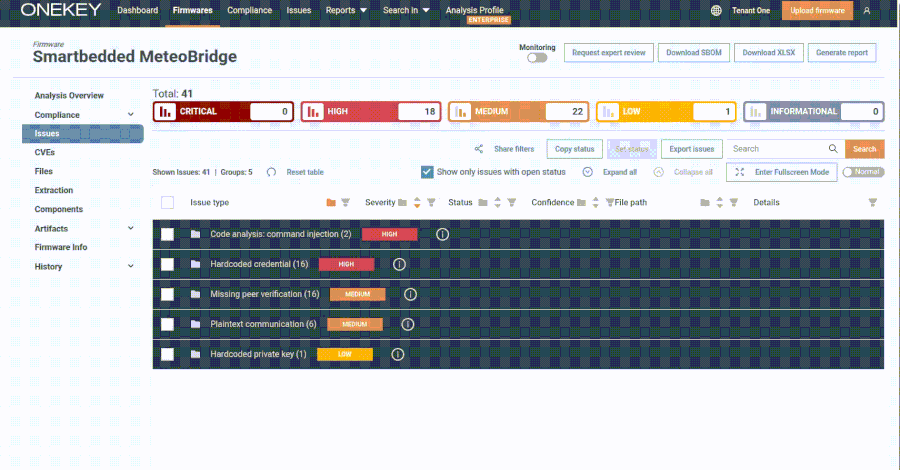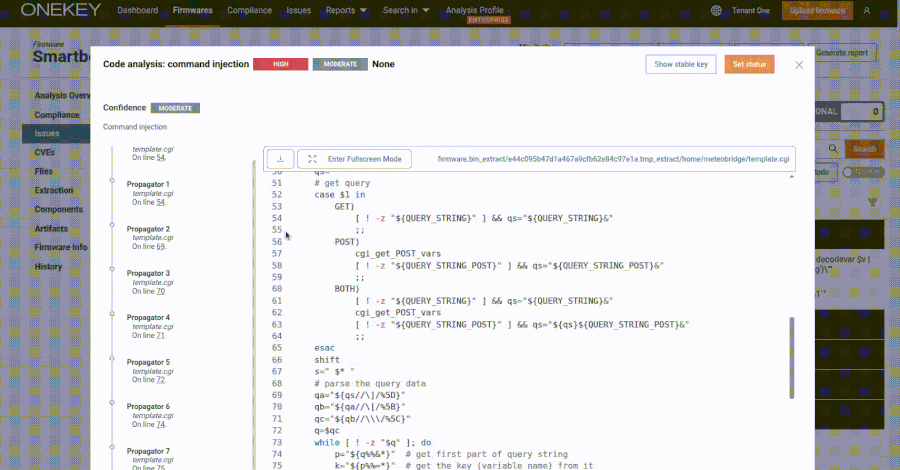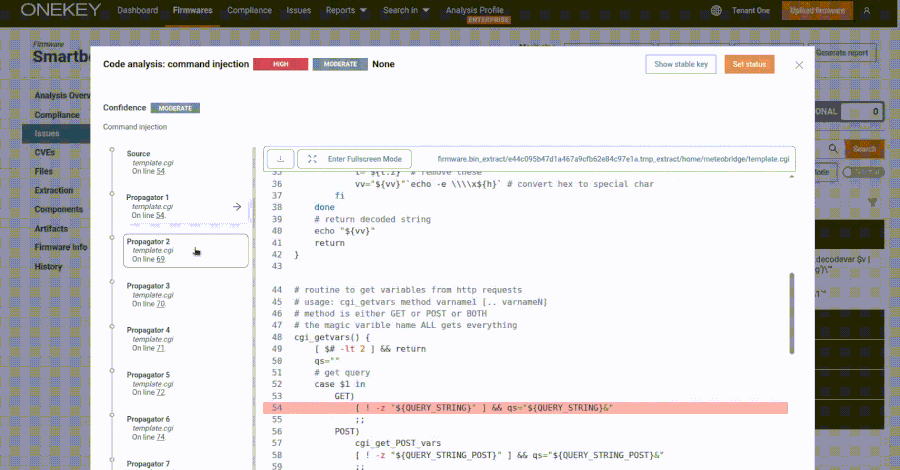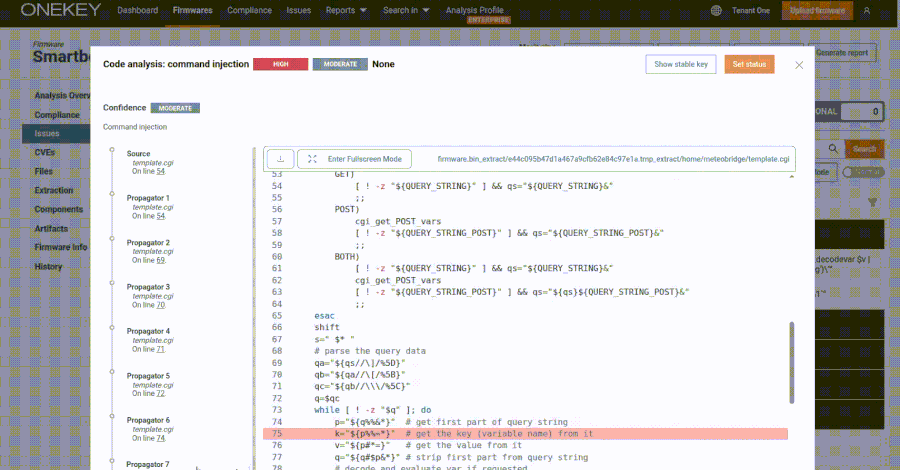
The US Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a high-strength security flaw affecting Meteobridge in smart beds in a known Exploited Vulnerability (KEV) catalog, citing evidence of active exploitation.
The vulnerability, CVE-2025-4008 (CVSS score: 8.7), is a case of command injection in the Meteobridge web interface, which can lead to code execution.
“SmartBedded Meteobridge contains a command injection vulnerability that allows remote, unauthorized attackers to gain arbitrary command execution with high privilege (root) on affected devices,” CISA said.
According to OneKey, which discovered and reported this issue in late February 2025, the Meteobridge web interface allows administrators to manage and control the system’s data collection through CGI Shell Scripts and web applications written in C.
Specifically, the web interface exposes the “template.cgi” script via “/CGI-bin/template.cgi”. This is vulnerable to command injection resulting from unstable use of evaluation calls, allowing attackers to provide specially written requests to execute arbitrary code.
Curl -i -U Meteobridge: Meteobridge \ ‘https://192.168.88.138/cgi-bin/template.cgi?$(id>/tmp/a) = whatever’
Additionally, OneKey said the vulnerability could be exploited by unauthenticated attackers due to the fact that CGI scripts are hosted in public directories without the need for authentication.
“Remote exploitation via malicious webpages is also possible, as it is a get request without custom headers or token parameters,” security researcher Quentin Kaiser said in May. “Just send the link to the victim, create an IMG tag using the src set and say “https://subnet.a/public/template.cgi?templateFile = $(command).'”

Currently, there are no public reports referring to how CVE-2025-4008 is being abused in the wild. The vulnerability was addressed in Meteobridge version 6.2, released on May 13, 2025.
Also, four other defects added to the KEV catalog by CISA –
CVE-2025-21043 (CVSS score: 8.8) – Samsung mobile devices contain vulnerabilities outside of LibimageCodec.Quram.so. CVE-2017-1000353 (CVSS score: 9.8) – Jenkins includes the need to remove untrusted data vulnerabilities that bypass denilist-based protection mechanisms to allow ruthless remote code execution. CVE-2015-7755 (CVSS score: 9.8) – Juniper Schoursos contains an inappropriate authentication vulnerability that allows unauthorized remote management access to devices. CVE-2014-6278, aka Shell Shock (CVSS Score: 8.8) – GNU BASH contains an OS command injection vulnerability that allows remote attackers to execute arbitrary commands through the environment in which they were created.
In light of active exploitation, a Federal Private Enforcement Division (FCEB) agency is required to apply the necessary updates by October 23, 2025 for optimal protection.
Source link