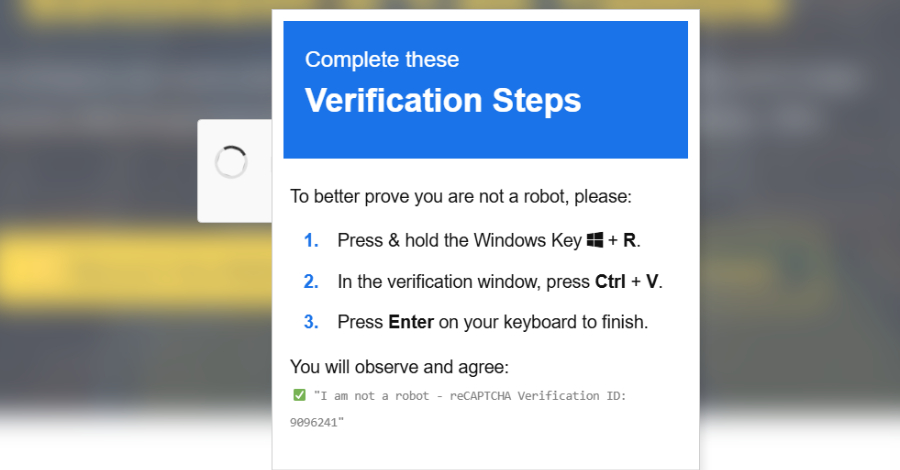
Cybersecurity researchers have detailed a new campaign that combines ClickFix-style fake CAPTCHAs with signed Microsoft Application Virtualization (App-V) scripts to distribute an information stealer called Amatera.
“Rather than directly invoking PowerShell, attackers use this script to control how execution begins, avoiding more common and easily recognized execution paths,” Blackpoint researchers Jack Patrick and Sam Decker said in a report released last week.
The idea is to convert App-V scripts into living-off-the-land (LotL) binaries that proxy PowerShell execution through trusted Microsoft components, hiding malicious activity.
The starting point for the attack is to trick users into installing Windows[ファイル名を指定して実行]A fake CAPTCHA verification prompt designed to paste and execute malicious commands into the dialog. However, this is where this attack diverges from the traditional ClickFix attack.
Rather than directly invoking PowerShell, the specified command exploits a signed Visual Basic script associated with App-V, “SyncAppvPublishingServer.vbs,” which uses “wscript.exe” to retrieve and execute an in-memory loader from an external server.
Please note that the misuse of “SyncAppvPublishingServer.vbs” is not new. In 2022, two different threat actors from China and North Korea, tracked as DarkHotel and BlueNoroff, were observed leveraging the LOLBin exploit to covertly execute PowerShell scripts. However, this is the first time this has been observed in a ClickFix attack.
MITER notes that in the ATT&CK framework, “adversaries could exploit SyncAppvPublishingServer.vbs to circumvent PowerShell execution restrictions and ‘live off the land’ to evade defenses.” “Proxed execution may serve as a trusted/signed alternative to invoking ‘powershell.exe’ directly.”
Using App-V scripts is also important. This is because virtualization solutions are only built into Enterprise and Education editions of Windows 10 and Windows 11, and the latest Windows Server versions. Not available for Windows Home or Pro installations.
On Windows operating systems where App-V is not present or enabled, command execution will fail completely. This also indicates that enterprise management systems are likely to be the primary target of the campaign.
The obfuscated loader performs checks to ensure it is not running in a sandboxed environment and fetches configuration data from public Google Calendar (ICS) files, effectively turning a trusted third-party service into a dead drop resolver.

“Externalizing configuration in this way allows attackers to quickly rotate infrastructure or adjust delivery parameters without having to redeploy earlier stages of the chain, reducing operational friction and increasing the longevity of the initial infection vector,” the researchers noted.
Parsing a calendar event file yields additional loader stages, including a PowerShell script that acts as an intermediate loader to run the next stage, another PowerShell script, directly in memory. This step will retrieve a PNG image from a domain like “gcdnb.pbrd”.[.]”Ko” and “Iri”[.]io” is sent via the WinINet API, which hides an encrypted and compressed PowerShell payload.
The resulting script is decrypted, GZipped in memory, executed using Invoke-Expression, and ultimately a shellcode loader designed to launch the Amatera Stealer.
“What makes this campaign interesting is not a single trick, but how carefully thought out everything is when chained together,” Blackpoint concluded. “From requiring manual interaction by the user, to validating the state of the clipboard, to retrieving live configuration from a trusted third-party service, each step strengthens the last.”
“As a result, the execution flow will only proceed if it unfolds (almost) exactly as the attacker expects, making both automated detonation and casual analysis significantly more difficult.”
Evolution of ClickFix: JackFix, CrashFix, GlitchFix
The disclosure comes as ClickFix became one of the most widely used initial access methods last year, accounting for 47% of attacks observed by Microsoft.

A recent ClickFix campaign targets social media content creators, claiming they are eligible for a free verified badge and instructing them in a video to copy an authentication token from a browser cookie into a fake form to complete a supposed authentication process. The embedded video tells users to “do not log out for at least 24 hours” to keep their authentication tokens valid.
According to Hunt.io, the campaign has been active since at least September 2025 and is estimated to have used 115 web pages and eight exposed endpoints across the attack chain. The primary targets of this activity include creators, monetized pages, and businesses seeking verification, with the ultimate goal being to facilitate account takeover after token theft.
“Defending against ClickFix technology is uniquely difficult because the attack chain is built almost entirely on legitimate user actions and the exploitation of trusted system tools,” Martin Zugec, Bitdefender’s director of technical solutions, said in a report last month. “Unlike traditional malware, ClickFix turns the user into the first access point, making the attack appear benign from an endpoint defense perspective.”

ClickFix is also constantly evolving, leveraging variants such as JackFix and CrashFix to trick victims into infecting their machines. Operators use several methods to try to trick targets into executing commands, but the growing popularity of social engineering techniques has paved the way for ClickFix builders, which are advertised on hacker forums for between $200 and $1,500 per month.
A recent entrant into this threat landscape is ErrTraffic. ErrTraffic is a traffic distribution system (TDS) designed specifically for campaigns like ClickFix to break compromised websites that have been injected with malicious JavaScript and suggest fixes that address non-existent issues. The technology is codenamed GlitchFix.
Malware as a Service (MaaS) supports three different file distribution modes that use fake browser update alerts, fake “system fonts required” dialogs, and fake system font missing errors to trigger execution of malicious commands. ErrTraffic is explicitly blocked from running on machines located in Commonwealth of Independent States (CIS) countries.

“ErrTraffic not only displays fake update prompts, but also actively destroys the underlying page to make victims believe that something is truly wrong,” Censys said. “It also applies CSS transformations that make everything seem broken.”
ClickFix has also been employed by the attackers behind the ClearFake campaign. This campaign is known to infect sites with fake web browser update decoys on compromised WordPress and distribute malware. ClearFake’s use of ClickFix was first recorded in May 2024, leveraging a CAPTCHA challenge to deliver Emmenhtal Loader (aka PEAKLIGHT), and later dropping Lumma Stealer.
This attack chain also leverages another known technique called EtherHiding, which uses a smart contract on Binance’s BNB Smart Chain (BSC) to obtain the next stage of JavaScript code, and ultimately injects a fake ClickFix CAPTCHA obtained from another smart contract into the web page. At the same time, the final stage avoids reinfection of already infected victims.

Similar to the Amatera Stealer attack, the ClickFix command copied to the clipboard exploits ‘SyncAppvPublishingServer.vbs’ to obtain the final payload hosted on the jsDelivr Content Delivery Network (CDN). According to Expel’s analysis of the ClearFake campaign, 147,521 systems may have been infected since late August 2025.
“One of the many factors security products use to determine whether an action is malicious is whether it is performed by a trusted application,” said security researcher Marcus Hutchins. “In this case, ‘SyncAppvPublishingServer.vbs’ is a default Windows component, and only TrustedInstaller (a highly privileged system account used internally by the operating system) can modify the file. Therefore, the file and its behavior alone are usually not suspicious.”
“It is unlikely that an organization or EDR will completely block SyncAppvPublishingServer.vbs from launching PowerShell in hidden mode, as this would make the component unusable for its intended purpose. As a result, an attacker could exploit the command line injection bug in SyncAppvPublishingServer.vbs to execute arbitrary code through a trusted system component.”

Expel also characterizes this campaign as highly sophisticated and highly evasive due to its reliance on blockchain and common CDNs, as well as the use of PowerShell code execution in memory to avoid communicating with infrastructure that is not a legitimate service.
Censys describes the widespread fake CAPTCHA ecosystem as “a fragmented, rapidly changing exploitation pattern that uses trusted web infrastructure as a delivery surface,” with Cloudflare-style challenges acting as a handoff to PowerShell commands, VB scripts, clipboard-driven execution of MSI installers, and even browser-native frameworks like Matrix Push C2.
“This is consistent with a broader shift to life off the web, including security-themed interfaces, platform-sanctioned workflows, and the systematic reuse of conditioned user behavior to deliver malware,” the attack surface management company said. “An attacker does not need to compromise a trusted service; they inherit trust by operating within the familiar validation and browser workflows that users and tools are trained to accept.”
Source link