Cybersecurity researchers have discovered more than 12 security vulnerabilities affecting Tridium’s Niagara framework, which allows attackers on the same network to compromise their systems under certain circumstances.
“If the Niagara system is misconfigured, these vulnerabilities are fully exploitable, thereby disabling encryption for certain network devices,” Nozomi Networks Labs said in a report published last week. “If they chain together, they can allow attackers who can access the same network – they can compromise the Niagara system, such as intermediate (MITM) locations.”
Developed by Tridium, Honeywell’s independent business entity, the Niagara Framework is a vendor-neutral platform used to manage and control a wide range of devices from various manufacturers, including HVAC, lighting, energy management, security, and more, making it a valuable solution in building management, industrial automation and smart infrastructure environments.
It consists of two main components: A platform is the underlying software environment that provides the necessary services to create, manage, and create, manage, and run stations that communicate and control with connected devices and systems.

If a Niagara system is misunderstood and disables encryption on network devices, opening doors to lateral movement and wider operational disruptions, affecting safety, productivity and service continuity, the vulnerabilities identified by the Nozomi network can be exploited.
Below is the most serious problem:
CVE-2025-3936 (CVSS score: 9.8) – Incorrect permission assignment for critical resource CVE-2025-3937 (CVSS score: 9.8) CVE-2025-3938 (CVSS score: 9.8) – CVE-1tographic Step cve-20-25-13941 (CVSS score: 9.8) 9.8) – Inappropriate handling of windows: Data Alternative Data Stream CVE-2025-3944 (CVSS score: 9.8) – Incorrect permission assignment for critical resource CVE-2025-3945 (CVSS score: 9.8) – CVE-20-3943 (CVS faits: cvs feat in a cve-205-3943 (sensitive query string)
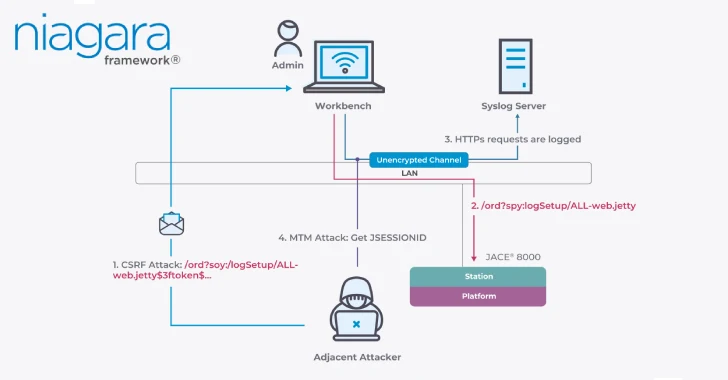
Nozomi Networks said it could create an exploit chain that combines CVE-2025-3943 and CVE-2025-3944.
Specifically, an attacker can weaponize CVE-2025-3943 to intercept anti-CSRF (cross-site request forgery) that updates the token in scenarios where the syslog service is enabled.
Token-armed threat actors can trigger CSRF attacks and direct them to administrators to visit specially-created links that fully record the content of all incoming HTTP requests and responses. The attacker then extracts the administrator’s JSessionID session token and uses it to connect to Nier Glass Station with full height privileges, creating a new backdoor admin user for persistent access.
The next phase of the attack involves an interim (AITM) attack by abusing administrative access, downloading the private key associated with the device’s TLS certificate, and taking advantage of the fact that both the station and the platform share the same certificate and key infrastructure.
By controlling the platform, attackers were able to leverage CVE-2025-3944 to facilitate root-level remote code execution on the device and achieve a complete takeover. Following responsible disclosure, this issue is addressed in the Niagara Framework and Enterprise Security versions 4.14.2U2, 4.15.U1, or 4.10U.11.
“Niagara can often represent a valuable target as it connects critical systems and, in some cases, bridges IoT and information technology (IT) networks,” the company said.
“Given the critical features that can be controlled by Niagara-powered systems, these vulnerabilities can pose high risks to operational resilience and security if not set for each tridium cure guidelines and best practices.”
This disclosure occurs because several memory corruption flaws have been discovered in the P-NET C library, an open source implementation of the PROPINET protocol for IO devices.
“In fact, using CVE-2025-32399, attackers can force their CPUs to infinite loops and consume 100% of their CPU resources,” says Nozomi Networks. “Another vulnerability tracked as CVE-2025-32405 will allow an attacker to write across connection buffer boundaries, destroy memory, and render the device completely unusable.”

The vulnerability was resolved in library version 1.0.2, released in late April 2025.
In recent months, several security flaws have been unearthed on Rockwell Automation PowerMonitor 1000, Bosch Rexroth Ctrlx Core, and Inaba Denki Sangyo’s IB-MCT001 cameras.
“The successful exploitation of these vulnerabilities allows attackers to obtain product login passwords, obtain unauthorized access, tamper with product data and modify product settings,” the US Cybersecurity and Infrastructure Security Agency (CISA) said in an advisory to IB-MCT001 Flaws.
Source link