Cybersecurity researchers have been bringing attention to a series of cyberattacks targeting African financial organizations since at least July 2023, using a combination of open source and public tools to maintain access.
Palo Alto Networks Unit 42 refers to “Cl” to “Cluster”, and “CRI” to “Crimer Votivation” and “Cl” to “CL” and “CRI”.
The ultimate goal of the attack is suspected to be to obtain initial access and sell it to other criminals at underground forums, and make threat actors an initial access broker (IAB).
“Threat actors copy signatures from legal applications to forge file signatures, disguise toolsets, and mask malicious activities,” said researchers Tom Factorman and Guy Levy. “Threat actors often spread legitimate products for malicious purposes.”

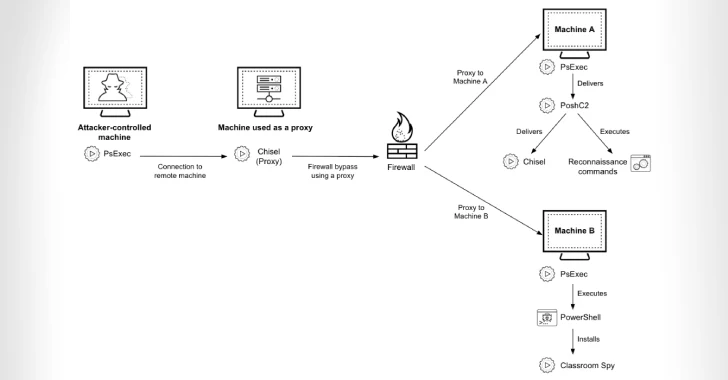
The attack is characterized by the deployment of tools such as POSHC2 for Command and Control (C2), chisels for tunnels of malicious network traffic, and classroom spys for remote management.
The exact method used by threat threats to violate the target network is not clear. Once scaffolding is obtained, the attack chain deploys Mesh Central Agent and subsequent classroom spies to command the machine, bypassing POSHC2 to other Windows hosts on the compromised network, and bypassing and spreading POSHC2.
For side step detection efforts, payloads are passed as legitimate software using icons from Microsoft Teams, Palo Alto Networks Cortex and Broadcom VMware Tools. POSHC2 lasts in the system using three different methods –
Setting up a service to save Windows Shortcuts (LNK) files to a tool in the startup folder using a task scheduled with the name “Palo Alto Cortex Services.”
In some incidents observed by cybersecurity companies, the threat actor is said to have stolen user credentials and is used to set up a proxy using POSHC2.

“POSHC2 can use a proxy to communicate with command and control (C2) servers, and the threat actor appears to have tailored some of the POSHC2 implants specifically for the target environment,” the researchers say.
This is not the first time POSHC2 has been used in an attack targeting Afrance Services. In September 2022, Checkpoint detailed a spear phishing campaign called DangerseSavanna to provide Metasploit, POSHC2, DWSERVICE and ASYNCRAT, targeting financial and insurance companies in the Ivory Coast, Morocco, Cameroon, Senegal and Togo.

The disclosure has shed light on a new ransomware group called DiRe Wolf, which has already claimed 16 casualties throughout the US, Thailand, Taiwan, Australia, Australia, Bahrain, Canada, India, Italy, Peru and Singapore since its arrival last month. The top target sectors are technology, manufacturing and financial services.
An analysis of Dire Wolf Locker reveals what is written in Golang, with the ability to disable system logging, terminate the hard coding list for 75 services and 59 applications, and remove Shadow Copies to block recovery efforts.
“While there is no initial access, the reconnaissance or lateral movement techniques used by Dire Wolf are known at this time, but organizations will follow appropriate security practices to allow monitoring of the technologies revealed in this analysis,” the company said.
Source link