It has been observed that threat actors who harness deceptive social engineering tactics known as Clickfix will deploy the versatile backdoor code name Cornflake.v3.
Mandiant, owned by Google, described the activity it tracks as UNC5518. This is described as part of the access scheme as access as a service that uses fake Captcha pages as lures to provide initial access to the system, and is then monetized by other threat groups.
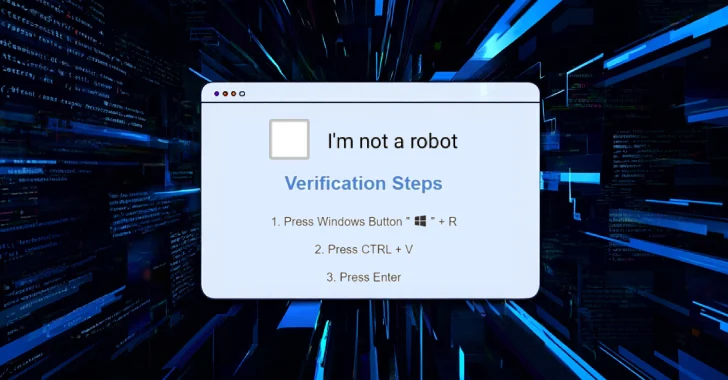
“The first infection vector, called Clickfix, copies a malicious PowerShell script to the user on the compromised website, and[Windows実行]It involves directing you to run through a dialog box,” Google said in a report published today.

The access provided by UNC5518 is evaluated as being utilized by at least two different hacking groups, UNC5774 and UNC4108, to initiate the multi-stage infection process and drop additional payloads –
UNC5774, another financially motivated group that provides cornflakes as a way to deploy various subsequent payloads is the threat actors with unknown motivation to deploy tools such as Voltmarker and NetSupport rats using PowerShell;
The attack chain can start with the victim landing a fake Captcha verification page after interacting with search results that use search engine optimization (SEO) addiction or malicious ads.

The user is then fooled by the malicious PowerShell command execution by launching the Windows Run dialog and runs the next-stage dropper payload from the remote server. The newly downloaded script checks whether it is running within a virtualized environment and eventually launches Cornflake.v3.
Observed in both JavaScript and PHP versions, Cornflake.v3 is a backdoor that supports the execution of payloads over HTTP, including executables, dynamic link libraries (DLLs), JavaScript files, batch scripts, and PowerShell commands. It also allows you to collect basic system information and send it to an external server. To avoid detection, traffic is proxyed through the CloudFlare tunnel.
“cornflake.v3 is an updated version of cornflake.v2, and shares a significant portion of the codebase,” said Mandiant researcher Marco Gali. “Unlike V2, which acts only as a downloader, V3 has host persistence via the registry execution key and supports additional payload types.”
Both generations are significantly different from C-based downloaders that use TCP sockets for Command and Control (C2) communication and have the ability to perform DLL payloads.
Host persistence is achieved through changes to the Windows registry. At least three different payloads will be delivered via Cornflake.v3. It consists of an active directory reconnaissance utility, a script to harvest qualifications via KerberoAsting, and another backdoor called Windytwist.sea.
It has also been observed that the selected version of Windytwist.sea is attempting to move laterally across the network of infected machines.

“To mitigate the execution of malware via Clickfix, organizations can as much as possible.[Windows実行]You need to disable the dialog box,” Galli said. “Regular simulation exercises are important to counter this and other social engineering tactics. Additionally, robust logging and monitoring systems are essential to detect subsequent payload executions, such as those related to Cornflake.v3.”
USB infection will remove Xmrig Miner
This disclosure comes when threat intelligence companies detail the ongoing campaign from September 2024 onwards to infect other hosts and employ USB drives to deploy cryptocurrency miners.

“This demonstrates the continued effectiveness of initial access through infected USB drives,” Mandiant said. “The low cost and the ability to bypass network security make this a compelling option for attackers.”
The attack chain begins when the victim is tricked into running a Windows Shortcut (LNK) on the compromised USB drive. LNK files allow you to run Visual Basic Script, which is also in the same folder. The script launches a batch script to start an infection –
A C++ DLL launcher that starts running other malicious components such as Dirtybulk, Cutfail, C++ malware dropper responsible for decrypting and installing malware on systems such as HighReps and Pumpbench, and a C++ backdoor that facilitates reconnaissance, such as third libraries like OpenSSL, libcurl, winpthreadgc high high reptes flesecens aa withreadgc high repreps, Pumpbench, a C++ backdoor that facilitates reconnaissance, such as PostgreSQL database servers, provides remote access, and downloads Xmrig Xmrig, an open source software for mining cryptocurrencies such as Monero, Dero, Ravencoin.
“Infecting USB drives spreads the pump bench,” Mandiant says. “Scan the system on available drives and then create batch files, VBScript files, shortcut files, and DAT files.”
Source link