Russian companies are being targeted as part of a massive phishing campaign designed to provide known malware called DarkWatchman.
The targets of the attack include entities in the media, tourism, finance and insurance, manufacturing, retail, energy, communications, transportation and biotechnology sectors, Russian cybersecurity company F6 said.
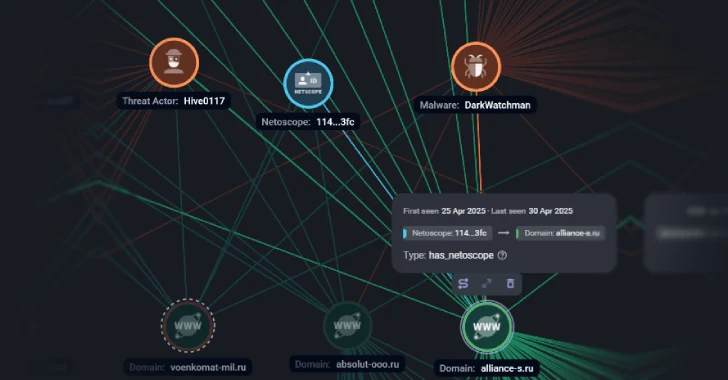
The activity is rated by IBM X-Force as a financially motivated group called HIVE0117, which is attributed to an attack on Russian users across the electronic, electronic and industrial sectors of Lithuania, Estonia and Russia.
Then, in September 2023, Dark Watchman malware was used again in a phishing campaign aimed at the energy, finance, transportation and software security industries based in Russia, Kazakhstan, Latvia and Estonia.
Russian banks, retailers and markets, telecom operators, agricultural industry companies, fuel and energy companies, logistics companies and IT companies were again elected DarkWatchman in November 2023 using Courier Delivery-themed lures.

DarkWatchman, a JavaScript-based remote access trojan, can collect key logs, system information, and deploy secondary payloads. It was first documented in December 2021.
“The fi thin nature of DarkWatchman’s malware, as well as the use of JavaScript and Keylogger written in C#, and the ability to remove traces of its existence when instructions compromise, are evidence of a somewhat refined feature in 2023.”
The latest attack set includes sending phishing emails containing password-protected malicious archives. This provides a variant of DarkWatchman with improved ability to avoid detection after opening.
New Sheriff’s Backdoor Targeted Ukraine
Disclosure occurs when IBM X-Force stated that an unspecified entity within Ukraine’s defense division was targeted in the first half of 2024 by an unspecified entity called a sheriff, whose previously undocumented Windows backdoors were targeted.
“Threat actors have used Ukrainian popular news portals at Ukraine at Ukraine to host the sheriff’s backdoor,” security researcher Golomur said in a report published in late March 2025.
“Malware focuses on maintaining a low profile designed for long-term compromises while removing data and taking screenshots.”

It is suspected that the website may have been violated in early March 2024 to stage the malware. The Sheriff is equipped to download and manage multiple components, including screenshot modules with commands and configuration values received as comments in ZIP files.
“The access of threat actors to Ukraine’s biggest news portal will work with increased obfuscation, positioning them to carry out various impactful attacks,” Mule said. “In this particular incident, the threat actor may have abused a trusted domain to stage the malware without question.”
The backdoor is also equipped with a “suicide” function. This stops all activity when called by the operator remotely and removes directories containing malware and folders on the dropbox used for command and control (C2) communication.

IBM pointed out that certain aspects of the malware overlap with Turla’s Kazuar and Curtch aspects, as well as those of GroundBait’s Operation Prikormka and Bad Magic’s Cloudwizard.
“To both CloudWizard and the sheriff, “Getsettings” https://thehackernews.com/ “get_settings” will get the configuration of each module,” the company said. “CloudWizard, Prikormka, and the sheriff share the same screenshots, which take 15 minutes apart. The file list modules for CloudWizard and Prikormka are called “trees.”
The backdoor discovery follows a report from the Ukrainian provincial services of Special Communications and Information Protection (SSSCIP) warning that the number of incidents increased by 48% in the second half of 2024 (2,576) compared to the previous six months (1,739).
In total, 4,315 cyber incidents were registered in 2024, up from 1,350 in 2021, 2,194 in 2022 and 2,543 in 2023. Meanwhile, the number of serious and altitude incidents fell to 59, down from 1,048 in 2023 and 1,048 in 2023, 367, to 59.
“Russian hackers are actively implementing automation by employing supply chain attacks in penetration through software vendors and combining espionage and sabotage techniques,” SSSCIP said. “The main focus of the attack is a collection of intelligence that can affect frontline operational situations. In particular, the enemy is targeting situational awareness systems and specialized defense companies.”
Source link