Most security tools can’t see what happens within the browser, but that’s where most of the work and the risks live now. Deciding how security leaders will close that gap is often faced with choice. Deploy a dedicated enterprise browser or add an enterprise-grade control layer to a browser that employees already use and trust.
The Ultimate Battle: Enterprise Browser vs. Enterprise Browser Extension validates this choice to show nine “rounds”, adoption, data protection, productivity, management overhead, remote access, zero trust linement, supply chain security, future reads, where each approach will expand and where trade-offs will occur.
Each round compares the two models using a practical enterprise scenario, making it easier to see what you can do, as well as performance at scale.
The browser has become a workspace
Browsers have become the primary workspace for enterprise users. This is where you will create, access and move via COPY/PASTE actions and move more and more through copy/paste actions, submit form, upload, download, and GENAI prompts.

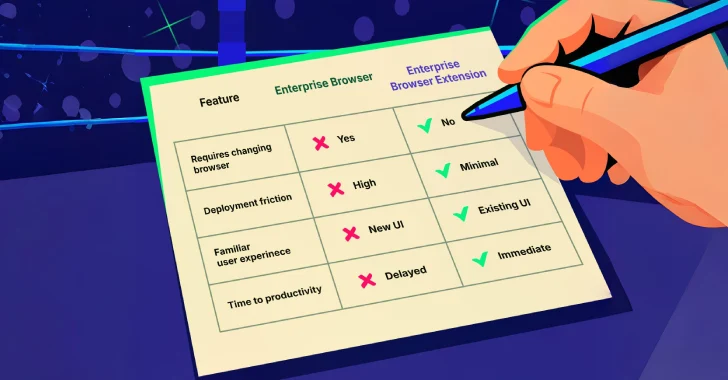
The habits of the default browser are deeply ingrained. Forcesing the switch slows adoption, especially in hybrid environments where unmanaged devices and contractors play the role.
The expansion ecosystem is valuable and risky. It not only expands functionality, but also expands the potential attack surface. This guide reveals that neither the Enterprise Browser nor the Enterprise Browser extension will replace the rest of the security stack. One of the clearest examples of that gap is how the use of Genai works in your browser.
genai: Use case to test both models
With the adoption of Genai Tools’ enterprise, browser security has introduced shocking and in-session risks.
Your own code, business plans, and confidential records can be pasted at a prompt without an audit trail. Because the context of identity is important, controls must distinguish between personal accounts and work in real time. Coverage must be extended to unmanaged devices, third parties, and temporary access users. Extended governance needs to balance productivity with the ability to detect and limit dangerous behavior.
This guide uses such scenarios to stress-test both approaches in multiple rounds, revealing where coverage, depth of control, and operational overhead diverges.
Enterprise Browser vs Secure Browser Extension: Side-by-side comparison in 9 rounds

The Ultimate Battle organizes comparisons into rounds related to nine manipulations. Rather than listing features, we test how each model responds to actual conditions, from enabling BYOD access without eroding data usage to managing risky extensions without disrupting workflows.
Where differences are most clearly shown:
coverage
Enterprise Browser: Strong control within its own environment, but adoption relies on users toggling defaults to maintain sensitive activity within the EB. Secure Browser Extension: Runs in mainstream browsers (Chrome/Edge) to cover managed, unmanaged, and contractor devices without modifying the user’s primary workflow.
Control and Enforcement
Enterprise Browser: Deep Guardrails within EB, including session separation and strict separation of work and personal contexts. Enterprise Browser Extensions: DOM-level visibility, form fill, upload, download, and Genai prompts to alert, edit, or apply blocks to copy/paste. Policies can be bound by identity that distinguishes between business and individual activities.
Integration and operation
Enterprise Browser: Clean integration while still in use within EB, but requires parallel browser management and associated support. Enterprise Browser extension: Stream Browser-Layer Telemetry to SIEM/XDR, affecting IAM/ZTNA decisions, and centrally updating users without reorganizing them with new browsers.
Make decisions about enterprise browsers and secure browser extensions
This guide is designed to help security teams turn their abstract strengths and weaknesses into decisions that fit their environment and risk profiles. The choice of enterprise browser and extensions for enterprise browsers is not purely technical. This is to balance depth of control and coverage width, taking into account adoption patterns and long-term manageability.
Comparison documents present these trade-offs in a structured, scenario-driven format, allowing teams to map to their own environments and make informed calls. Download the full comparison to see how each approach works where it matters most to your organization.
Source link