Hackers have violated Telemessage, an Israeli company that builds custom versions of messaging apps such as Signal, WhatsApp and Telegram for clients, including the US government. The stolen data includes direct messages and group chat content sent through these modified platforms, according to reports from 404 Media.
“The data stolen by hackers include direct messages and group chat content sent using that signal clone. It also includes modified versions of WhatsApp, Telegram and Wechat. Recently, Telemessage was at the heart of a wave of media coverage after Mike Waltz accidentally revealed that he used the tool in a cabinet meeting with President Trump.”
According to WikiLeaks, hackers gained access to Telemessage’s backend admin panel using credentials drawn from previously intercepted data. The violation linked archived chat logs and contact information to US officials.
Telemessage Hacked: Israeli Company Correction Signal App publishes archived US government messages
This is not just about the vendor being compromised. It emphasizes a deeper problem. Modified versions of signals used by some government agencies do not store end-to-end encrypted signals. Messages were reportedly not encrypted between the app and the archive system controlled by Telemessage customers. Once saved, you can read the message.
The original signal team was distanced from the violation. In a statement to the 404 media, Signal said:
“We cannot guarantee the privacy or security properties of an unofficial version of a signal.”
The revised app reportedly was adopted by US agencies during the Trump administration, but it is unclear how widely used it was or whether it is still in use.
The Israeli company behind the revised signaling app used by the Trump administration has been hacked.
Telemessage’s backend panel was accessed using credentials found in intercepted data. The hackers have released archived messages and contact information for US officials.
Hack is revealed…pic.twitter.com/ugedjrrr3h
– WikiLeaks (@wikileaks) May 5, 2025
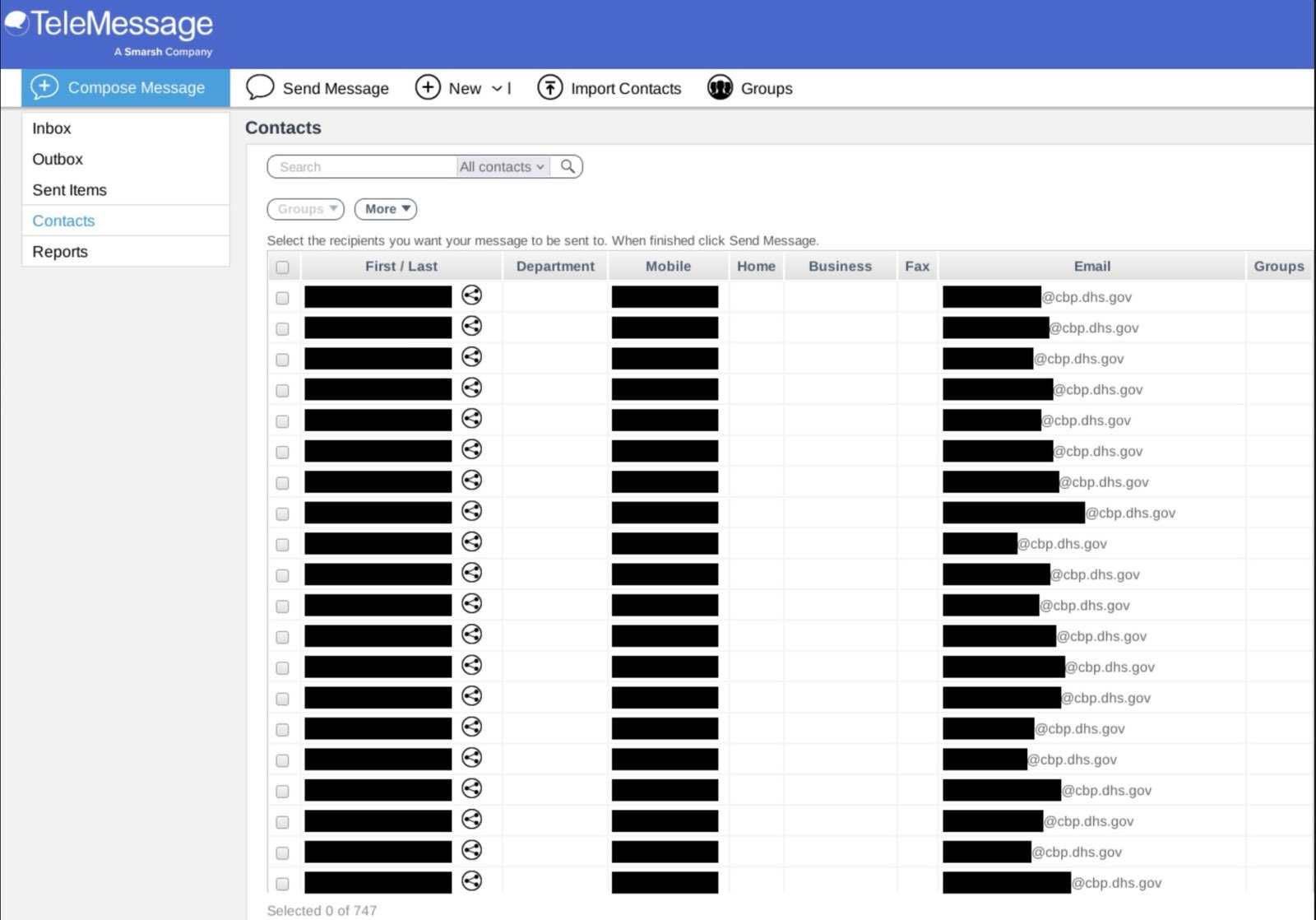
Screenshots of government email addresses published
TeleMessage promotes the tool as a compliance solution designed to capture and store communications across platforms such as WhatsApp, SMS, Signal and more. These services appeal to sectors such as finance and government. However, this violation indicates that changing safe tools for compliance can lead to dangerous vulnerabilities, especially if the back-end system remains exposed.
Hackers reportedly accessed data from company signal clones and other modified apps, including Telegram, WhatsApp, and WeChat. Screenshots reviewed by 404 Media show references to US Customs and Border Protection, Coinbase, and other financial institutions.
Telemessage recently made a headline after using the app to mention it at a cabinet meeting with then-President Donald Trump. Waltz’s contacts on the platform included figures such as Marco Rubio, Tulsi Gabbard, and JD Vance. Hackers did not access these specific conversations, but the violation revealed that the archived chat was not end-to-end encrypted after capture.
This violation is more than just a dark eye for one technology vendor. This is a warning: it may just tweak a secure system for monitoring and break the protection that made it reliable in the first place.
🚀Want to share the story?
Submit your stories to TechStartUps.com in front of thousands of founders, investors, PE companies, tech executives, decision makers and tech leaders.
Please attract attention

