Cybersecurity researchers are warning of malicious campaigns targeting WordPress sites with malicious JavaScript injections designed to redirect users to sketchy sites.
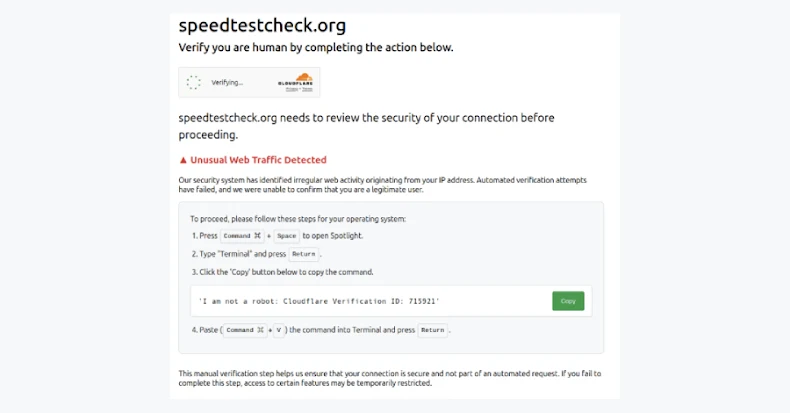
“Site visitors are injected with content that is drive-by malware, such as a fake Cloudflare verification,” Sucuri researcher Puja Srivastava said in an analysis published last week.
A website security company said it launched an investigation after one of its customer’s WordPress sites served suspicious third-party JavaScript to site visitors, ultimately finding that the attacker had made malicious changes to a theme-related file (‘functions.php’).
The code injected into “functions.php” includes a reference to Google Ads, presumably to evade detection. However, it actually acts as a remote loader by sending an HTTP POST request to the domain “brazilc”.[.]com’ then responds with a dynamic payload containing two components.
A JavaScript file hosted on a remote server (‘porsasystem'[.]com”) is referenced by 17 websites at the time of writing and contains code that performs site redirects. A piece of JavaScript code that creates a hidden 1×1 pixel iframe, including legitimate Cloudflare code such as “cdn-cgi/challenge-platform/scripts/jsd/main.js”, which is the core API of the bot detection and challenge platform. Insert code that mimics the asset.

The domain “porsasystem” is noteworthy.[.]com’ is flagged as part of a traffic distribution system (TDS) called Kongtuke (also known as 404 TDS, Chaya_002, LandUpdate808, and TAG-124).
According to information shared by an account named ‘monitorsg’ on Mastodon on September 19, 2025, the infection chain begins with a user visiting a compromised site, which results in the execution of ‘porsasystem’.[.]com/6m9x.js”, which then leads to “porsasystem”.[.]com/js.php,” which ultimately redirects the victim to a ClickFix-style page for malware distribution.

This finding points to the need to protect WordPress sites and keep plugins, themes, and website software up to date, to enforce strong passwords, to scan sites for anomalies, and to create unexpected administrator accounts to maintain persistent access even after malware is detected and removed.
Create a ClickFix page using the IUAM ClickFix Generator
The disclosure came as Palo Alto Networks’ Unit 42 detailed a phishing kit named IUAM ClickFix Generator that leverages ClickFix social engineering techniques to infect users with malware and allow attackers to come up with customizable landing pages that mimic browser verification challenges commonly used to block automated traffic.
“This tool allows attackers to create highly customizable phishing pages that mimic the challenge-response behavior of browser validation pages commonly deployed by content delivery networks (CDNs) and cloud security providers to protect against automated threats,” said security researcher Ammar Elsad. “The spoofed interface is designed to appear legitimate to the victim, increasing the effectiveness of the decoy.”

The custom-built phishing page also has the ability to manipulate the clipboard, a key step in a ClickFix attack, and detect the operating system used to adjust the infection sequence and deliver compatible malware.
In at least two different cases, threat actors have been detected using pages generated using kits that deploy information stealers, such as DeerStealer and Odyssey Stealer. Odyssey Stealer is designed to target Apple macOS systems.
The arrival of the IUAM ClickFix Generator further strengthens Microsoft’s advance warning that commercial ClickFix builders will be on the rise in underground forums starting in late 2024. Another notable example of a phishing kit that has integrated this product is Impact Solutions.
Microsoft said in August 2025, “These kits offer the creation of landing pages using a variety of available lures, including Cloudflare.[ファイル名を指定して実行]It also provides the construction of malicious commands to paste into dialogs. These kits claim to ensure payload persistence as well as bypassing antivirus and web protection (some even promise to bypass Microsoft Defender SmartScreen).
Needless to say, these tools further lower the barrier to entry for cybercriminals, allowing them to launch sophisticated multi-platform attacks at scale without requiring much effort or technical expertise.
ClickFix becomes stealthy through cache smuggling
The findings also follow the discovery of a new campaign that revamps the ClickFix attack method by staying under the radar and using a sneaky technique known as cache smuggling, rather than explicitly downloading malicious files to target hosts.
“This campaign differs from previous ClickFix variants in that the malicious script does not download files or communicate with the internet,” said Marcus Hutchins, lead threat researcher at Expel. “This is accomplished by preemptively storing arbitrary data on the user’s machine using the browser’s cache.”

In an attack documented by the cybersecurity firm, a ClickFix-themed page masquerades as the Fortinet VPN Compliance Checker and uses FileFix tactics to trick users into launching Windows File Explorer, pasting a malicious command into the address bar and triggering the execution of the payload.
Hidden commands are designed to run PowerShell scripts via conhost.exe. What makes this script unique is that it does not download any additional malware or communicate with attacker-controlled servers. Instead, an obfuscated payload is executed that is disguised as a JPEG image and is already cached by the browser when the user visits the phishing page.

“Neither web pages nor PowerShell scripts explicitly download files,” Hutchins explained. “By simply caching a fake ‘image’ in the browser, the malware can retrieve the entire zip file onto the local system without making a web request with a PowerShell command.”
“The implications of this technique are alarming, as cache smuggling can provide a way to bypass protections that detect malicious files when they are downloaded and executed. An innocent-looking “image/jpeg” file is simply downloaded, its contents extracted, and executed via PowerShell commands hidden in the ClickFix phishing lure. ”
Source link