Threat actors have been observed leveraging Google Tag Manager (GTM) to provide credit card skimmer malware targeting Magento-based e-commerce websites.
Website security company Sucuri says that this code looks like a typical GTM and Google Analytics script used for website analytics and advertising purposes, but is obfuscated, which can provide permanent access to attackers. It said that backdoors are included.
At the time of writing, three sites have been found to be infected with the GTM identifier in question (GTM-MLHK2N68), down from the six reported by Sucuri. A GTM identifier refers to a container that contains various tracking codes (such as Google Analytics, Facebook Pixel, etc.) and rules that are triggered when certain conditions are met.
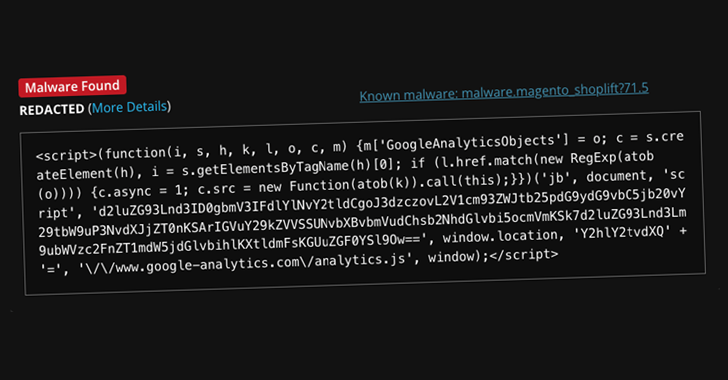
Further analysis reveals that the malware is loaded from the Magento database table “cms_block.content”, with the GTM tag containing an encoded JavaScript payload that acts as a credit card skimmer.

“The script is designed to collect sensitive data entered by users during the checkout process and send it to a remote server controlled by an attacker,” said security researcher Puja Srivastava. .

Once run, the malware is designed to steal credit card information from the checkout page and send it to an external server.
This is not the first time GTM has been abused for malicious purposes. In April 2018, Sucuri revealed that the tool was being used for fraud.
The development details another WordPress campaign where the company is likely to employ a vulnerability in a plugin or compromised administrator account and install malware that redirects site visitors to a malicious URL. It will take place a few weeks later.
Source link