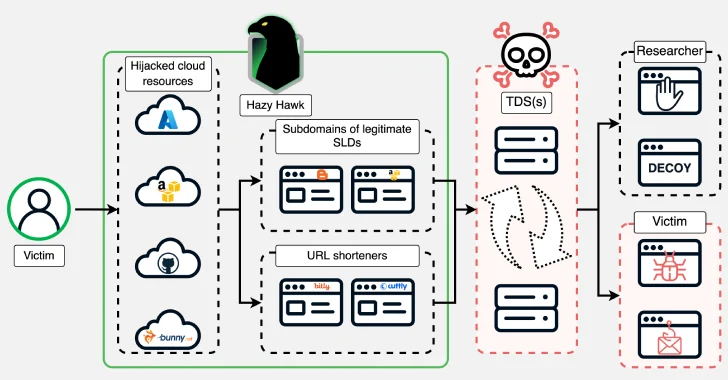
Threat actors known as Hazy Hawk have been observed hijacking abandoned cloud resources from well-known organizations, such as Amazon S3 buckets and Microsoft Azure endpoints, by leveraging false mining in domain name systems (DNS) records.
According to InfoBlox, hijacked domains are used to host URLs that users direct fraud and malware through their traffic delivery system (TDSES). Other resources taken away by threat actors include resources hosted on Akamai, Bunny CDN, CloudFlare CDN, GitHub, and Netlify.
The DNS threat intelligence company said it first discovered threat actors after gaining control of several subdomains associated with the Centers for Disease Control and Prevention (CDC) in February 2025.
Since then, other government agencies around the world, well-known universities, international companies such as Deloitte, PricewaterhouseCoopers and Ernst & Young have been determined to have been victimized by the same threat actors since at least December 2023.

“Arguably the most notable thing about Haze Hawk is that these difficult, vulnerable domains with connections to respected organizations are not used for spying or “high-brow” cybercrime,” said Jacques Portal and Renée Burton of Infoblox in a report shared with Hacker News.
“Instead, they feed the suspicious underworld of AdTech, whipping victims into a wide range of scams and fake applications, and using browser notifications to trigger a process that has long-lasting impact.”
What’s noteworthy about Hazy Hawk’s work is hijacking trustworthy and reputable domains belonging to legitimate organizations, so it increases the reliability of search results when used to provide malicious spam content. But even more worrying, this approach allows threat actors to bypass detection.
Supports the operation is the ability of an attacker to hang DNS CNAME records and seize control of abandoned domains. This is a technology previously exposed by Guardio in early 2024 as being exploited by bad actors for spam growth and click monetization. All that a threat actor needs to do is register the missing resources and hijack the domain.

Hazy Hawk goes a step further by finding abandoned cloud resources and directing them for malicious purposes. In some cases, threat actors employ URL redirection techniques to hide which cloud resources have been hijacked.
“We use the name hazy hawk for this actor to hang DNS CNAME records and find and hijack cloud resources to use in malicious URL distributions,” says Infoblox. “Domain hijacking components may be provided as a service and may be used by a group of actors.”
Attack chains often clone the contents of the legal site of the first site hosted in a hijacked domain, and invite the victim to visit with pornographic or pirated content. Visitors to the site then leak through TDS and decide where to land next.

“Hazy Hawk is one of dozens of threat actors to track in the world of ad affiliate marketing,” the company said. “Threat actors belonging to affiliate advertising programs are encouraged to include requests that drive users to tailored malicious content and allow push notifications from the “website” along the redirect path. ”
In doing so, the idea is to flood victims’ devices with push notifications and provide an endless torrent of malicious content. Each notification leads to various scams, scullyware, fake investigations, and involves requests to allow more push notifications.
To prevent and protect haze hawk activity, we recommend that you delete the DNS CNAME record as soon as resources are shut down. On the other hand, end users are encouraged to reject notification requests from unfamiliar websites.
“Operators like Hazy Hawk are responsible for the first lure, but the user who clicks is led into a roughly, malicious, malicious Adtech maze. Hayce Hawk has put a considerable amount of effort into identifying vulnerable domains and using them for fraudulent operations, indicating that these ad affiliate programs have been successful in paying well.
Source link