At least six South Korea’s organizations are being targeted by the prolific North Korean-related Lazarus group as part of a campaign called Operation Sink Hall.
The activity covers Korean software, IT, Financial, Semiconductor Manufacturing and Telecommunications Industries, according to a Kaspersky report published today. The first evidence of a compromise was first detected in November 2024.
The campaign included “a sophisticated combination of watering hole strategies and vulnerability exploitation within Korean software.” “A day vulnerability of the Innorix agent was also used for lateral movement.”
Attacks have been observed to pave the way for variations of known Lazarus tools such as Threatneedle, Agamemnon, Wagent, Signbt, and Copperhedge.

What makes these intrusions particularly effective is the high possibility of exploiting security vulnerabilities in Cross Ex, the common legal software in Korea.
“The Lazarus Group has a strong grasp of these details and uses a strategy targeting South Korea, combining vulnerabilities in such software with watering hole attacks,” said a Russian cybersecurity vendor.
The exploitation of security flaws for the lateral movement of Innorix agents is notable in the fact that similar approaches have been adopted in the past by Andariel subclusters of the Lazarus Group to provide malware such as Volgmer and Andardoor.
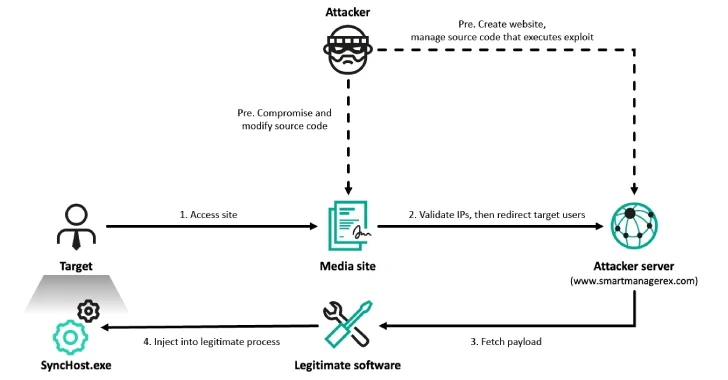
The starting point for the latest wave of attacks was the waterhole attack, which stimulated the deployment of the threat after the target visited various Korean online media sites. Visitors landing on a site are filtered using server-side scripts before redirecting to an adversary domain to provide malware.
“We will assess with moderate confidence that the redirected site can run malicious scripts and target potential cross-EX flaws installed on the target PC and launch malware,” the researcher said. “The script then eventually ran a legitimate Synchost.exe and injected shellcode that loads the threat variant into the process.”

It has been observed that infection sequences employ two phases using threats and shaking early stages, then employing signatures and copper hedges to establish sustainability, conduct reconnaissance, and provide qualification dumping tools to compromised hosts.
They have also deployed malware families such as LPeclient for victim profiling and payload delivery, as well as download devices called Agamemnon for downloading and running additional payloads received from command and control (C2) servers, but at the same time, they incorporate running security solutions into their bypass security solutions.

One of the payloads downloaded by Agamemnon is a tool designed to perform lateral movements by taking advantage of the security flaws of the Innorix Agent File Transfer Tool. Kaspersky said its investigation unearthed any additional files that download zero-day vulnerabilities in Innorix agents patched by the developer.
“The Lazaro Group’s specialist attacks targeting South Korean supply chains are expected to continue in the future,” Kaspersky said.
“Attackers are also trying to minimize detection by developing new malware and enhancing existing malware. In particular, they showcase the extensions to how C2 communicates, command structure, and how data is sent and received.”
Source link