Cybersecurity researchers are using phishing email to shed light on a new attack chain that offers an open source backdoor called VShell.
“Linux-specific malware infection chain starting with spam emails containing malicious RAR archive files,” Trellix researcher Sagar Bade said in a technical article.
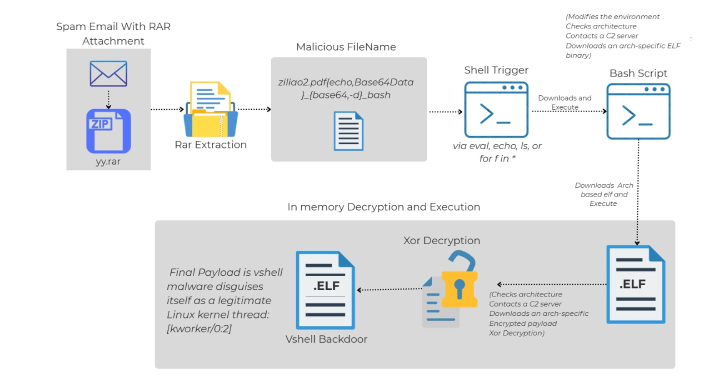
“The payload is not hidden within the file content or macros. It is encoded directly into the file name itself. By skillfully using shell command injection and Base64-encoded BASH payload, attackers turn simple file list operations into automatic malware execution triggers.”
The cybersecurity company added, exploiting the simple yet dangerous patterns commonly observed in shell scripts that occur when file names are evaluated with insufficient disinfection, causing trivial commands such as evaluations and echoes, making it easier to execute arbitrary code.

Additionally, this technique offers the additional advantage of avoiding traditional defenses as the antivirus engine does not scan the filenames normally.
The starting point of the attack is an email message that contains a RAR archive containing files containing malicious file names.
Specifically, the filename includes BASH compatible code designed to run commands when interpreted by the shell. It is worth noting that simply extracting a file from an archive does not trigger an execution. Rather, it only occurs when a shell script or command tries to parse a file name.
Another important aspect to consider here is that you cannot manually create file names with this syntax. This means that it could have been written using a different language or dropped using an external tool or script that bypasses shell input validation, Trellix said.
This leads to the execution of the embedded base64 encoding drawer, and gets the ELF binary of the appropriate system architecture (x86_64, i386, i686, armv7l, or aarch64) from the external server. The binary begins to communicate with the Command and Control (C2) server for that portion to retrieve the encrypted VShell payload, decoding and execution on the host.
According to Trellix, the fishing email is disguised as an invitation to a beauty product survey, and invites the winners to complete a financial reward (10 yuan).
“Importantly, the email contains a RAR archive attachment (‘YY.RAR’) despite not explicitly instructing the user to open or extract,” Bade explained. “The social engineering angle is subtle. Users are distracted by research content, and the presence of attachments can be mistaken for research-related documents or data files.”
VSHELL is a GO-based remote access tool that has been widely used by Chinese hacking groups in recent years, including UNC5174, reverse shell, UNC5174 that supports file operations, process management, port forwarding, and encrypted C2 communication.
What makes this attack dangerous is that the malware can work completely in-memory and target a wide range of Linux devices, not to mention avoiding disk-based detection.
“This analysis highlights the dangerous evolution of Linux malware delivery, where we weaponize simple file names embedded in RAR archives to allow arbitrary commands to be executed,” says Trellix. “Infection Chain leverages command injection in shell loops, abuses Linux’s tolerant execution environment, and ultimately provides powerful backdoor VShell malware that can control the system completely remotely.”

Picus Security is developing as it released a technical analysis called the Exploit Post-Exploit Tool, focused on Linux, leveraging the Linux kernel’s IO_URING framework to avoid traditional monitoring tools. It is currently unknown who is behind the malware.
“Instead of calling standard functions such as read, write, recv, send, and connect, RingReaper employs IO_URINGPRIMITIVES (e.g. IO_URING_PREP_*) to perform comparable operations asynchronously.” “This method helps bypass hook-based detection mechanisms and reduces the visibility of malicious activities in telemetry commonly collected by the EDR platform.”
RingReaper uses IO_URING to enumerate system processes, active pseudo-end (PTS) sessions, network connections, and logged in users, reducing footprint and avoiding detection. You can also collect user information from the “/etc/passwd” file, abuse SUID binaries for privilege escalation, and erase traces after execution.
“We leverage IO_IRING, the latest asynchronous I/O interface in the Linux kernel, to minimize reliance on traditional system calls that security tools frequently monitor or hook,” says Picus.
Source link