Microsoft has warned of a multi-stage adversary-in-the-middle (AitM) phishing and business email compromise (BEC) campaign targeting multiple organizations in the energy sector.
“The campaign exploited the SharePoint file sharing service to deliver a phishing payload and relied on creating inbox rules to maintain persistence and avoid user awareness,” the Microsoft Defender Security Research Team said. “The attack evolved into a series of AitM attacks and subsequent BEC activity across multiple organizations.”
As part of the post-exploit activity following the initial breach, unknown attackers have been observed leveraging trusted internal identities from victims to conduct large-scale phishing operations within and outside of organizations, casting a wide net and expanding the scope of their campaigns.
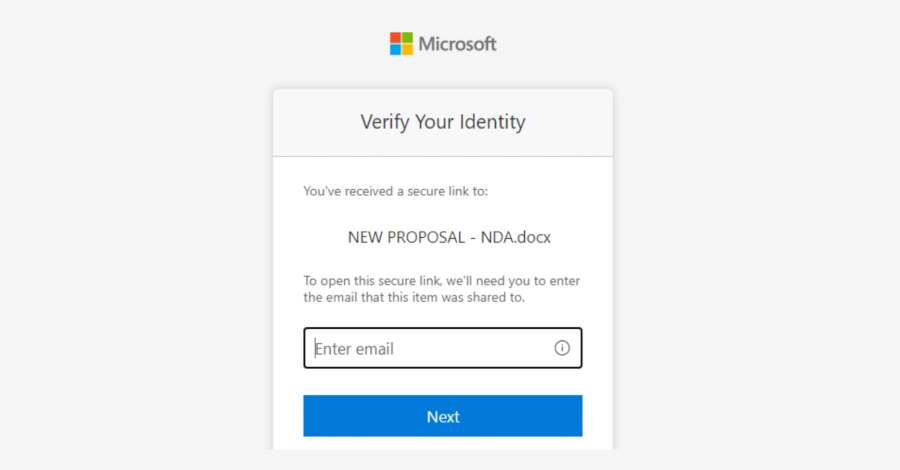
The attack started with a phishing email that appeared to come from an email address that belonged to a trusted organization and had previously been compromised. Attackers exploited this legitimate channel by sending messages disguised as SharePoint document sharing workflows to feign authenticity and trick recipients into clicking on the phishing URL.

Services like SharePoint and OneDrive are widely used in corporate environments, and the emails are sent from legitimate addresses, so they are less likely to arouse suspicion and allow attackers to deliver phishing links or stage malicious payloads. This approach is also known as Living Off Trusted Sites (LOTS), as it weaponizes the ease of use and ubiquity of such platforms to disrupt email-centric detection mechanisms.
This URL redirects the user to a fake credential prompt to view the document. Using the stolen credentials and session cookies, the attacker gains access to the account and creates an inbox rule that deletes all incoming emails and marks all emails as read. With this foundation in place, compromised inboxes can be used to send phishing messages containing fake URLs designed to perform credential theft using AitM attacks.
In one case, Microsoft said the attackers launched a large-scale phishing campaign that included more than 600 emails sent to the compromised user’s contacts inside and outside the organization. Attackers have also been observed deleting undelivered or out-of-office emails and taking steps to ensure the authenticity of emails if message recipients express concerns. The communication will then be deleted from your mailbox.

“These techniques are common to all BEC attacks and are intended to keep the victim unaware of the attacker’s actions, which can increase persistence,” the Windows maker said.
Microsoft said the attack highlights the “operational complexity” of AitM and said password resets alone cannot remediate the threat, as affected organizations must revoke active session cookies and remove inbox rules created by attackers that were used to evade detection.
To this end, the company said it has worked with customers to reverse multi-factor authentication (MFA) changes made by the attackers to the accounts of compromised users and remove questionable rules created on those accounts. At this time, it is unclear how many organizations were compromised or whether it was the work of known cybercrime groups.
We recommend that organizations work with their identity providers to ensure security controls are in place, such as phishing-resistant MFA, enable conditional access policies, implement continuous access assessments, and use anti-phishing solutions that monitor and scan incoming emails and visited websites.
The attack outlined by Microsoft highlights a continuing trend among attackers to stage malware by abusing trusted services such as Google Drive, Amazon Web Services (AWS), and Atlassian’s Confluence Wiki to redirect to credential harvesting sites. This eliminates the need for attackers to build their own infrastructure and makes malicious activity appear legitimate.
The disclosure comes after identity services provider Okta announced it had detected a custom phishing kit specifically designed for use in voice phishing (also known as vishing) campaigns targeting Google, Microsoft, Okta, and a wide range of cryptocurrency platforms. In these campaigns, attackers pose as technical support representatives and call potential targets using a spoofed support hotline or company phone number.
The goal of this attack is to trick users into visiting a malicious URL and handing over their credentials. Those credentials are then relayed to the attacker in real-time via the Telegram channel, allowing unauthorized access to the account. Social engineering efforts are carefully planned, with attackers scouting their targets and creating customized phishing pages.
Sold as a service, the kit includes client-side scripts that allow an attacker to control the authentication flow in real-time on a targeted user’s browser by providing verbal instructions and convincing them to perform an action that leads to MFA bypass, such as approving a push notification or entering a one-time password.
“These kits allow attackers to call a targeted user and control the authentication flow as that user interacts with a credential phishing page,” said Moussa Diallo, threat researcher at Okta Threat Intelligence. “An attacker can control the page that a target displays in their browser, fully synchronized with the instructions they provide during a call. Attackers can leverage this synchronization to defeat any form of MFA that is not phishing-resistant.”

In recent weeks, phishing campaigns have been exploiting basic authentication URLs (i.e. “username:password@domain”).[.]com”) in the username field followed by the @ symbol and the actual malicious domain to visually mislead the victim.
“When users see a URL that starts with a familiar and trusted domain, they are likely to assume that the link is legitimate and safe to click,” Netcraft said. “However, the browser interprets everything before the @ symbol as authentication credentials, not as part of the destination. The actual domain, or the domain to which the browser connects, is included after the @ symbol.”
Other campaigns rely on simple visual deception tricks, such as using “rn” instead of “m”, to hide malicious domains and trick victims into thinking they are visiting legitimate domains associated with companies such as Microsoft (“rnicrosoft”)[.]com”), MasterCard (“rnastercard[.]Marriott (Narriott Hotels)[.]com”), and Mitsubishi (“rnitbishielectric”)[.]com”). This is called a homoglyph attack.
“Though attackers often target brands that start with the letter M with this technique, some of the most convincing domains are obtained by swapping ‘m’ in words for ‘rn’ in words,” said Ivan Khamenka of Netcraft. “This technique becomes even more dangerous when it appears in words that organizations commonly use as part of their brand, subdomains, or service identifiers. Terms such as email, message, member, confirmation, and correspondence all contain the m in the middle word, which users rarely process.”
Source link