Cybersecurity researchers discovered a malware campaign deploying Amatera Stealer and NetSupport RATs using the now popular ClickFix social engineering tactic.
This activity observed this month is tracked by eSentire under the name EVALUSION.
First discovered in June 2025, Amatera is believed to be an evolution of ACR (short for “AcridRain”) Stealer, which was available in a malware-as-a-service (MaaS) model until malware sales ceased in mid-July 2024. Amatera is available through subscription plans ranging from $199 per month to $1,499 per year.
“Amatera provides threat actors with extensive data exfiltration capabilities across crypto wallets, browsers, messaging applications, FTP clients, and email services,” the Canadian cybersecurity vendor said. “Specifically, Amatera employs advanced evasion techniques such as WoW64 SysCalls to evade user-mode hooking mechanisms commonly used by sandboxes, antivirus solutions, and EDR products.”

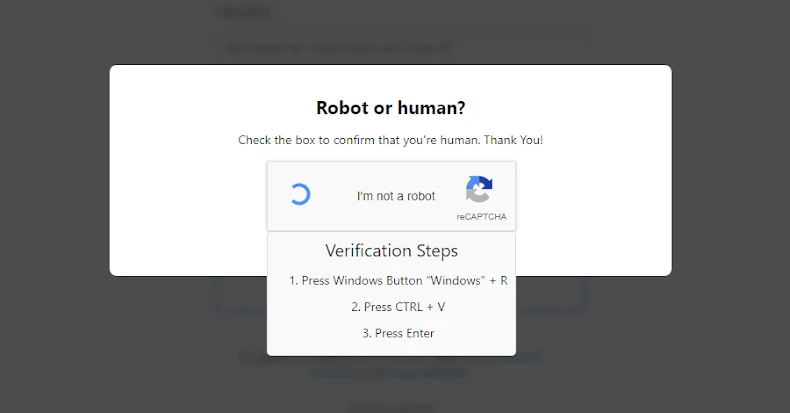
As is often the case with ClickFix attacks, users are tricked into using Windows[ファイル名を指定して実行]Use the dialog to execute malicious commands and complete reCAPTCHA validation checks on the fake phishing page. This command starts a multi-step process that uses the “mshta.exe” binary to launch a PowerShell script that downloads the .NET downloaded from the file hosting service MediaFire.
The payload is an Amatera Stealer DLL packed using PureCrypter. PureCrypter is a C#-based multifunctional crypter and loader that is also promoted as a MaaS product by a threat actor named PureCoder. The DLL is injected into the ‘MSBuild.exe’ process and the stealer then collects sensitive data, connects to an external server and executes PowerShell commands, and fetches and executes the NetSupport RAT.

“Of particular note in the PowerShell invoked by Amatera are checks to determine if the victim’s machine is part of a domain or has files of potential value (such as a crypto wallet),” eSentire said. “If neither is found, NetSupport will not be downloaded.”
This development coincides with the discovery of several phishing campaigns propagating various malware families.
A batch script that calls a PowerShell loader delivers an XWorm An email containing a Visual Basic Script attachment disguised as an invoice A compromised website with malicious JavaScript injected that redirects site visitors to a fake ClickFix page that mimics a Cloudflare Turnstile check ClickFix delivers a NetSupport RAT as part of an ongoing campaign codenamed SmartApeSG (also known as HANEYMANEY and ZPHP) Show fake CAPTCHA checks using lures and[ファイル名を指定して実行]Executes a malicious PowerShell command that drops a credential stealer when executed via a dialog. Emails that spoof internal “email delivery” notifications falsely claim to have blocked important messages related to unpaid invoices, package deliveries, and requests for quotation (RFQs) in order to trick recipients into clicking on a link that siphons login credentials under the pretext of moving the message to their inbox. Phishing kits named Cephas (first appeared in August 2024) and Tycoon 2FA are used to lure users to malicious login pages and steal their credentials.
“What makes Cephas notable is that it implements unique and unusual obfuscation techniques,” Barracuda said in an analysis published last week. “The kit hides the code by creating random invisible characters within the source code, evading anti-phishing scanners and preventing signature-based YARA rules from matching accurate phishing techniques.”
Source link