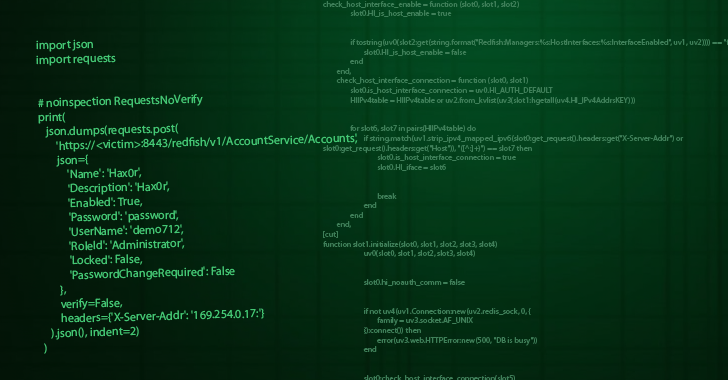
AMI’s Megarac Baseboard Management Controller (BMC) software reveals a critical security vulnerability that allows attackers to bypass authentication and take post-exposure actions.
The vulnerability tracked as CVE-2024-54085 is equipped with a CVSS V4 score of 10.0, indicating maximum severity.
“Local or remote attackers can take advantage of the vulnerability by accessing an internal host on a remote management interface (Redfish) or a BMC interface (Redfish),” firmware security company Eclypsium said in a report shared with Hacker News.
“By exploiting this vulnerability, an attacker can remotely control a compromised server, allowing malware, ransomware, firmware tampering, bridging motherboard components (BMC or potentially BIOS/UEFI), potential server physical damage (overvoltage/bricking), and victim reboot loops.
Additionally, vulnerabilities can be weaponized to phase out destructive attacks, and by sending malicious commands, sensitive devices will be rebooted continuously. This could pave the way for indefinite downtime until the device is reconfigured.

CVE-2024-54085 is the latest list of long list of security drawbacks discovered in Ami Megarac BMC since December 2022.

Eclypsium pointed out that CVE-2024-54085 is similar to CVE-2023-34329. The vulnerability has been found to affect the following devices:
HPE Cray XD670 ASUS RS720A-E11-RS24U ASROCKRACK
AMI has released a patch to address the defects as of March 11, 2025. There is no evidence that the issue has been exploited in the wild, but it is essential that downstream users update the system once OEM vendors incorporate these fixes and release them to customers.
“Please note that patching these vulnerabilities is a non-trivial exercise and requires downtime on the device,” Eclypsium said. “The vulnerability affects AMI’s BMC software stack only. However, since AMI is at the top of the BIOS supply chain, the downstream impact will affect 12 manufacturers.”
Source link