Weaponize new attack technologies to rope thousands of public domain controllers (DCs) around the world to create malicious botnets that use them to carry out power distributed denial of service (DDOS) attacks.
This approach is codenamed Win-Ddos by Safebreach Researchers or Yair and Shahak Morag.
“When investigating the complexity of Windows LDAP client code, we discovered a critical flaw that overwhelms the URL referral process on the victim server by manipulating the point DCS.”
“The result was that we were able to create Win-Dos, which allowed attackers to leverage the power of tens of thousands of public DCs around the world to create malicious botnets with enormous resources and upload rates.

When converting DCS to a DDOS bot without the need for code execution or credentials, the attack essentially transforms the Windows platform into both a victim and a weapon. The attack flow is as follows:
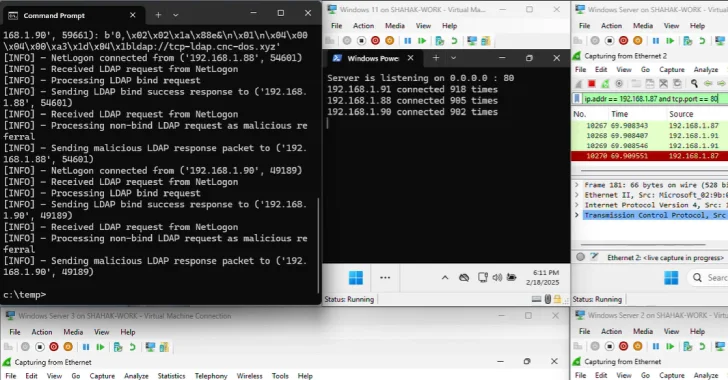
The attacker sends an RPC call to the DCS, triggering it to be a CLDAP client, and sending a CLDAP request to the attacker’s CLDAP server. This will return a referral response to the attacker’s LDAP server, switching from UDP to TCP DC, and sending it to the LDAP server attacker’s attacker. A referral response containing a long list of LDAP referral URLs. All of these can point to a single port of a single IP address DCS, send an LDAP query to that port, and close the TCP connection to a web server provided through the port

“When a TCP connection is aborted, DCS continues with the next introduction on the list, which again refers to the same server,” the researcher said. “And this behavior is repeated until all URLs in the referral list have finished, creating innovative Win-DDOS attack techniques.”
What makes win-dos important is that it has high bandwidth and no need for attackers to purchase a dedicated infrastructure. Also, you cannot fly under the radar as the device must be violated.
Further analysis of the LDAP client code referral process has revealed that it is possible to trigger an LSASS crash, restart, or blue screen (BSOD) by sending a long referral list to DCS, taking advantage of the fact that it is not freed from DC’s heap memory, by taking advantage of the fact that it is not freed from DC’s heap memory.
In addition to that, transport-independent code executed on server client requests has three new denial-of-service (DOS) vulnerabilities that could cause domain controllers to crash without requiring authentication, and an additional DOS flaw that provides authenticated users with the ability to crash domain controllers or Windows computers in their domains.

The identified drawbacks are listed below –
CVE-2025-26673 (CVSS score: 7.5) – Uncontrolled resource consumption of Windows LightWeight Directory Access Protocol (LDAP) allows unauthorized attackers to deny services on the network (fixed May 2025) CVE-2025-32724 (CVSS score: 7.5) Romantic attackers deny services over the network (fixed June 2025) CVE-2025-49716 (CVSS score: 7.5) – Windows Uncontrolled resource consumption in Netlogon allows rogue attackers to deny services on the network (fixed July 2025) CVE-2025-49722 Spooler component allows certified attackers to deny services on adjacent networks (fixed July 2025)
Similar to the vulnerability of Ldapnightmare (CVE-2024-49113), the latest findings detailed in early January of this year show that blind spots exist in windows that can be targeted, exploited and crippled business operations.
“The vulnerabilities we discovered are zero click-free vulnerabilities that allow attackers to crash these systems remotely when attackers are exposed, showing how attackers with minimal access to their internal networks can cause the same outcomes for private infrastructure,” the researchers said.
“Our findings break the general assumptions in enterprise threat modeling. DOS risks apply only to public services, and internal systems are safe from abuse unless they are fully compromised. The impact on enterprise resilience, risk modeling and defense strategies is important.”
Source link