Cybersecurity researchers are shedding light on a previously undocumented threat actor called Nighteagle (aka APT-Q-95), which has been observed to target Microsoft Exchange Servers as part of a zero-day exploit chain targeting China’s government, defense and technology sectors.
According to Qianxin’s Reddrip team, the threat actor has been active since 2023, switching network infrastructure at extremely fast speeds. The findings were presented at Cydes 2025, the third edition of Malaysia’s National Cyber Defense & Security Exhibition and Conference, which will be held from July 1st to 3rd, 2025.

“It looks like it’s running at night in China,” the cybersecurity vendor said, explaining the rationale behind nainasguru’s name.
The attacks mounted by threat actors achieved the main goal of single-outing entities operating in high-tech, chip semiconductors, quantum technology, artificial intelligence, and military verticals, and collecting intelligence.
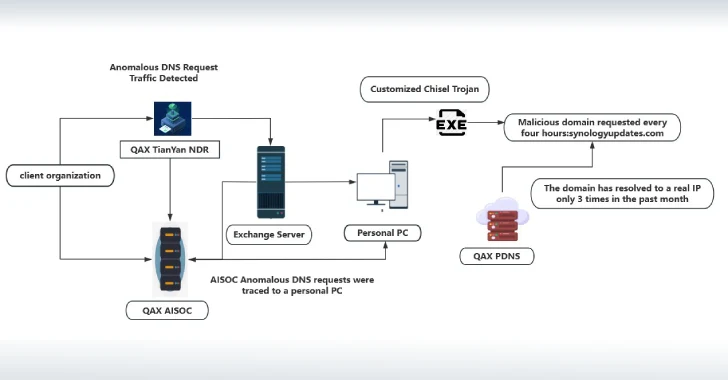
The company also noted that it began its investigation after discovering a bespoke version of the GO-based chisel utility, one of its customer endpoints configured to automatically start every four hours as part of a scheduled task.

“The attacker achieved the Intranet Penetration feature by modifying the source code of the open source Chisel Intranet Penetration tool, hard-coded execution parameters, using the specified username and password, establishing a sock connection with the 443 end of the specified C&C address, and mapping it to the specified port of the C&C host.

The Trojan is said to be delivered by a .NET loader, and it is embedded in the Internet Information Server (IIS) service on Microsoft Exchange Server. Further analysis determined the existence of zero-days that allow an attacker to obtain a MachineKey and gain unauthorized access to the Exchange server.
“The attacker could de-emphasize the Exchange server using the key, thereby porting the Trojan to a server that conforms to the Exchange version, allowing anyone to read mailbox data remotely,” the report states.
Qianxin argued that the activity was likely to be the work of threat actors from North America, given that the attack took place between 9pm and 6am Beijing time. The Hacker News reached out to Microsoft for further comment. I’ll update the story if I get a response.
Source link