Exposed PostgreSQL instances are the target of ongoing campaigns designed to gain unauthorized access and deploy cryptocurrency miners.
Cloud security company Wiz said the activity was a variant of the intrusion set initially flagged by Aqua Security in August 2024, including the use of a malware stock called PG_MEM. This campaign is attributed to the threatening actor Wiz track as Jinx-0126.
“Threatening actors can then evolve and implement defensive evasion techniques such as deploying binary with a unique hash for each target, and may avoid detection, such as running minor payloads fireless. [cloud workload protection platform] A solution that relies solely on the reputation of hash,” said researchers Avigayil Mechtinger, Yaara Shriki, and Gili Tikochinski.

Wiz also revealed that the campaign likely claims more than 1,500 victims to date.
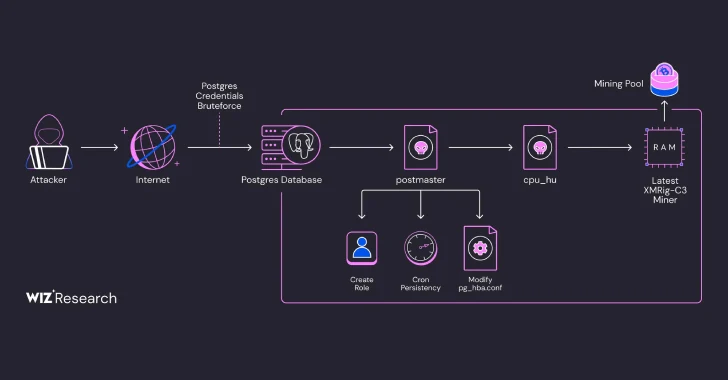
The most distinctive aspect of the campaign is the abuse of copying from a program SQL command that executes any shell command on the host.

The access gained by the successful exploitation of weakly configured PostgreSQL services is used to carry out pre-recon and drop Base64 encoded payloads. It’s actually a shell script that kills competing cryptocurrency miners and drops a binary named PG_Core.
Also downloaded to the server is a postmaster of an obfuscated Golang binary codename that mimics a legitimate PostgreSQL multi-user database server. It is designed to use Cron jobs to set up persistence on a host, increase privileges and create new roles, and write another binary called CPU_HU to disk.

CPU_HU downloads the latest version of Xmrig Miner from GitHub and downloads FILLESSLY via the known Linux Filless Technique called MEMFD.
“The threat actors assign unique mining workers to each victim,” Wiz said. “Each wallet had around 550 workers. In total, this suggests that the campaign could have leveraged over 1,500 compromised machines.”
Source link