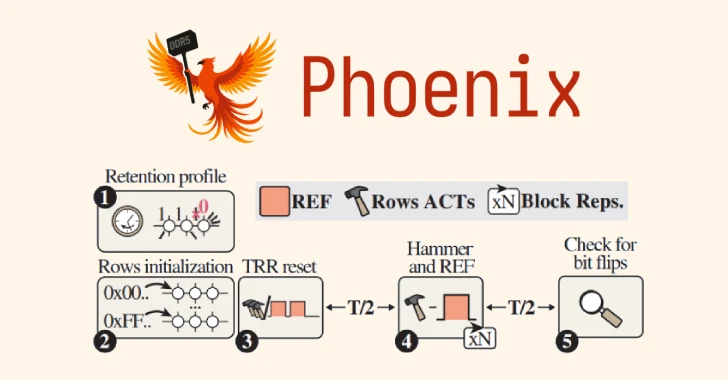
A team of scholars from EthZürich and Google have discovered a new variant of the Rowhammer attack targeting the double data rate 5 (DDR5) memory chips of Korean semiconductor vendor SK Hynix.
The Rowhammer Attack Variant, known as the codename Phoenix (CVE-2025-6202, CVSS score: 7.1), can bypass advanced protective mechanisms set up to resist attacks.
“We have proven that it is possible on a large scale to reliably trigger a Rowhammer bit flip on SK Hynix’s DDR5 devices,” EthZürich said. “We also proved that Die ECC won’t stop Rowhammer and that Rowhammer’s end-to-end attack is still possible in DDR5.”

Rowhammer refers to a hardware vulnerability because repeated accesses of a column of memory in a drum chip can trigger bit flips on adjacent rows. This can then be weaponized by bad actors, gaining unauthorized access to data, escalating privileges, or even denying services.
Although first demonstrated in 2014, future DRAM chips are susceptible to Rowhammer attacks as DRAM manufacturers rely on density scaling to increase DRAM capacity.
A study published by researchers EthZürich in 2020 found that “new DRAM chips are more vulnerable to Rowhammer. As device feature size decreases, the number of activations required to induce Rowhammer bit flips also decreases.”
Further studies of subjects have demonstrated that vulnerability has several dimensions and is sensitive to several variables, including environmental conditions (temperature and voltage), process variation, stored data patterns, memory access patterns, and memory control policies.
Major mitigations for Rowhammer attacks include error correction codes (ECC) and target row updates (TRR). However, these measures have proven ineffective against more sophisticated attacks such as Trespass, Smash, Half-Double, and Blacksmith.
The latest findings from EthZürich and Google show that bypass advanced TRR defenses on DDR5 memory and that researchers can open the door for what is called “the first Rowhammer privilege escalation exploit in a standard production-grade desktop system with DDR5 memory.”
In other words, the final result is a privileged escalation exploit that gets the route of a DDR5 system with default settings in just 109 seconds. Specifically, this attack takes advantage of the fact that it does not sample a specific update interval to flip bits across all 15 DDR5 memory chips in the test pool generated between 2021 and 2024.
Potential exploitation scenarios involving these bit-flips allow you to target RSA-2048 keys in co-located virtual machines to break SSH authentication, and use SUDO binaries to escalate local privileges to the root user.

“The inability to update wild DRAM devices will remain vulnerable for years,” the researchers said. “We recommend tripling the refresh rate, which has stopped Phoenix from triggering bit flips in the test system.”
The disclosure comes weeks after researchers from George Mason University and Georgia Tech detailed two different Rowhammer attacks, called OneFlip and ECC.Fail, respectively.
OneFlip revolves around triggering one bitflip to change weights in a deep neural network (DNN) model and activating unintended behavior, while ECC.Fail is described as the first end-to-end Rowhammer attack valid for DDR4 server machines with ECC memory.
“Unlike the counterparts on a PC, the server has additional protection against corrupted memory data (e.g., Rowhammer or Cosmic Ray Bit Flips) in the form of errors that fix the code,” the researchers said. “They can detect bit flips in memory and even potentially correct them. ECC.FAIL bypasses these protections by carefully guiding Rowhammer bit flips at specific memory locations.”
Source link