Cybersecurity researchers have escaping container isolation protection and bypassing current patched security vulnerabilities in the Nvidia Container Toolkit that could be leveraged to gain full access to the underlying host. I discovered it.
The new vulnerability is tracked as CVE-2025-23359 (CVSS score: 8.3). It affects the next version –
nvidia Container Toolkit (all versions up to 1.17.3) – Fixed in version 1.17.4 NVIDIA GPU operator (all versions up to 24.9.1) – Fixed in version 24.9.2

“The Nvidia Container Toolkit for Linux contains a vulnerability for time used (Toctou) when used in the default configuration. This means that crafted container images access the host file system It could be possible,” the company said in its advisory. Tuesday.
“Successful use of this vulnerability could lead to code execution, denial of service, escalation of privileges, disclosure of information, and data tampering.”
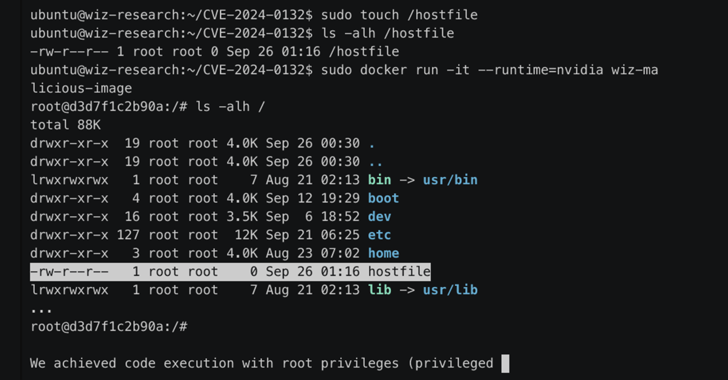
Wiz, a cloud security company that shared additional technical details of the flaw, said it was bypassing another vulnerability (CVE-2024-0132, CVSS score: 9.0) addressed by NVIDIA in September 2024 Ta.
In short, the vulnerability allows bad actors to mount the host’s root file system in a container, allowing free access to all files. Additionally, access can be used to launch privileged containers and achieve full host compromises through runtime UNIX sockets.
Wiz Researchers’ security researchers Shir Tamari, Ronen Shustin, and Andres Riancho said in the source code analysis of the container toolkit, the file path used during the mount operation is symbolic to allow the file path to be mounted from outside the container. I discovered that I can use links to manipulate it. (i.e., the root directory) to the path in “/usr/lib64”.

Access to the host filesystem provided by container escape is read-only, but this restriction can be avoided by interacting with UNIX sockets to generate a new privileged container and gaining unlimited access to the filesystem.
“This level of access also allowed us to monitor network traffic, debug active processes and perform a variety of other host-level operations,” the researchers said.
In addition to updating to the latest version, NVIDIA Container Toolkit users are advised not to disable the “-No-CNTLIBS” flag in their production environment.
Source link