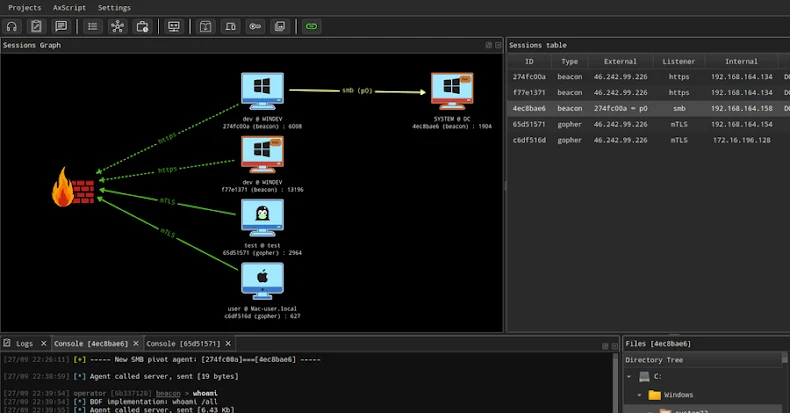
The open-source command and control (C2) framework known as AdaptixC2 is being used by a growing number of threat actors, some of which are associated with Russian ransomware gangs.
AdaptixC2 is an extensible post-exploitation and adversarial emulation framework designed for penetration testing. The server component is written in Golang, while the GUI client is written in C++ QT for cross-platform compatibility.
It comes with a wide range of features, including fully encrypted communications, command execution, a credential and screenshot manager, and a remote terminal. An earlier iteration was publicly released in August 2024 by a GitHub user named “RalfHacker” (@HackerRalf on X). This user describes himself as a penetration tester, red team operator, and “MalDev” (short for malware developer).

In recent months, AdaptixC2 has been employed by various hacking groups, including threat actors associated with the Fog and Akira ransomware operations, as well as early access brokers that leveraged CountLoader in attacks aimed at providing a variety of post-exploitation tools.
Palo Alto Networks’ Unit 42, which analyzed the technical aspects of the framework last month, characterized it as a modular and versatile framework that can be used to “give comprehensive control over affected machines,” and as part of a fake help desk support phone scam via Microsoft Teams and PowerShell scripts generated with artificial intelligence (AI).
Although AdaptixC2 is presented as an ethical open source tool for red teaming, it has clearly attracted the attention of cybercriminals.
Cybersecurity firm Silent Push said RalfHacker’s GitHub profile as “MalDev” sparked an investigation that led to the discovery of several GitHub account email addresses linked to the account owner, as well as a Telegram channel called RalfHackerChannel, where messages posted to AdaptixC2’s dedicated channel were reshared. The RalfHackerChannel channel has over 28,000 subscribers.

In a message on the AdaptixFramework channel in August 2024, they said they were interested in starting a project around “Public C2, which is very trendy right now,” and hoped to “be like Empire,” another popular post-exploitation and adversarial emulation framework.
While it is unclear at this stage whether RalfHacker is directly involved in malicious activity related to AdaptixC2 or CountLoader, Silent Push said their “connections to the Russian criminal underworld through their use of Telegram for marketing purposes and the subsequent increased use of the tool by Russian threat actors all raise significant red flags.”
Hacker News has reached out to RalfHacker for comment. I will update the article if I receive a response.
Source link