Cybersecurity researchers are warning about new campaigns that are leveraging variants of FileFix social engineering tactics to provide STEALC information steeler malware.
“The observed campaign uses highly compelling multilingual phishing sites (e.g., fake Facebook security pages) and avoid detection with anti-analytics technology and advanced obfuscation,” Acronis security researcher Eliad Kimhy said in a report shared with Hacker News.
At high levels, the attack chain uses FileFix to seduce users to launch the initial payload and download seemingly harmless images containing malicious components from the BitBucket repository. This allows attackers to bypass detection by abusing the trust associated with legitimate source code hosting platforms.
FileFix is a bit different from Clickfix, as it was first documented as a proof of concept (POC) by security researcher MRD0X in June 2025. This avoids the need to launch the Windows Run dialog and paste the already copied OBFuscated command to complete the Bogs Captcha verification check on the polished page set for this purpose.

Instead, it leverages the file upload feature of a web browser to deceive users, copy and paste copies into the File Explorer address bar, and runs locally on the victim’s machine.
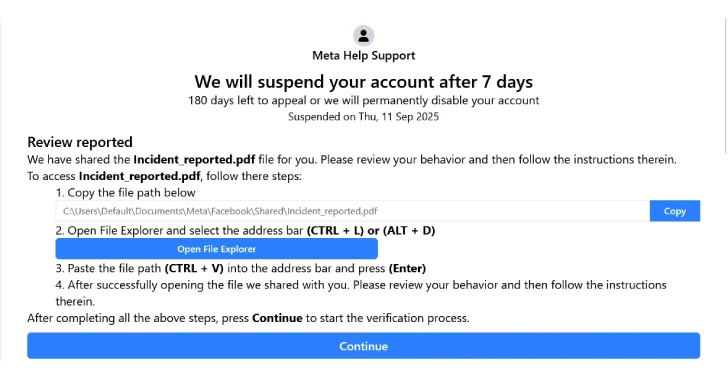
The attack begins on a phishing site where victims are likely to be redirected from an email message warning recipients about potential suspensions of their Facebook accounts a week later, claiming that the shared post or message violates the policy. Users are then asked to click on a button to appeal to the decision.
Not only is phishing pages obfuscated in large quantities, they also rely on techniques such as junk code and fragmentation, which hinders analysis efforts.
File fix attacks take effect when you click the button. At this point you will see a message that you can copy and paste the path to the document in the File Explorer address bar to access the expected policy violation PDF version.
The path provided in the order looks completely harmless,[コピー]When you click the button, it actually copies malicious commands with extra spaces, so when you open it using the Open File Explorer button, only the file path will be displayed when pasted into File Explorer.
This command is a multi-stage PowerShell script that downloads the aforementioned image and decodes it into the next stage payload, and runs a GO-based loader that unpacks the shellcode responsible for launching STEALC.
FileFix also offers an important advantage over ClickFix. This could potentially block system administrators as security majors[Runダイアログ(またはAppleMacOSの場合のターミナルアプリ)を開くのではなく、広く使用されているブラウザー機能を乱用するためです。
「一方、Clickfixをそもそも検出するのが非常に難しいことの1つは、実行ダイアログを介してExplorer.exeから、または端末から直接生み出されることです。
「この攻撃の背後にある敵は、貿易財産への多大な投資を示し、フィッシングインフラストラクチャ、ペイロード配信、およびサポート要素を慎重に工学的に設計して、回避と衝撃の両方を最大化しました。」
この開示は、Doppelが偽のサポートポータル、CloudFlare Captchaエラーページ、クリップボードハイジャック(つまり、Clickfix)の組み合わせを使用して、Autohotkey(AHK)をダウンロードして実行する悪意のあるPowerShellコードを実行するために、Clipboard Hijacking(Ie、Clickfix)を使用して別のキャンペーンを詳述したことに伴います。

このスクリプトは、侵害されたホストをプロファイルし、AnyDesk、TeamViewer、Information Stealers、Clipper Malwareなどの追加のペイロードを提供するように設計されています。
サイバーセキュリティ会社は、犠牲者が見た目のようなGoogleドメインを指すMSHTAコマンドを実行するように導かれる活動の他のバリアントも観察したと述べました( “wl.google-587262[.]com”), retrieve and run a remote malicious script.
“AHK is a Windows-based scripting language originally designed to automate repetitive tasks such as keystrokes and mouse clicks,” said Aarsh Jawa, security researcher at Doppel.
“Though it has long been popular among power users and system administrators because of its simplicity and flexibility, threat actors began to create lightweight malware droppers and information steelers using AHK as weapons around 2019. These malicious scripts often pose as benign automation tools or support utilities.”
Source link